2016-02-06 - TRAFFIC ANALYSIS EXERCISE ANSWERS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive the pcap: 2016-02-06-traffic-analysis-exercise.pcap.zip 8.8 MB (8,838,133 bytes)
- Zip archive of the malspam, Snort/Suricata logs, and spreadsheet with employee info: 2016-02-06-traffic-analysis-exercise-emails-and-alerts.zip 48.0 kB (47,966 bytes)
NOTES:
- David posted his write-up here. Feel free to review, as his write-up goes into more detail than I did
ANSWERS
Below are my answers for this traffic analysis exercise:
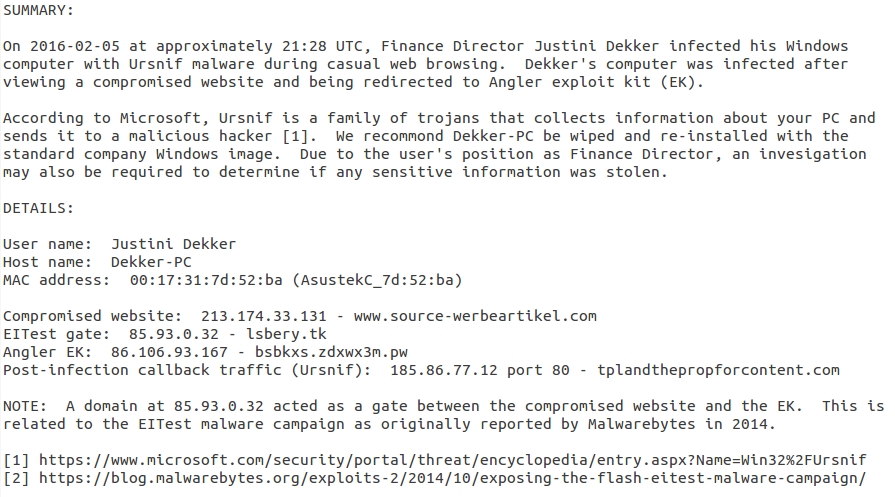
DETAILS
There's just one host in this pcap, so you can easily find out information on the Windows host by reviewing NBNS or DHCP traffic as shown below. That should give you the IP address, MAC address, and host name.
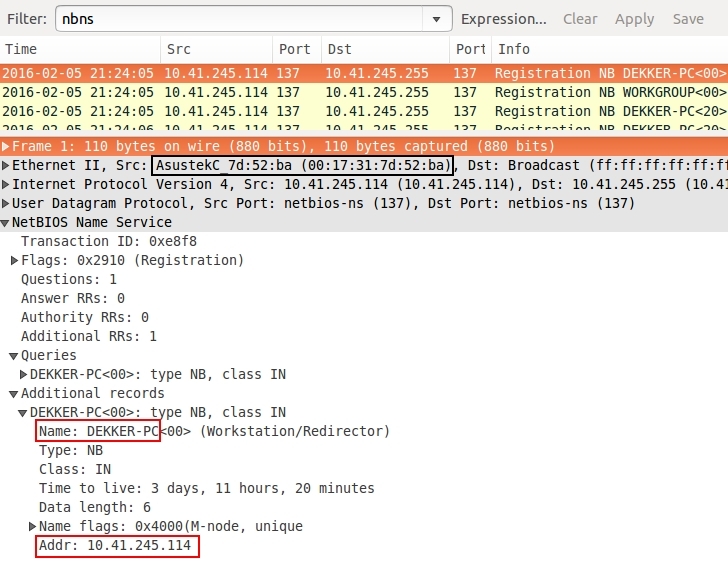
Shown above: Filtering on NBNS traffic in Wireshark.
