2016-04-18 - EITEST AND PSEUDO-DARKLEECH ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-18-Angler-EK-traffic-2-pcaps.zip 5.2 MB (5,198,746 bytes)
- 2016-04-18-EITest-Angler-EK-sends-Panda-Banker.pcap (1,034,895 bytes)
- 2016-04-18-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap (4,867,166 bytes)
- 2016-04-18-Angler-EK-malware-and-artifacts.zip 1.5 MB (1,450,366 bytes)
- 2016-04-18-injected-EITest-script-in-page-from-compromised-site.txt (1,096 bytes)
- 2016-04-18-EITest-flash-file-from-caddea_tk.swf (15,528 bytes)
- 2016-04-18-EITest-Angler-EK-landing-page.txt (174,243 bytes)
- 2016-04-18-EITest-Angler-EK-flash-exploit.swf (31,688 bytes)
- 2016-04-18-EITest-Angler-EK-Silverlight-exploit.xap (169,132 bytes)
- 2016-04-18-extracted-DLL-from-Silverlight-exploit-GrmBL2Lnhwx.dll (209,408 bytes)
- 2016-04-18-EITest-Angler-EK-payload-Panda-Banker.exe (161,792 bytes)
- 2016-04-18-page-with-injected-pseudo-Darkleech-script-from-altanticeyephysicians_com.txt (40,138 bytes)
- 2016-04-18-pseudo-Darkleech-Angler-EK-landing-page.txt (174,289 bytes)
- 2016-04-18-pseudo-Darkleech-Angler-EK-flash-exploit.swf (40,376 bytes)
- 2016-04-18-C-Users-username-AppData-Local-Temp-15BA39EC-8171-4EBE-837B-3EDA6605A12-api-ms-win-system-rasadhlp-l1-1-0.dll (299,008 bytes)
- 2016-04-18-C-Users-username-AppData-Local-Temp-9D920166-42D4-4F1C-87BD-3353F7993691-api-ms-win-system-recovery-l1-1-0.dll (299,008 bytes)
- 2016-04-18-C-ProgramData-9A88E103-A20A-4EA5-8636-C73B709A5BF8-thawbrkr.dll (358,536 bytes)
- de_crypt_readme.bmp (232,6734 bytes)
- de_crypt_readme.html (3,315 bytes)
- de_crypt_readme.txt (1,641 bytes)
NOTES:
- Background on the pseudo-Darkleech campaign can be found here.
- Background on the EITest campaign can be found here.
- Identification of the EITest Angler EK payload is based on EmergingThreats alerts for post-infection traffic.
- Today's example of pseudo-Darkleech Angler EK delivered Bedep and followed up with CryptXXX ransomware.
- 2016-04-20 update: The 2 DLLs listed above under the user's AppData\Local\Temp directory are CryptXXX ransomware. See Proofpoint's blog post about it for more details.
- @Kafeine has an excellent blog post on Malware don't need coffee explaining how Bedep has evolved to avoid security researchers using virtual machines.
TRAFFIC
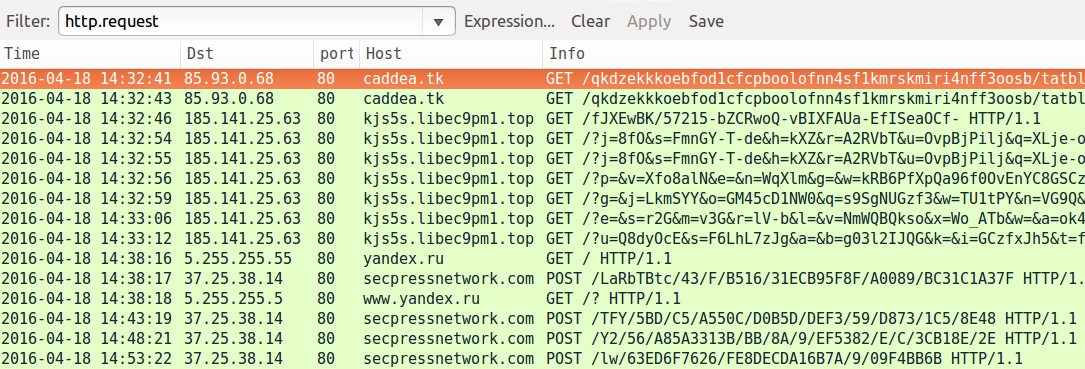
Shown above: Pcap of the EITest Angler EK infection traffic filtered in Wireshark.
