2016-03-31 - RIG EK FROM 188.227.74[.]171
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-03-31-Rig-EK-traffic.pcap.zip 273.5 kB (273,533 bytes)
- 2016-03-31-Rig-EK-malware-and-artifacts.zip 251.8 kB (251,758 bytes)
NOTES:
- This is the same activie I've documented before, where Rig EK distributed Qbot ( link ).
- Saw a Silverlight exploit in today's Rig EK traffic.
- Rig EK using a Silverlight exploit was first spotted by @malcode, identified by @antonivanovm, and documented by @kafeine on 2016-03-29.
TRAFFIC

Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 67.215.187[.]94 port 80 - xc.rottencouchtomatoes[.]com - GET /cuqviewforummsmz.php - returned variable to generate Rig EK landing page URL
- 188.227.74[.]171 port 80 - fg.the-schoolbook[.]com - Rig EK
MALWARE AND ARTIFACTS
SHA256 hash: a3b67b732f75b137ddfb5392bcb235c21dffb687304c972c8064d6bc5fe7cbac
File name: 2016-03-31-Rig-EK-flash-exploit.swf
SHA256 hash: 13410c3855c9cd4d3e54eb45ab4836ae8086aa03aa2f21257dd0fb9879b19dcb
File name: 2016-03-31-Rig-EK-landing-page.txt
SHA256 hash: 7b19d411ff077a6053d3ad3edb155ab932f03932cafb4905154325168c75c221
File name: 2016-03-31-Rig-EK-payload.com.exe
SHA256 hash: acb74c05a1b0f97cc1a45661ea72a67a080b77f8eb9849ca440037a077461f6b
File name: 2016-03-31-Rig-EK-Silverlight-exploit.xap (same hash as Kafeine already posted)
SHA256 hash: e535cf04335e92587f640432d4ec3838b4605cd7e3864cfba2db94baae060415
File name: binaryreader.dll (extracted DLL from Silverlight .xap archive, same hash as Kafeine already posted)
SHA256 hash: 8b5e3be0c9633269c18b98bbfae9e1401037196dbc9e33ab5499881e11d189bc
File name: 2016-03-31-pavtube_com-jquery.js.txt
SHA256 hash: 225f920a3c8e88dc2d09ed122626997d043c79f3f48ad11b4381e51f525b64a3
File name: 2016-03-31-xc.rottencouchtomatoes_com-cuqviewforummsmz.php.txt
IMAGES

Shown above: Start of injected script in .js file from compromised website.
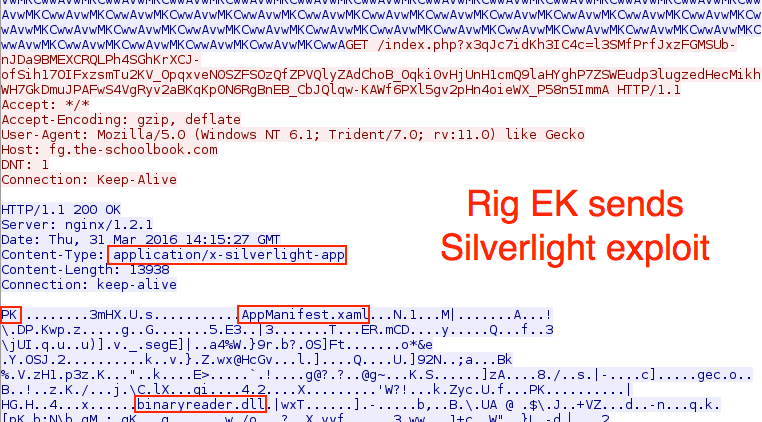
Shown above: Rig EK sends Silverlight exploit.
Click here to return to the main page.