2015-11-06 - TRAFFIC ANALYSIS EXERCISE - ANSWERS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
- The notes here discuss Malwr.com, but that site has been off-line since sometime in 2020. Also, the Hybrid-Analysis.com links were not working when I checked.
ASSOCIATED FILES:
- Zip archive of the pcap: 2015-11-06-traffic-analysis-exercise.pcap.zip 5.2 MB (5,211,550 bytes)
- Zip archive of the emails: 2015-11-06-traffic-analysis-exercise-emails.zip 104.1 kB (104,127 bytes)
NOTES:
- Thanks to those who've posted their own write-ups for this exercise on-line. They provide additional details that I didn't go into for my answers on this page.
ANSWERS
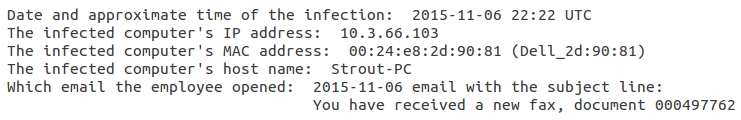
DETAILS
In order to figure out which email the user infected his or her computer with, you'll want to look at the infection traffic first. Make sure you've set up Wireshark as shown here and open the pcap. Filter on http.request to get an idea of traffic seen from the infected host.
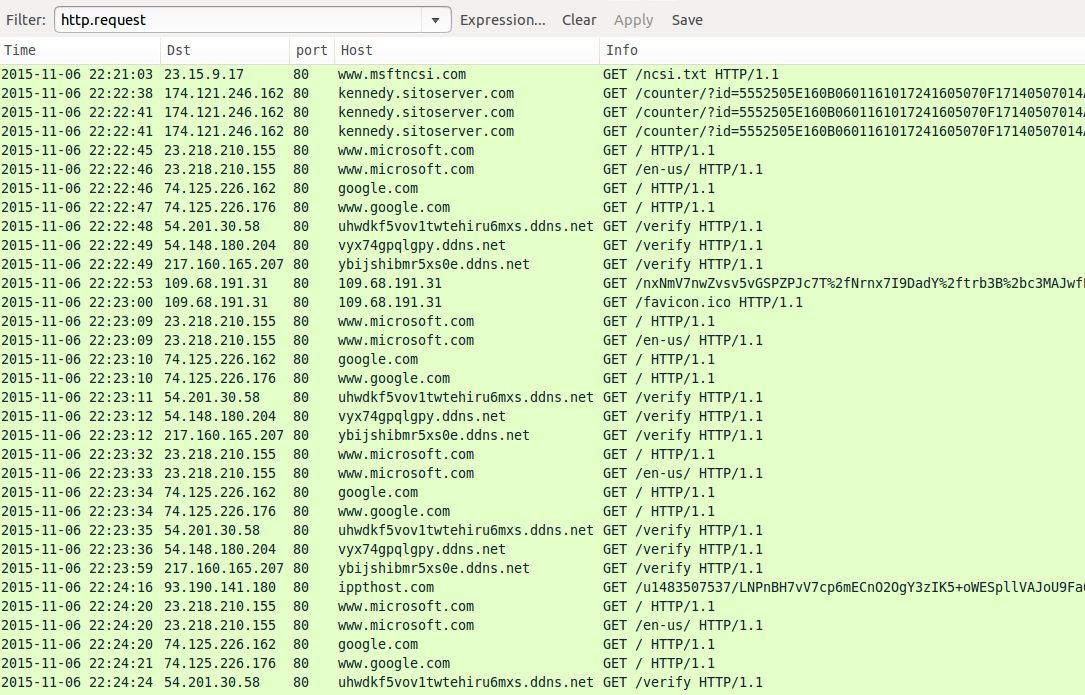
Shown above: Pcap from this exercise filtered in Wireshark.
Next, we'll look at the emails. Messages for this exercise are saved in the .eml format. This format is text-based and easily readable by Thunderbird. I copied the four emails extracted from the zip archive into Thunderbird.