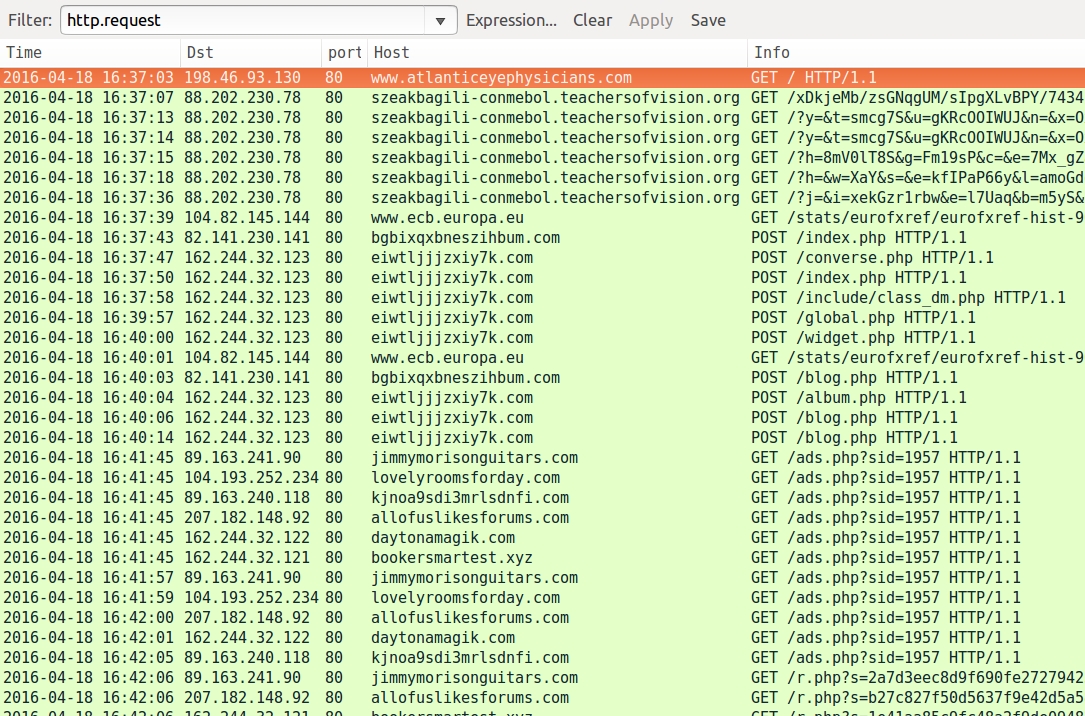
Shown above: Pcap of the pseudo-Darkleech Angler EK infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 85.93.0[.]68 port 80 - caddea[.]tk - EITest gate
- 185.141.25[.]63 port 80 - kjs5s.libec9pm1[.]top - Angler EK caused by the EITest campaign
- yandex[.]ru - Panda Banker connectivity check
- 37.25.38[.]14 port 80 - secpressnetwork[.]com - Panda Banker post-infection traffic
- 88.202.230[.]78 port 80 - szeakbagili-conmebol.teachersofvision[.]org - Angler EK caused by pseudo-Darkleech campaign
- www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml - Bedep connectivity check, info for DGA C2 domains
- 82.141.230[.]141 port 80 - bgbixqxbneszihbum[.]com - Bedep post-infection traffic
- 162.244.32[.]123 port 80 - eiwtljjjzxiy7k[.]com - Bedep post-infection traffic
- 146.0.42[.]68 port 443 - CryptXXX ransomware callback traffic
- 89.163.241[.]90 port 80 - jimmymorisonguitars[.]com - GET /ads.php?sid=1957 - Click fraud traffic
- 104.193.252[.]234 port 80 - lovelyroomsforday[.]com - GET /ads.php?sid=1957 - Click fraud traffic
- 89.163.240[.]118 port 80 - kjnoa9sdi3mrlsdnfi[.]com - GET /ads.php?sid=1957 - Click fraud traffic
- 207.182.148[.]92 port 80 - allofuslikesforums[.]com - GET /ads.php?sid=1957 - Click fraud traffic
- 162.244.32[.]122 port 80 - daytonamagik[.]com - GET /ads.php?sid=1957 - Click fraud traffic
- 162.244.32[.]121 port 80 - bookersmartest[.]xyz - GET /ads.php?sid=1957 - Click fraud traffic
IMAGES
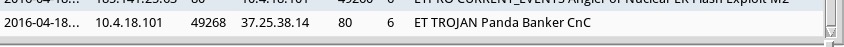
Shown above: Using the EmergingThreats ruleset, I saw alerts for Panda Banker malware from the EITest Angler EK traffic.

