2015-10-13 - ANGLER EK FROM 188.138.105[.]137 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-13-Angler-EK-sends-CryptoWall-3.0-traffic-ransomware.pcap.zip 887.1 kB (887,050 bytes)
- 2015-10-13-Angler-EK-and-CryptoWall-3.0-ransomware-files.zip 261.7 kB (261,651 bytes)
NOTES:
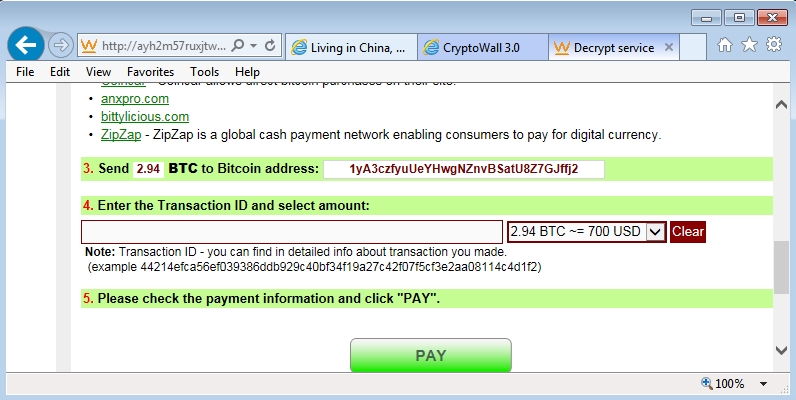
- Bitcoin address for this CryptoWall 3.0 ransomware sample's ransom payment was: 1yA3czfyuUeYHwgNZnvBSatU8Z7GJffj2
CHAIN OF EVENTS
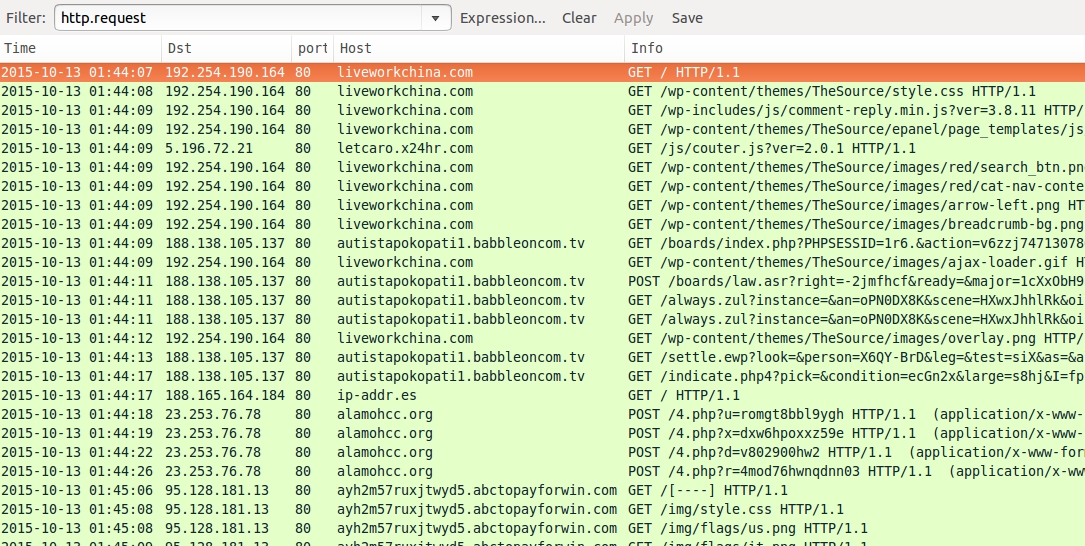
ASSOCIATED DOMAINS:
- liveworkchina[.]com - Compromised website
- 5.196.72[.]21 port 80 - letcaro.x24hr[.]com - Redirect/gate
- 188.138.105[.]137 port 80 - autistapokopati1.babbleoncom.tv - Angler EK
- ip-addr[.]es - IP address check by the malware
- 23.253.76[.]78 port 80 - alamohcc.org - CryptoWall 3.0 ransomware check-in
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.abctopayforwin[.]com - User checking the decrypt instructions
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - User checking the decrypt instructions
- ayh2m57ruxjtwyd5.deballmoneypool[.]com - Domain for decrypt instructions that didn't resolve in DNS
- 109.70.26[.]37 port 80 - ayh2m57ruxjtwyd5.armnsoptionpay[.]com - Another domain for decrypt instructions, went to Russian page saying domain was unavailable
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT:
- SHA256 hash: e47f0a2dfddc047d36342f54253d6e9a7c2c8799f1522eca6f1741bd03d0add7 - File size: 42.3 KB ( 43,290 bytes ) (Virus Total link)
ANGLER EK MALWARE PAYLOAD (CRYPTOWALL 3.0 RANSOMWARE):
- SHA256 hash: ef571c90c4fa41982d77a7d443e5232c8a31487fe2a449ba17240a230b148549 - File size: 245.8 KB ( 245,786 bytes ) (Virus Total link)
Click here to return to the main page.