2015-10-13 - NEUTRINO EK FROM 81.2.241[.]147
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-13-Neutrino-EK-traffic-2-pcaps.zip 623.6 kB (623,635 bytes)
- 2015-10-13-Neutrino-EK-malware-and-artifacts.zip 226.4 kB (226,373 bytes)
CHAIN OF EVENTS
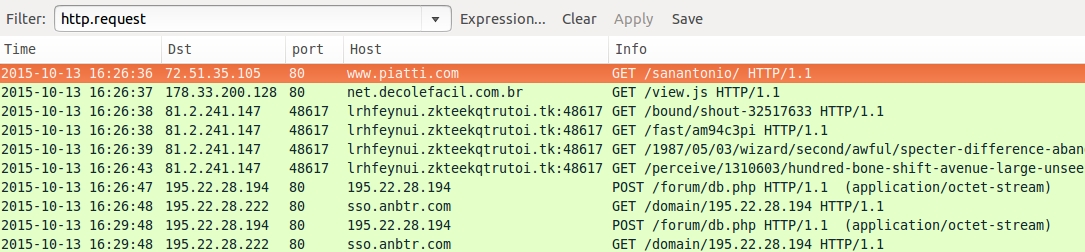
Shown above: HTTP requests from the first run.

Shown above: HTTP requests from the second run.
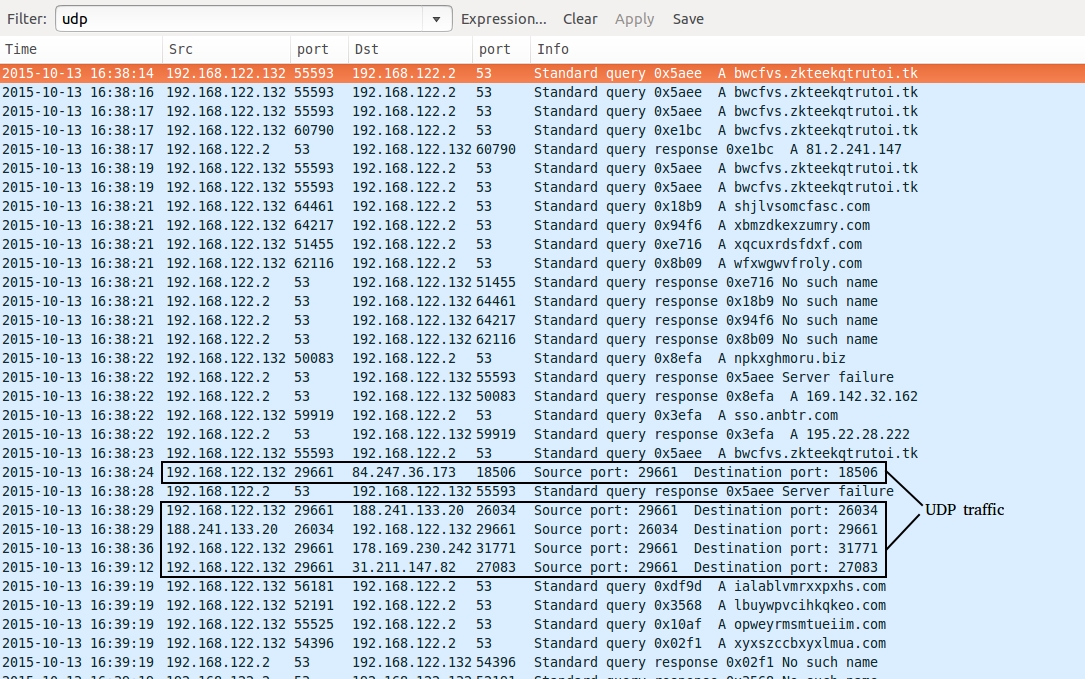
Shown above: UDP traffic from the second run (also shows some of the DGA domains requested).