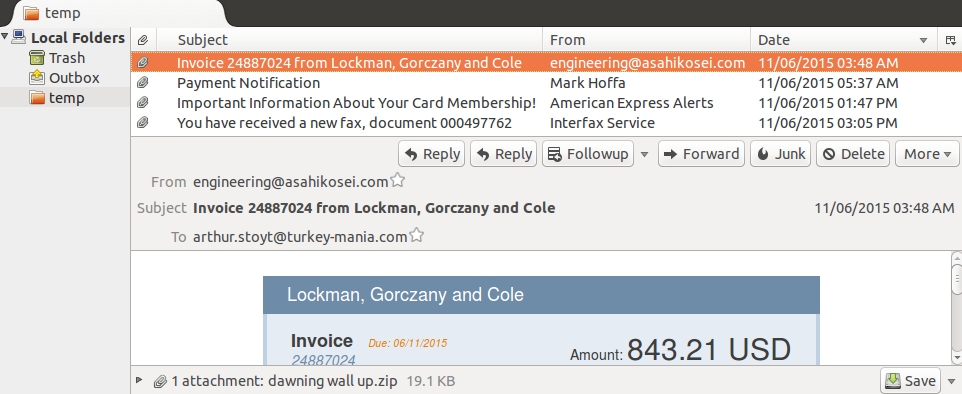
Shown above: The emails shown in Thunderbird.
THE FIRST EMAIL
This first email we'll look at has the subject line: Invoice 24887024 from Lockman, Gorczany and Cole. This email has a link that doesn't work, but it also has an attachment named dawning wall up.zip.
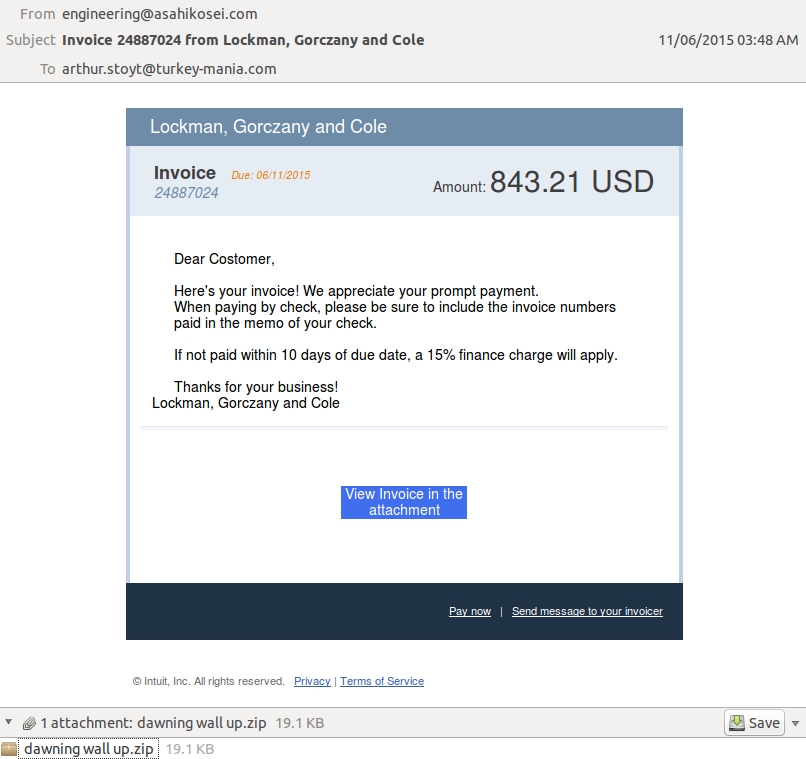
Shown above: The first email.
This zip archive contains an .exe file disguised as a PDF document (the file's icon makes it look like it's a PDF).
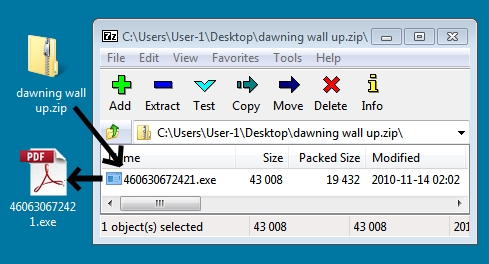
Shown above: Attachment from the first email.
Submit the extracted .exe file to VirusTotal, and you'll it's already been submitted. What does the traffic look like that's caused by our first malware sample? To find out, search any of the file's hashes (MD5, SHA1, or SHA256) in Malwr.com (must have an account, but it's free) and Hybrid-Analysis.com (don't need an account).
In this case, Malwr.com doesn't show any traffic from this malware sample; however, Hybrid-Analysis.com does.