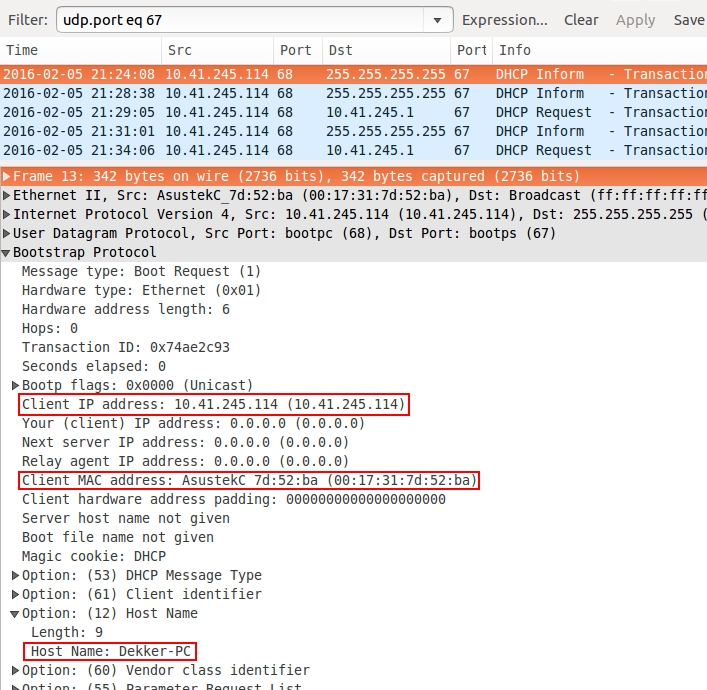
Shown above: Filtering on DHCP traffic in Wireshark.
Once you have the name of the PC, you can check the employee roster to see who it is.
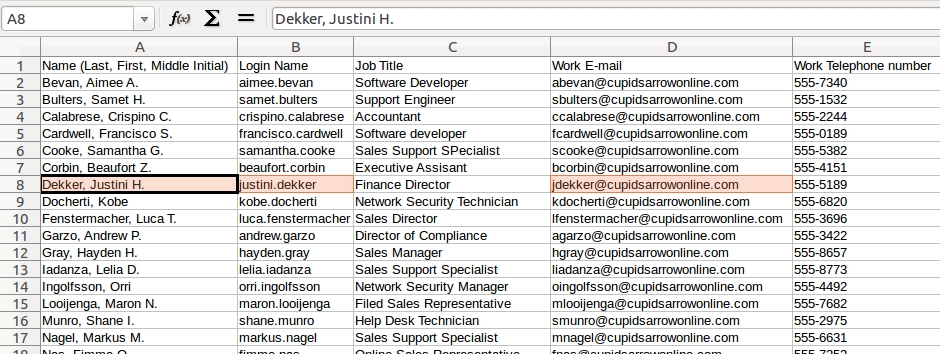
Shown above: Finding the user on the employee roster by using the Windows host name.
The first thing you should do when investigating these issues is to review the alerts. I've included the alerts in two text files. One has Suricata alerts using the EmergingThreats Pro ruleset. The other has Snort alerts using the Talos subscription ruleset.
They are both somewhat lengthy. If you want to get a good idea of the alerts in the Suricata list, and you're using a Linux/Unix/Mac host, you can use the grep command in a terminal window. For example, grep ET 2016-02-06-traffic-analysis-exercise-suricata-logs.txt should list all the alert lines from the file.
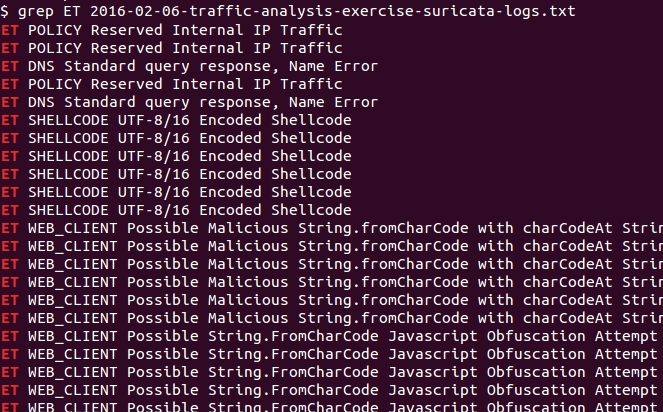
Shown above: Grep-ing alert lines from the text file of Suricata alerts.
Looking through the results, you'll find indications of Angler EK and Ursnif malware.