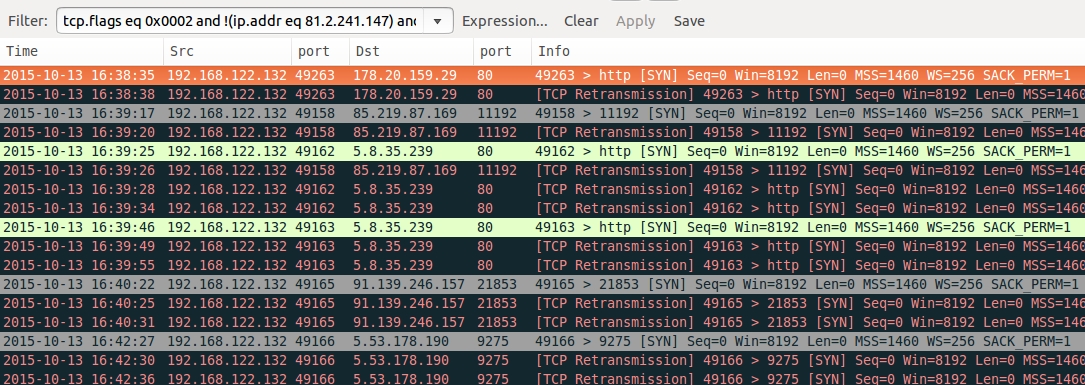
Shown above: TCP connections from the infected host during the second run.
ASSOCIATED DOMAINS:
- www.piatti[.]com - Compromised website
- 178.33.200[.]128 port 80 - net.decolefacil.com.br - Redirect (gate)
- 81.2.241[.]147 port 10771 - icbvir.zkteekqtrutoi[.]tk - Neutrino EK (first run)
- 81.2.241[.]147 port 29391 - bwcfvs.zkteekqtrutoi[.]tk - Neutrino EK (second run)
- 81.2.241[.]147 port 48617 - lrhfeynui.zkteekqtrutoi[.]tk - Neutrino EK (second run)
- 195.22.28[.]194 port 80 - 195.22.28[.]194 - Post-infection traffic
- sso.anbtr[.]com - Post-infection traffic
- 178.20.159[.]29 port 80 - 178.20.159[.]29 - Post-infection traffic
- 107.181.187[.]200 port 80 - 107.181.187[.]200 - Post-infection traffic
- various IPs various ports - UDP and TCP traffic (see pcaps for details)
PRELIMINARY MALWARE ANALYSIS
NEUTRINO EK FLASH EXPLOIT:
- SHA256 hash: 95ac87429064060009522bb777ec21caafc073797a3b1880759205bf57f65653 - File size: 87.5 KB (89,590 bytes) (Virus Total link)
MALWARE RETRIEVED FROM THE INFECTED HOST:
- C:\Windows\Installer\{E592F560-0ACD-78DD-8A96-2D396A5A4072}\syshost.exe (Virus Total link) - NOTE: This is where the Neutrino EK payload copied itself.
- C:\Windows\System32\Drivers\d839b6ab329a8dc8.sys (Virus Total link)
- C:\Windows\Temp\UDDB730.tmp (NOTE: This is same file as d839b6ab329a8dc8.sys.)
REGISTRY KEYS ASSOCIATED WITH THIS INFECTION:
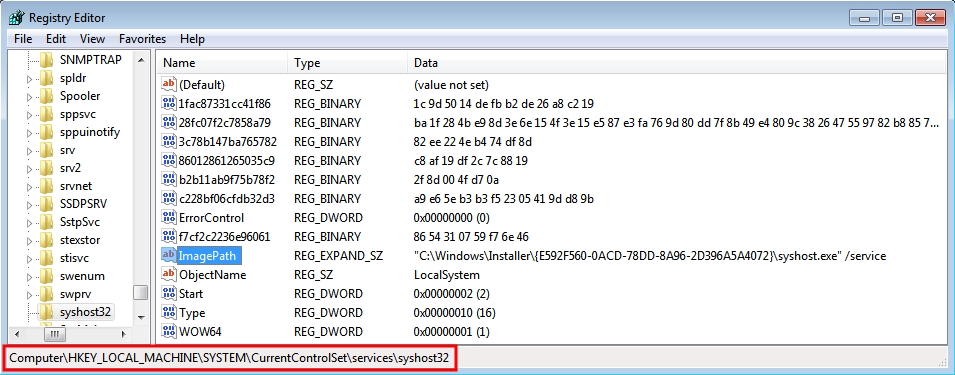
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\syshost32
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\services\syshost32
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\syshost32
VALUES FOR ALL THE ABOVE REGISTRY KEYS:
- Value name: ImagePath
- Value type: REG_EXPAND_SZ
- Value data: "C:\Windows\Installer\{E592F560-0ACD-78DD-8A96-2D396A5A4072}\syshost.exe" /service
Click here to return to the main page.