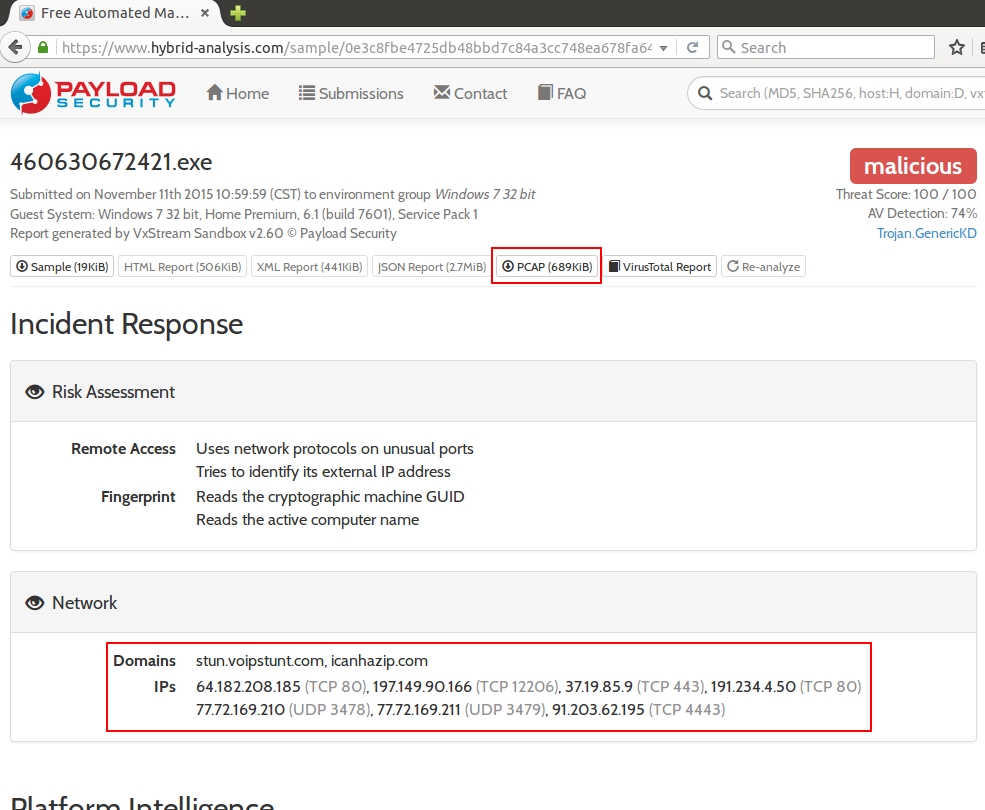
Shown above: Hybrid-Analysis.com's information for our first malware sample.
Hybrid-Analysis.com also provides a pcap of the post-infection traffic. If we open it in Wireshark, we'll find it doesn't match traffic from our infected host. Our preliminary assesment? The user did not run the attachment from this email. [NOTE: This file is an Upatre downloader designed to infect a computer with Dyre malware.]
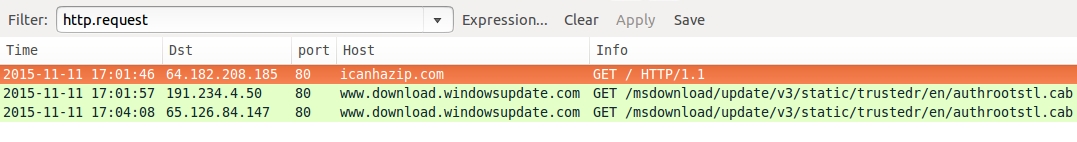
Shown above: The pcap from Hybrid-Analysis.com for our first malware sample shown in Wireshark, filtered for http.request.
THE SECOND EMAIL
Our second email has the subject line: Payment Notification. This email has an attachment named Bill Payment_000010818.xls.
Shown above: The second email.
Submit the .xls attachment to VirusTotal, and you'll it's already been submitted. What does the traffic look like from our second malware sample? Let's review the results from Malw.com and Hybrid-Analysis.com.
Of note, you'll want to search for the file hash and use the earliest submission if the file has been submitted multiple times. Also of note, Malwr.com doesn't provide pcap files for samples submitted by someone else, but it will still provide some of the traffic details.
In this case, Both Malwr.com and Hybrid-Analysis.com show post-infection traffic by the malware.
