2016-01-07 - TRAFFIC ANALYSIS EXERCISE - ALERTS ON 3 DIFFERENT HOSTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2016-01-07-traffic-analysis-exercise.pcap.zip 12.1 MB (12,055,896 bytes)
- Zip archive of the alerts: 2016-01-07-traffic-analysis-exercise-alerts.zip 80.6 kB (80,593 bytes)
SCENARIO
You are working as an analyst reviewing suspcious network events at your organization's Security Operations Center (SOC). Things have been quiet for a while. However, you notice several alerts occur within minutes of each other on 3 separate hosts.
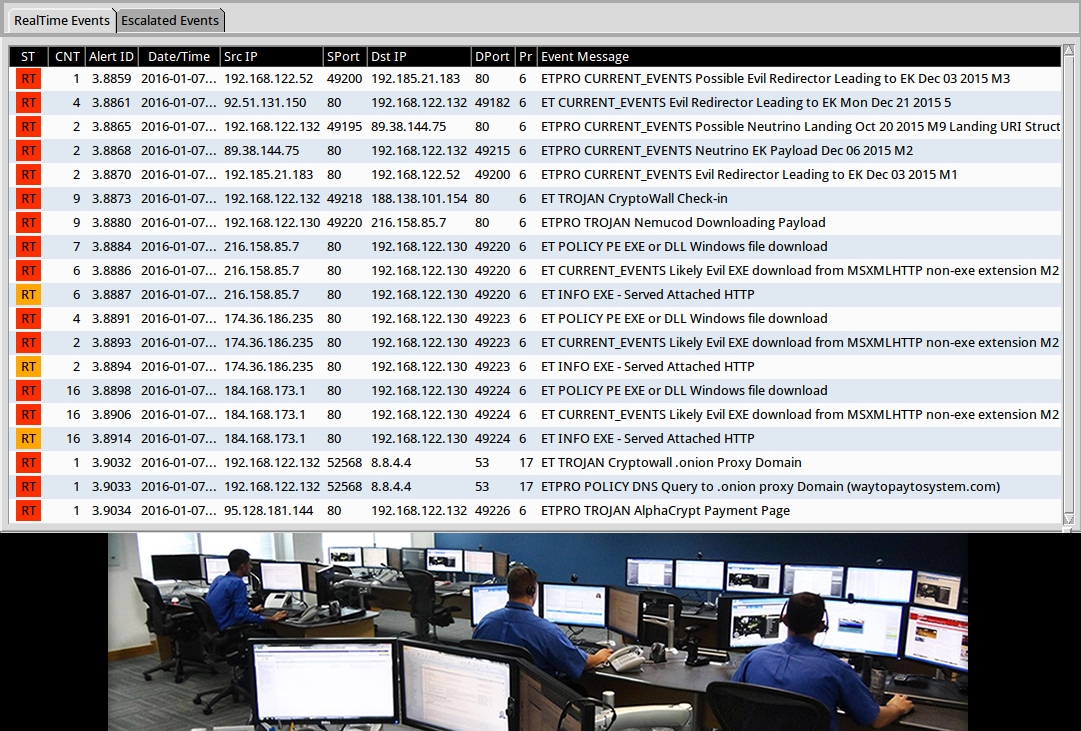
Said one analyst to another: A lot of these alerts contain the word "evil."
THE REPORT
Your were able to retrieve a pcap of network traffic, and you have a list of Snort and Suricata events from the activity. You'll need to write a report. Your report should include:
- Date and time range of the traffic you're reviewing.
- IP address, MAC address, and host name for each of the 3 computers in the pcap.
- Description of the activity for each of the 3 computers (what happened, if the host became infected, any details, etc.).
- A conclusion with recommendations for any follow-up actions.
And by "write" we mean type... Get it together, Dave!
ANSWERS
- Click here for the answers.
Click here to return to the main page.