Shown above: Panda Banker malware made persistent on the infected Windows host after the EITest Angler EK traffic.
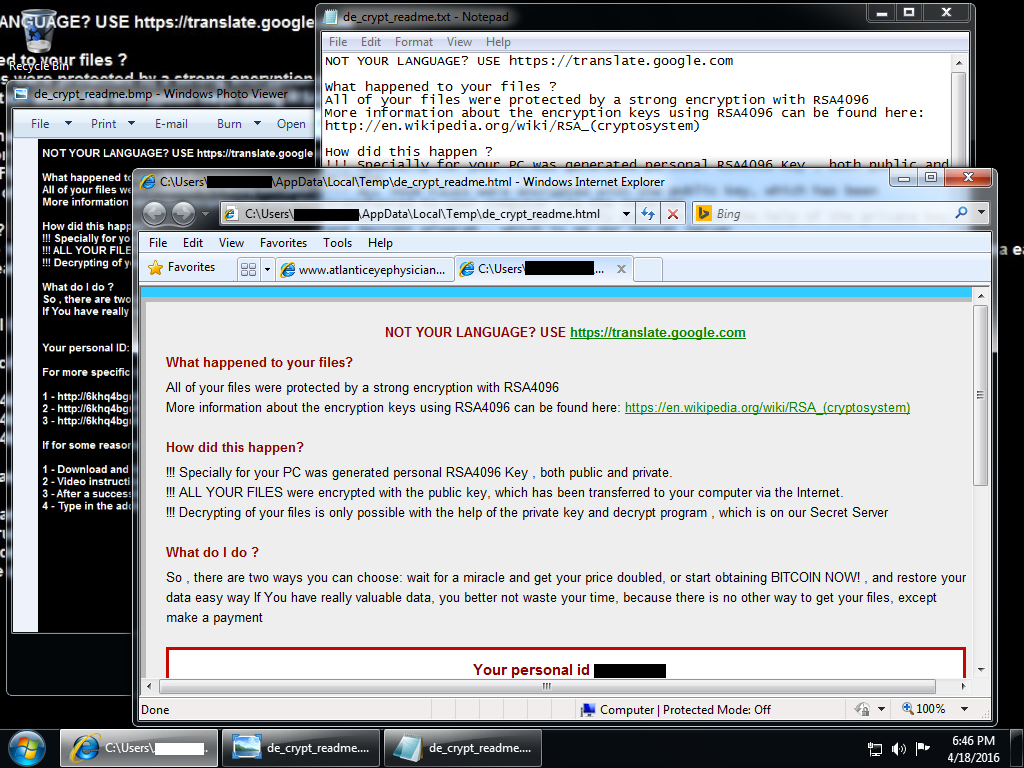
Shown above: Desktop of the infected Windows host with CryptXXX ransowmare artifacts after pseudo-Darkleech Angler EK caused the Bedep infection.
Click here to return to the main page.