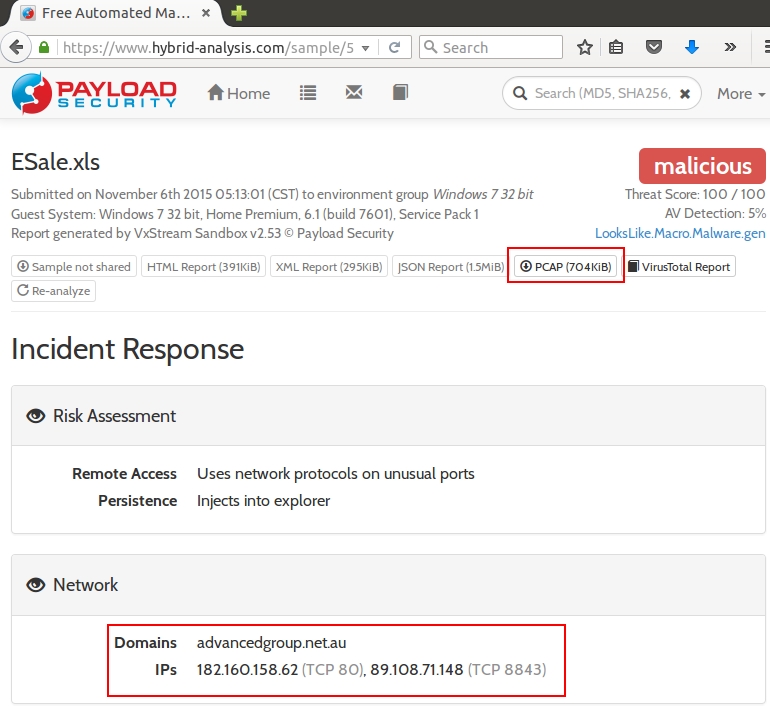
Shown above: Hybrid-Analysis.com's information for our second malware sample.
Download Hybrid-Analysis.com's pcap of the post-infection traffic. Open it in Wireshark, and you'll find it doesn't match traffic from our infected host. Our preliminary assesment? The user did not run the attachment from the second email.
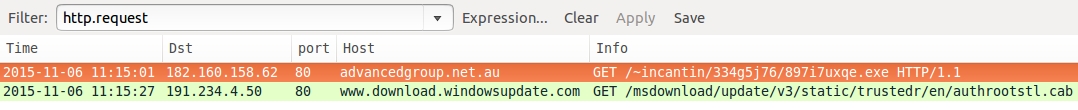
Shown above: The pcap from Hybrid-Analysis.com for our first malware sample shown in Wireshark, filtered for http.request.
THE THIRD EMAIL
Our third email has the subject line: Important Information About Your Card Membership!. This email has an attachment named AmericanExpress.html.
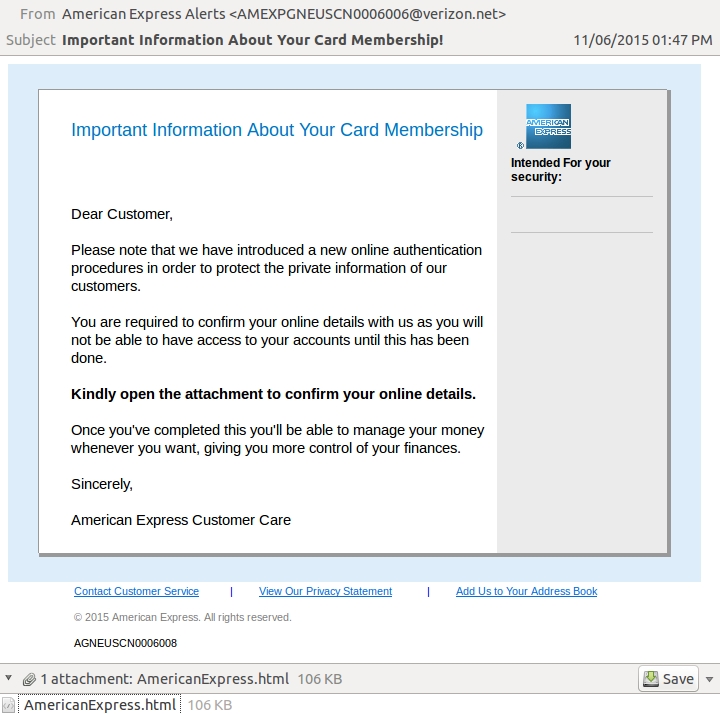
Shown above: The third email.
