2016-02-29 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-29-Angler-EK-data-dump-4-pcaps.zip 2.9 MB (2,911,987 bytes)
- 2016-02-29-Angler-EK-data-dump-malware-and-artifacts.zip 2.1 MB (2,080,620 bytes)
NOTES:
- Saw another CVE-2016-0034 Silverlight exploit as reported earlier this month by Kafeine ( link ).
- Big thanks to Denis who identified traffic associated with the Sucuri blog post about the Pseudo Darkleech campaign.
DETAILS
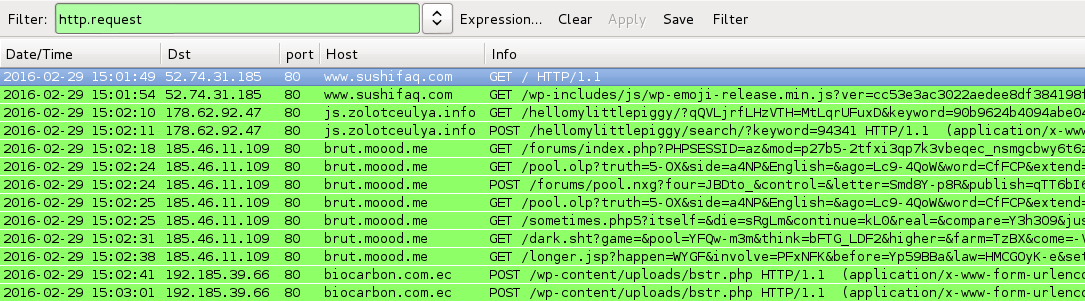
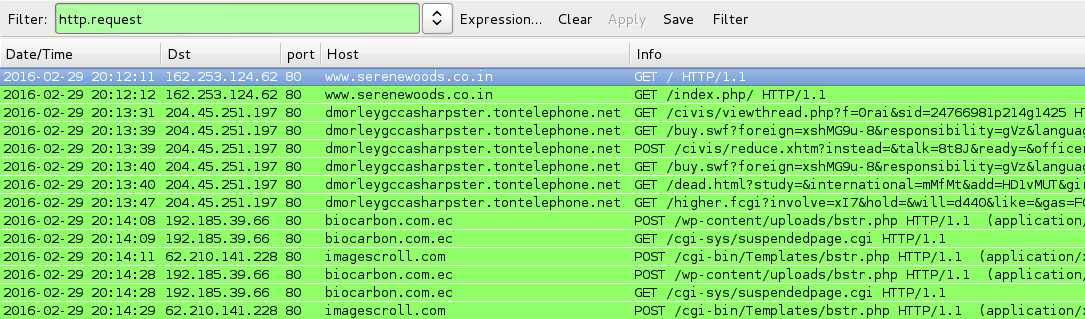

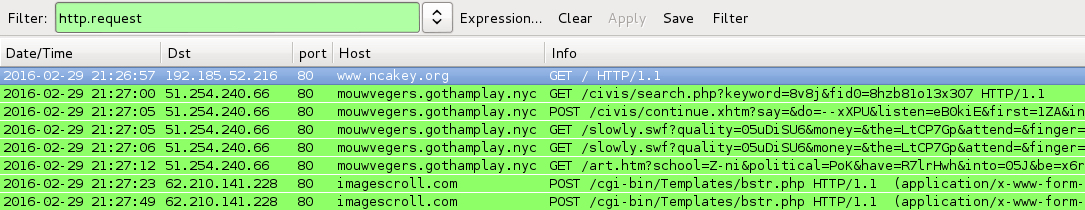
DATE/TIME: 2016-02-29 15:01 UTC
- www.sushifaq[.]com - Compromised website
- www.sushifaq[.]com - GET /wp-includes/js/wp-emoji-release.min.js?ver=cc53e3ac3022aedee8df384198ff44fb [.js file with injected script]
- 178.62.92[.]47 port 80 - js.zolotceulya[.]info - Admedia gate
- 185.46.11[.]109 port 80 - brut.moood[.]me - Angler EK
- 192.185.39[.]66 port 80 - biocarbon[.]com[.]ec - POST /wp-content/uploads/bstr.php [TeslaCrypt ransomware callback]
DATE/TIME: 2016-02-29 20:12 UTC
- www.serenewoods[.]co[.]in - Compromised website
- 204.45.251[.]197 port 80 - dmorleygccasharpster.tontelephone[.]net - Angler EK
- 192.185.39[.]66 port 80 - biocarbon[.]com[.]ec - POST /wp-content/uploads/bstr.php [TeslaCrypt ransomware callback]
- 62.210.141[.]228 port 80 - imagescroll[.]com - POST /cgi-bin/Templates/bstr.php [TeslaCrypt ransomware callback]
DATE/TIME: 2016-02-29 20:54 UTC
- www.buro[.]net[.]au - Compromised website
- 204.45.251[.]197 port 80 - tynnyrilt.myerscompanies[.]com - Angler EK
- 62.210.141[.]228 port 80 - imagescroll[.]com - POST /cgi-bin/Templates/bstr.php [TeslaCrypt ransomware callback]
DATE/TIME: 2016-02-29 21:26 UTC
- www.ncakey[.]org - Compromised website
- 51.254.240[.]66 port 80 - mouwvegers.gothamplay[.]nyc - Angler EK
- 62.210.141[.]228 port 80 - imagescroll[.]com - POST /cgi-bin/Templates/bstr.php [TeslaCrypt ransomware callback]
EXPLOITS/MALWARE:
- be6fe8b5fbd85b536396273313a3fbac 2016-02-29-Admedia-Angler-EK-payload-TeslaCrypt-ransomware-after-sushifaq_com.exe
- 1d50ab33a89ac28a500e09f2f7856bab 2016-02-29-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-ncakey_org.exe
- c2c2d3a5f24e17a13bd8ba599be2fb7f 2016-02-29-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-serenewoods_co_in.exe
- e44e90c06bfeda1b9245bc00d21f37af 2016-02-29-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-buro_net_au.exe
- 544884c1a956f39a5c198eaaf5503e80 2016-02-29-Admedia-Angler-EK-flash-exploit-after-sushifaq_com.swf
- c660cd298a1aab3feda3894ca86cac12 2016-02-29-pseudo-Darkleech-Angler-EK-flash-exploit-after-buro_net_au.swf
- c660cd298a1aab3feda3894ca86cac12 2016-02-29-pseudo-Darkleech-Angler-EK-flash-exploit-after-ncakey_org.swf
- c660cd298a1aab3feda3894ca86cac12 2016-02-29-pseudo-Darkleech-Angler-EK-flash-exploit-after-serenewoods_co_in.swf
Silverlight exploit
- 1d9199d81006ddd7c250ec281f33a8dd 2016-02-29-Admedia-Angler-EK-Silverlight-exploit-after-sushifaq_com.xap
Click here to return to the main page.