2015-09-16 - NEUTRINO EK FROM 89.38.149[.]168 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-16-Neutrino-EK-sends-CryptoWall-3.0--ransomware-traffic.pcap.zip
- 2015-09-16-Neutrino-EK-and-CryptoWall-3.0-ransomware-files.zip
NOTES:
- Bitcoin address for this CryptoWall 3.0 ransomware sample's ransom payment was: 12DEX1ynovnDVwXJ55hkVWQdE8E7gVFHQk
TRAFFIC
ASSOCIATED DOMAINS:
- 89.38.149[.]168 port 11242 - vhwlbv.tefgroup[.]xyz - Neutrino EK
- ip-addr[.]es - IP address check by CryptoWall 3.0 ransomware
- 184.168.19.1 port 80 - hurt911morrow[.]com - Callback traffic from CryptoWall 3.0 ransomware
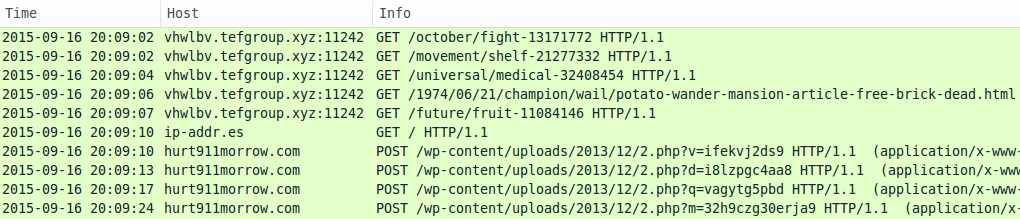
NEUTRINO EK:
- 2015-09-16 20:09:02 UTC - vhwlbv.tefgroup[.]xyz:11242 - GET /october/fight-13171772
- 2015-09-16 20:09:02 UTC - vhwlbv.tefgroup[.]xyz:11242 - GET /movement/shelf-21277332
- 2015-09-16 20:09:04 UTC - vhwlbv.tefgroup[.]xyz:11242 - GET /universal/medical-32408454
- 2015-09-16 20:09:06 UTC - vhwlbv.tefgroup[.]xyz:11242 - GET /1974/06/21/champion/wail/potato-wander-mansion-article-free-brick-dead.html
- 2015-09-16 20:09:07 UTC - vhwlbv.tefgroup[.]xyz:11242 - GET /future/fruit-11084146
POST-INFECTION TRAFFIC CAUSED BY THE CRYPTOWALL 3.0 PAYLOAD:
- 2015-09-16 20:09:10 UTC - ip-addr[.]es - GET /
- 2015-09-16 20:09:10 UTC - hurt911morrow[.]com - POST /wp-content/uploads/2013/12/2.php?v=ifekvj2ds9
- 2015-09-16 20:09:13 UTC - hurt911morrow[.]com - POST /wp-content/uploads/2013/12/2.php?d=i8lzpgc4aa8
- 2015-09-16 20:09:17 UTC - hurt911morrow[.]com - POST /wp-content/uploads/2013/12/2.php?q=vagytg5pbd
- 2015-09-16 20:09:24 UTC - hurt911morrow[.]com - POST /wp-content/uploads/2013/12/2.php?m=32h9czg30erja9
Click here to return to the main page.