This HTML file is a fake login page for American Express. It's designed to steal someone's login credentials, and it's not malware that would infect a Windows computer. Our preliminary assessment? This is not the email we're looking for.
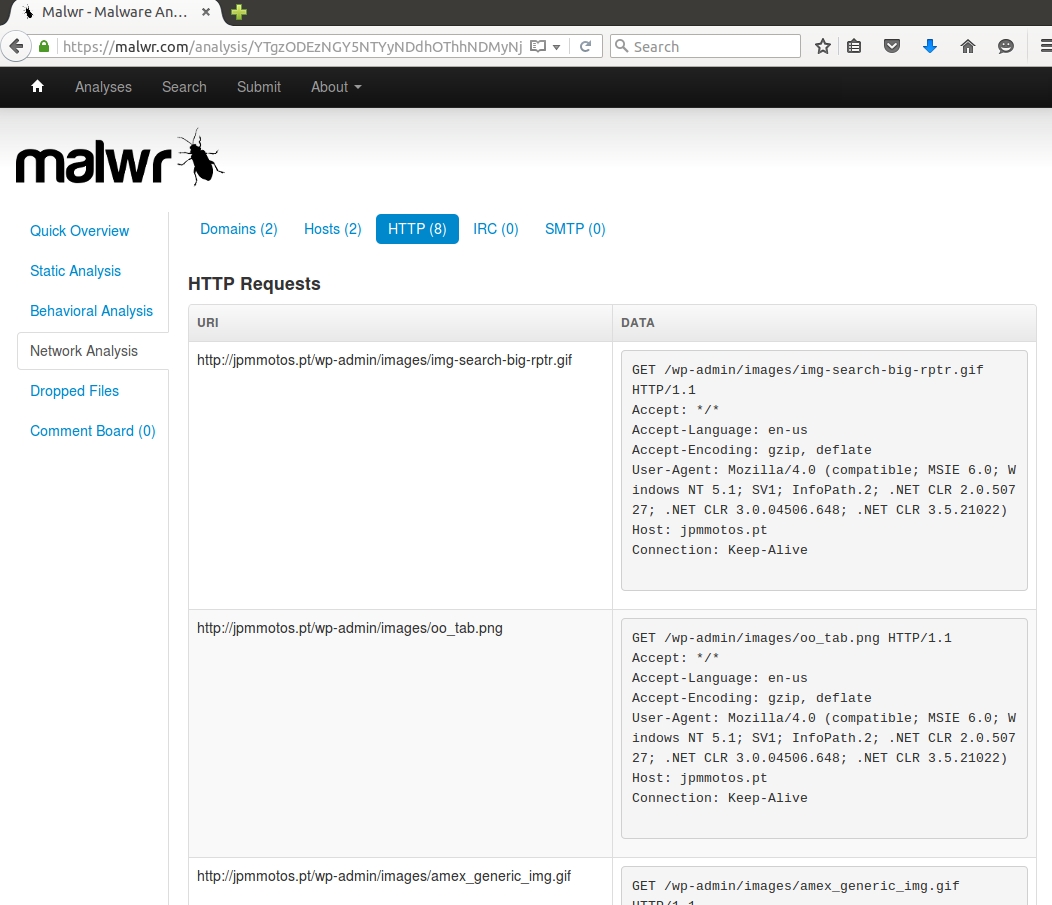
Shown above: Malwr.com's analysis of the HTML file.
THE FOURTH EMAIL
Our fourth email has the subject line: AmericanExpress.html. This email has an attachment named fax000497762.zip.
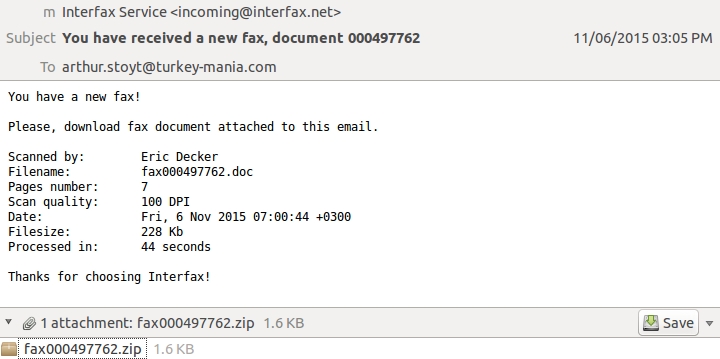
Shown above: The fourth email.
