2016-03-14 - RIG EK FROM 188.227.72[.]46
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-14-Rig-EK-3-pcaps.zip 551.4 kB (551,432 bytes)
- 2016-03-14-Rig-EK-malware-and-artifacts.zip 262.0 kB (262,025 bytes)
NOTES:
- Wasn't able to get a full infection chain in the first two pcaps, and the go0ogleee[.]com gate URL wasn't pointing to Rig EK later in the day.
- Traffic from the last pcap (kicked off by pavtube[.]com) is explained in two diaries at the Internet Storm Center (ISC):
TRAFFIC
2016-03-14 14:07 UTC:
- dtransrentcar[.]com - Compromised website
- 191.101.21[.]122 port 80 - www.go0ogleee[.]com - GET /index.php?promo=imesh [gate redirecting to Rig EK]
- 188.227.72[.]46 port 80 - th.debatestage[.]in - Rig EK
2016-03-14 17:40 UTC:
- oysterplus[.]net - Compromised website
- 103.7.43[.]41 port 80 - thucphamchucnang69[.]com - GET /wp-content/uploads/2015/05/logo-final-69.jp [first gate redirecting to second date]
- 191.101.21[.]122 port 80 - www.go0ogleee[.]com - GET /index.php?promo=imesh [second gate redirecting to Rig EK]
- 188.227.72[.]46 port 80 - de.ediabetesremedy[.]com - Rig EK
2016-03-14 21:35 UTC:
- www.pavtube[.]com - GET /public/temp/js/jquery.js [malicious script that calls for variable from gate]
- 198.2.206[.]238 port 80 - xm.psychskins[.]com - GET /ncvutviewforumbpx.php [gate returning the variable]
- 188.227.72[.]46 port 80 - ef.entn[.]in - Rig EK
IMAGES
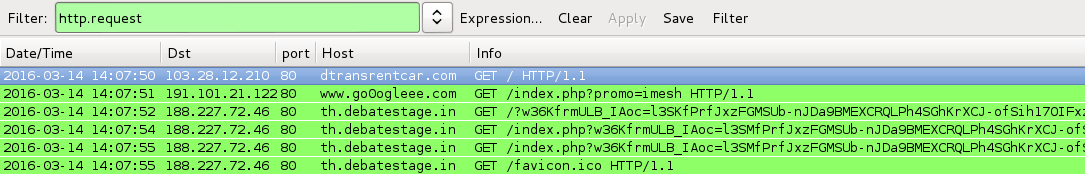
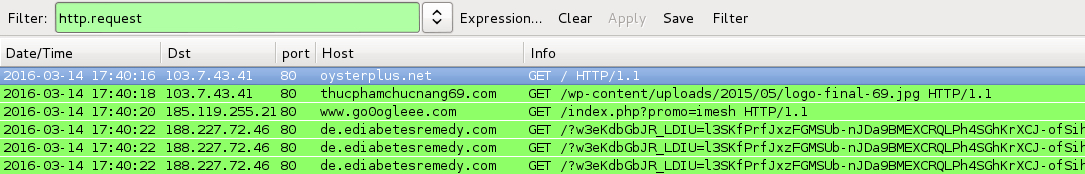
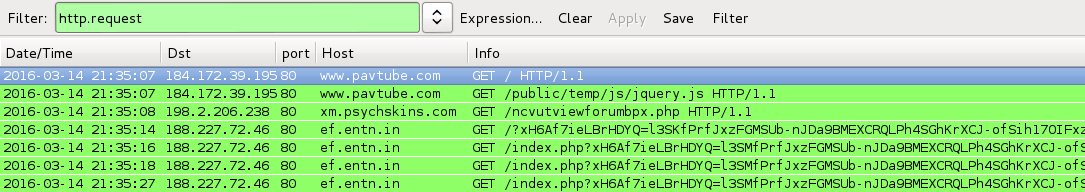
Shown above: Traffic from the infections filtered in Wireshark.
Click here to return to the main page.