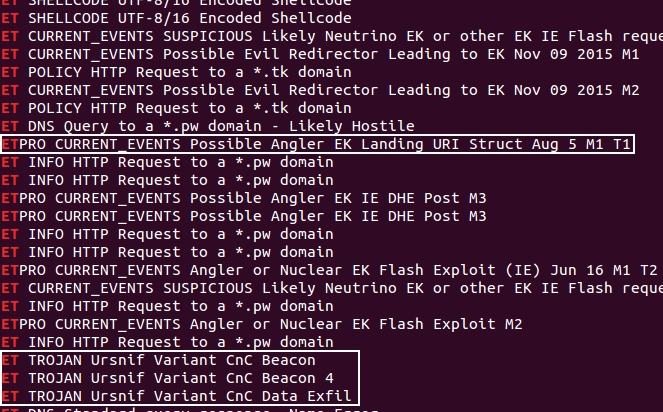
Shown above: Shown above: Indicators of Angler EK and Ursnif.
Using grep on the Snort alert file, you'll also see indicators of Angler EK.
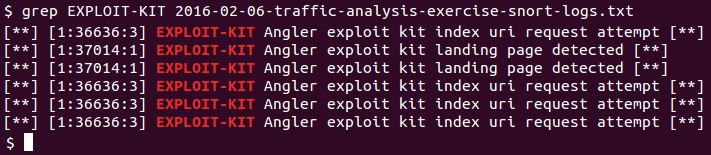
Shown above: Grep-ing for exploit kit activity from the Snort logs.
You'll have to review the Snort logs to see which IP address that Angler EK was on.
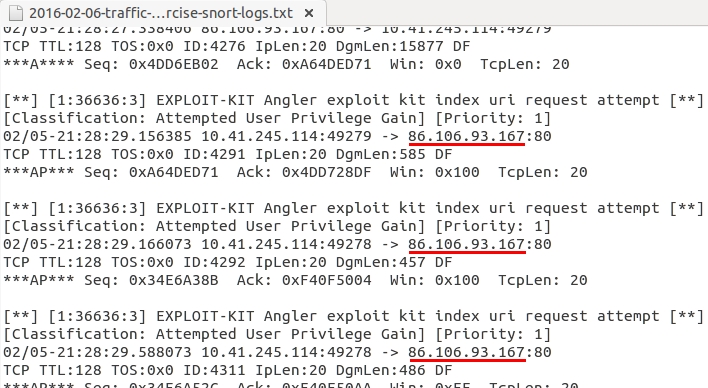
Shown above: Looking for the IP address used by Angler EK in the Snort logs.
The Suricata logs show the same IP address for the EK alerts.
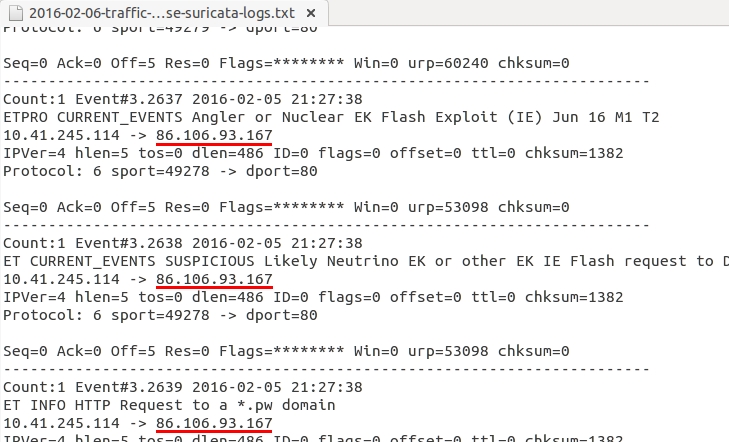
Shown above: Confirming the IP address used by Angler EK in the Suricata logs.
The Suricata logs will also show you the IP address for the Ursnif activity.
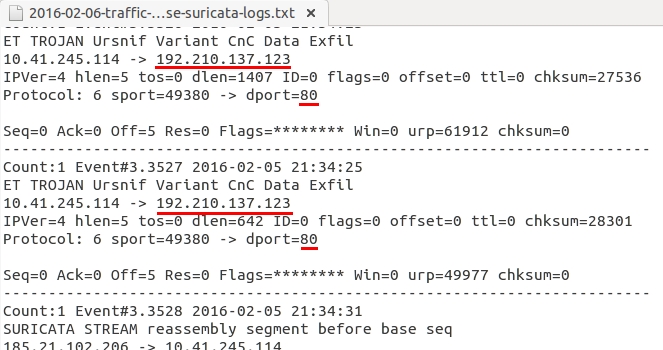
Shown above: Looking for the IP address for traffic caused by Ursnif in the Suricata logs.