This zip archive contains a .js file.
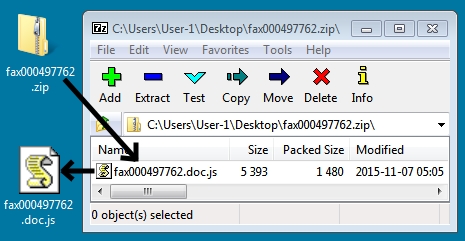
Shown above: Attachment from the fourth email.
Submit the extracted .js file to VirusTotal, and you'll it's already been submitted. What does the traffic look like from our last malware sample? Let's review the results from Malw.com and Hybrid-Analysis.com.
In this case, Both Malwr.com and Hybrid-Analysis.com show post-infection traffic by the malware.
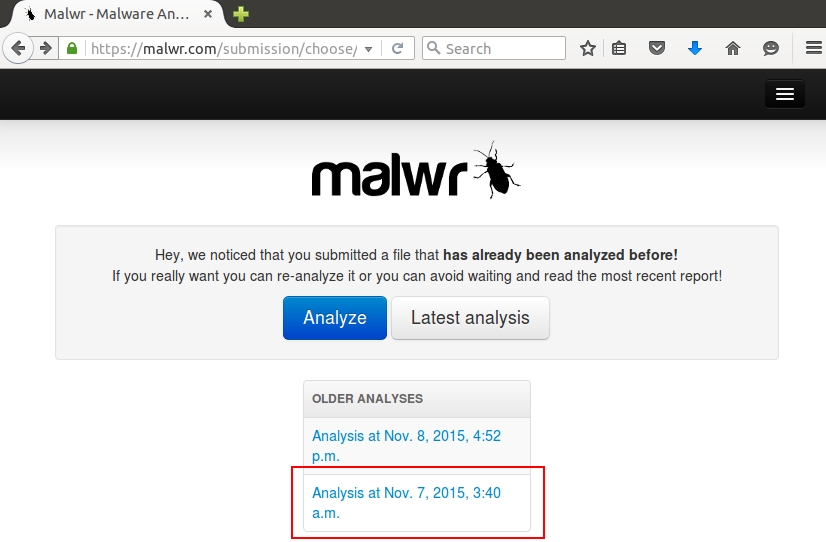
Shown above: Choosing the earliest submission of this malware from Malwr.com
Reviewing the traffic in Malwr.com, you'll find similar traffic patterns and domain names. Our preliminary assessment? This is the email the user opened. This is the malware the user ran on his Windows host.
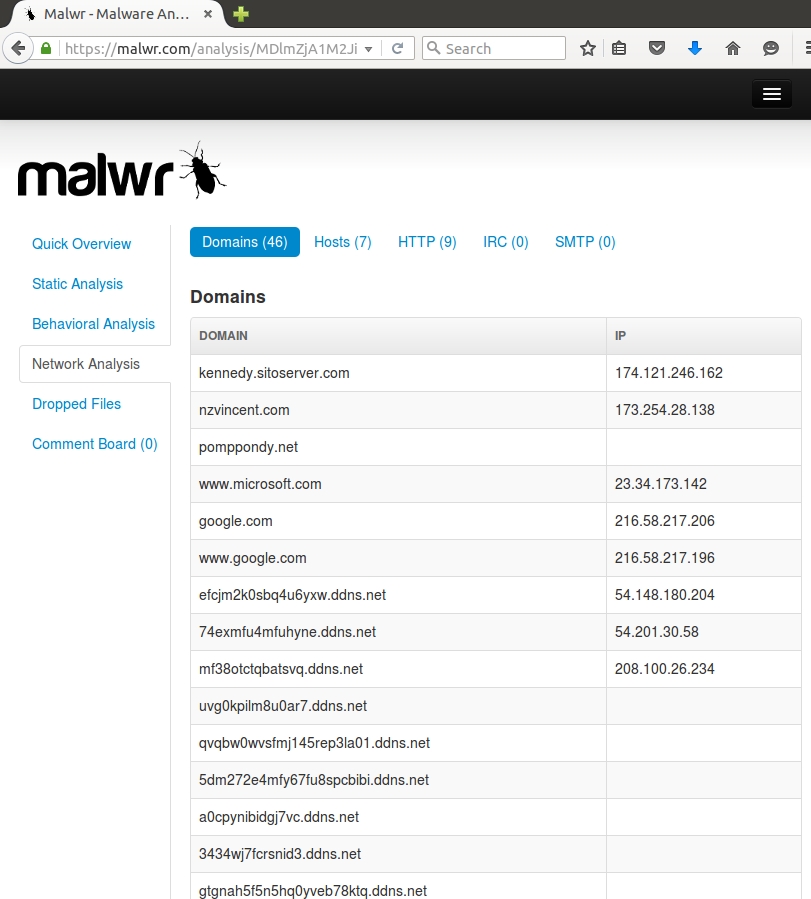
Shown above: Malwr.com's list of domains seen in the post-infection traffic.
