2015-09-23 - BARTALEX MALSPAM SENDS PONY AND VAWTRAK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-23-bartalex-word-macro-sends-pony-and-vawtrak.pcap.zip
- 2015-09-23-bartalex-word-macro-sends-pony-and-vawtrak.zip
NOTES:
- I wrote about Bartalex malicious spam (malspam) back in July 2015: https://isc.sans.edu/diary/Bartalex+malspam+pushing+PonyDyre/19947
- I still find Bartalex malspam every once in a while. Apparently, it's "still a thing."
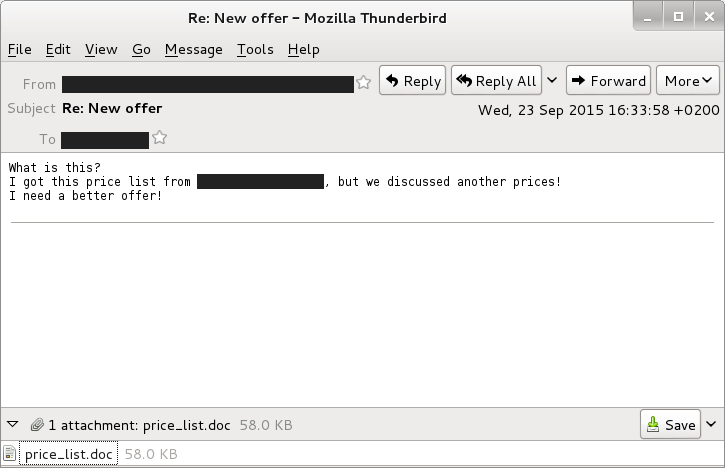
EXAMPLE OF THE MALSPAM
SCREEN SHOT OF THE MALSPAM:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.168.47[.]225 port 80 - ssgc[.]co - Traffic caused by Bartalex Word macro
- 184.168.47[.]225 port 80 - glovestix[.]com - Bartalex Word macro downloading Pony
- 77.246.150[.]56 port 80 - rindititred[.]ru - Pony check-in
- 69.49.225[.]132 port 80 - worldhealthsupply[.]com - Pony downloading Vawtrak
- 144.76.144[.]29 port 80 - errors-seeds[.]cz - Pony downloading Vawtrak
- 185.66.10[.]57 port 80 - ninthclub[.]com - Vawtrack post-infection traffic
- 185.66.10[.]57 port 80 - 185.66.10[.]57 - Vawtrack post-infection traffic
INFECTION TRAFFIC:
- 2015-09-23 20:02:28 UTC - ssgc[.]co - GET /wp-content/uploads/cache/remote/www-abc-net-au/5716367236.txt
- 2015-09-23 20:02:29 UTC - ssgc[.]co - GET /wp-content/uploads/cache/remote/www-abc-net-au/5716367236.txt
- 2015-09-23 20:02:29 UTC - ssgc[.]co - GET /wp-content/uploads/cache/remote/www-abc-net-au/pipi.txt
- 2015-09-23 20:02:33 UTC - glovestix[.]com - GET /wp-content/plugins/woocommerce-subscriptions/lib/action-scheduler/tests/phpunit/jobstore/s1.exe
- 2015-09-23 20:03:06 UTC - rindititred[.]ru - POST /gate.php HTTP/1.0
- 2015-09-23 20:03:06 UTC - worldhealthsupply[.]com - GET /system/logs/k1.exe HTTP/1.0
- 2015-09-23 20:03:07 UTC - errors-seeds[.]cz - GET /system/logs/k1.exe HTTP/1.0
- 2015-09-23 20:05:43 UTC - ninthclub[.]com - POST /Work/new/index.php
- 2015-09-23 20:05:43 UTC - ninthclub[.]com - POST /Work/new/index.php
- 2015-09-23 20:05:44 UTC - 185.66.10[.]57 - GET /module/221680f17a95443c798c701eff36cbe6
- 2015-09-23 20:05:45 UTC - 185.66.10[.]57 - GET /module/4c06c7a4c2bc6fb51cd998e9bbcf5846
- 2015-09-23 20:05:46 UTC - ninthclub[.]com - POST /Work/new/index.php
- 2015-09-23 20:05:46 UTC - 185.66.10[.]57 - GET /module/9f3359a7b12ceea791a4afc21a971152
- 2015-09-23 20:05:48 UTC - ninthclub[.]com - POST /Work/new/index.php
- 2015-09-23 20:05:53 UTC - ninthclub[.]com - POST /Work/new/index.php
- 2015-09-23 20:08:21 UTC - ninthclub[.]com - POST /Work/new/index.php
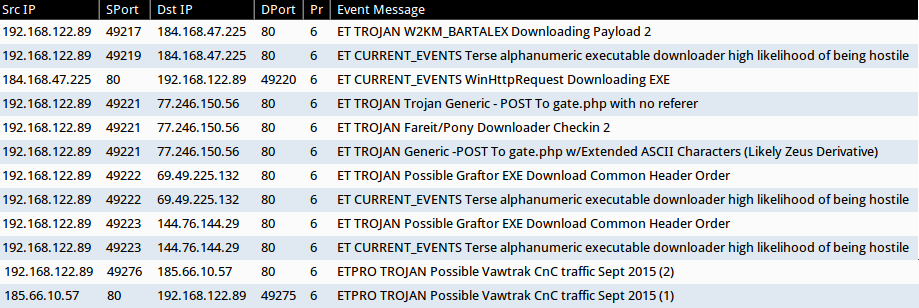
SNORT EVENTS
Some of the signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion:
PRELIMINARY MALWARE ANALYSIS
WORD DOCUMENT (ATTACHMENT FROM THE MALSPAM):
File name: price_list.doc
File size: 59,392 bytes
MD5 hash: facec082a3cffddc43e668a3080487f5
SHA1 hash: 7888f662d9b16b480f5e65bdbdbf4e94e1afbe4a
SHA256 hash: 120d5320a59a86f9b3e0774609a3f0773d76a7d66689525a023bee7f8666f2eb
Detection ratio: 7 / 56
First submission: 2015-09-23 14:10:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/120d5320a59a86f9b3e0774609a3f0773d76a7d66689525a023bee7f8666f2eb/analysis/
PONY (DOWNLOADED BY THE WORD DOCUMENT):
File name: s1.exe
File size: 251,392 bytes
MD5 hash: 6740944268a22221d0068dc44980dfcb
SHA1 hash: 3f2f3d1956c78a86062b367d298a154e4d755487
SHA256 hash: c1afb96d2a3b436444313fde02d103ff86f9b68d7e2ca3151b64cb7caa3696cd
Detection ratio: 0 / 56
First submission: 2015-09-23 14:15:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/c1afb96d2a3b436444313fde02d103ff86f9b68d7e2ca3151b64cb7caa3696cd/analysis/
VAWTRAK (DOWNLOADED BY THE PONY MALWARE):
File name: k1.exe
File size: 336,896 bytes
MD5 hash: 9f2273b3ff941ecebe9b04b7ce0a88a6
SHA1 hash: ddc86574dda8f072aeceaf48f01507f7095ded50
SHA256 hash: 4d47396e1e9c7538c59da8b5574fb8f208154cdfc6590e33b74b7e9feada7584
Detection ratio: 2 / 56
First submission: 2015-09-23 14:18:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/4d47396e1e9c7538c59da8b5574fb8f208154cdfc6590e33b74b7e9feada7584/analysis/
Click here to return to the main page.