When following the TCP stream for the Angler EK landing page (the first HTTP GET request to the Angler EK domain), you'll find a referer. That's an EITest gate.
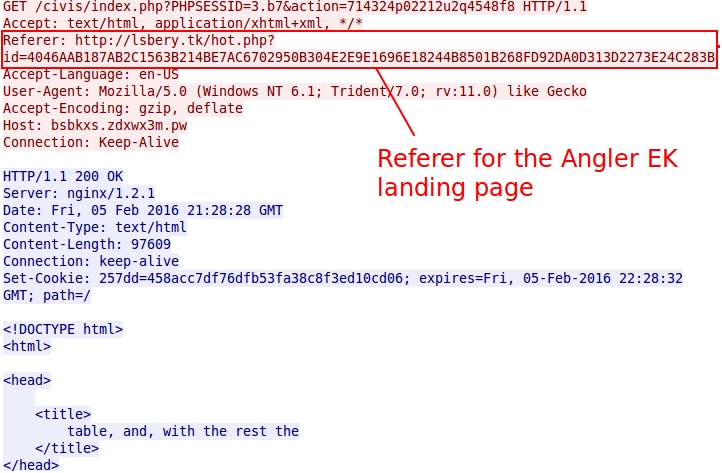
Shown above: Referer for Angler EK.
Go to the TCP stream for the above referer, and you'll find the EITest traffic with another referer. This other referer is the compromised website that led to the EITest gate.
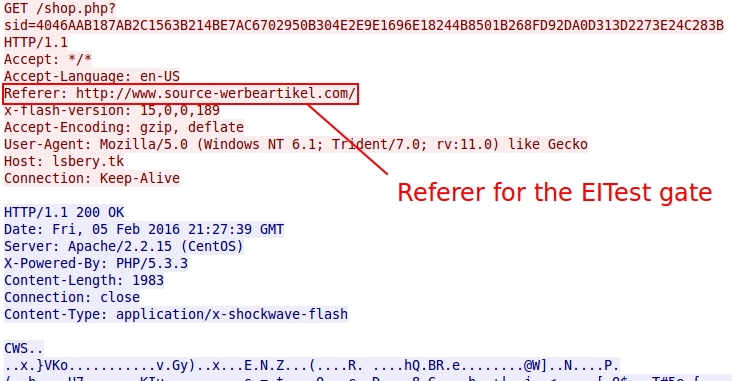
Shown above: Referer for the EITest gate.
Filtering the traffic in Wireshark shows the EITest gate and Angler EK urls as shown below.
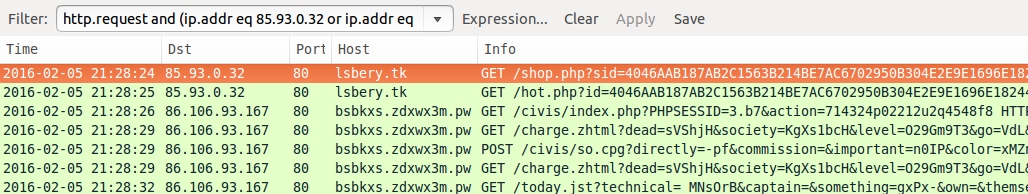
Shown above: EITest gate and Angler EK traffic in Wireshark.
Out of curiosity, I filtered the post-infection traffic from Ursnif in Wireshark.
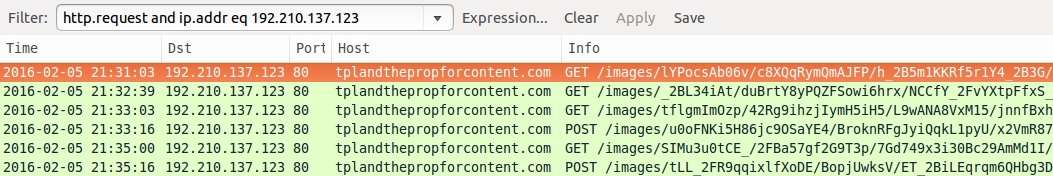
Shown above: Ursnif post-infection traffic.
FINAL WORDS
The emails from this exercise were a diversion. The root cause of the infection was the EK. Hopefully, you found this exercise helpful. It took me a while to write the answers, but any time I got side-tracked, Sven would push me in the right direction.

Sven's always pushing someone in "the right direction."
Click here to return to the main page.