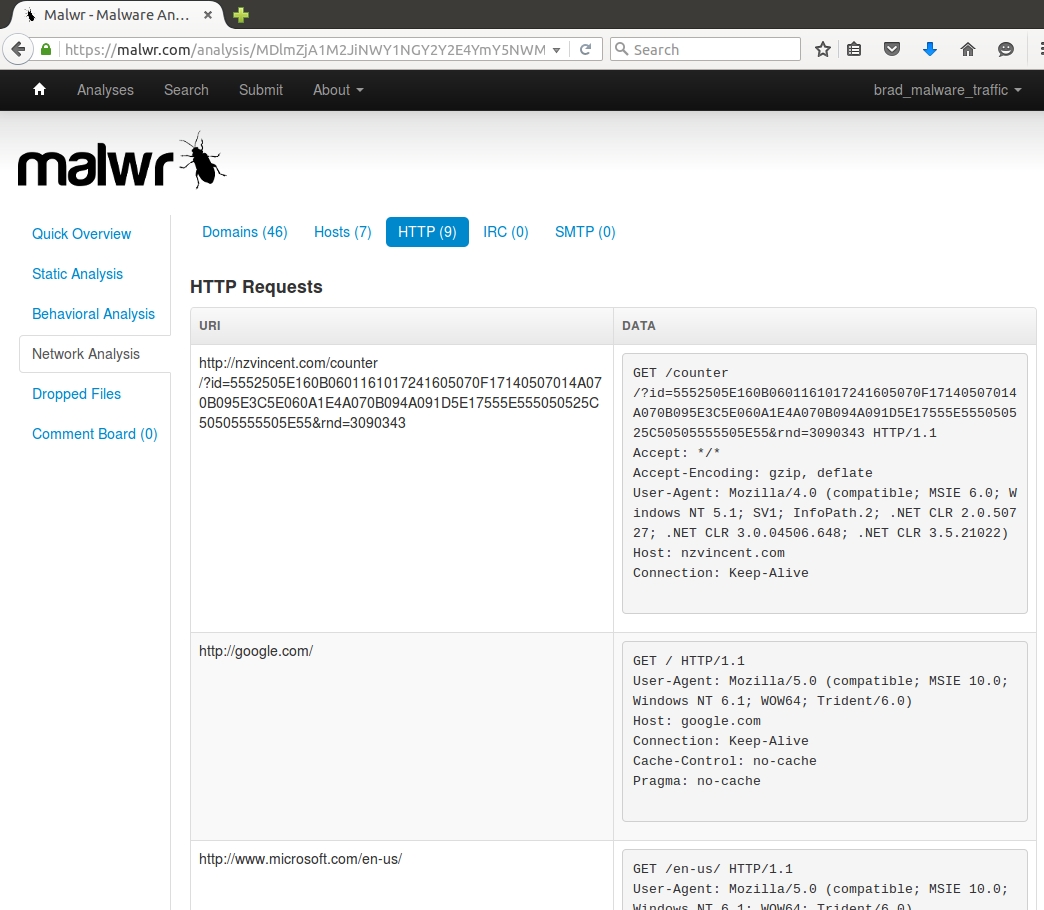
Shown above: Malwr.com's list of the HTTP requests seen in the post-infection traffic.
FINAL WORDS
As always, thanks for following along. Hope you had as much fun going through this exercise as I had making it.
Click here to return to the main page.
