2016-04-21 - RIG EK FROM 5.200.35[.]189 SENDS TOFSEE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-21-Rig-EK-sends-Tofsee.pcap.zip 181.2 kB (181,240 bytes)
- 2016-04-21-Rig-EK-sends-Tofsee.pcap (316,262 bytes)
- 2016-04-21-Rig-EK-and-Tofsee-files.zip 594.1 kB (594,071 bytes)
- 2016-04-21-Rig-EK-flash-exploit.swf (13,887 bytes)
- 2016-04-21-Rig-EK-landing-page.txt (4,736 bytes)
- 2016-04-21-Rig-EK-malware-pyaload-Tofsee.exe (208,896 bytes)
- 2016-04-21-iframe-returned-from-tobiasdesigns_com-pointing-to-Rig-EK.txt (332 bytes)
- 2016-04-21-page-from-doc-italia_com-with-injected-script.txt (5,972 bytes)
- ppyymxkk.exe (4,129,1776 bytes) -- Dropped at C:\Users\[username]\ppyymxkk.exe
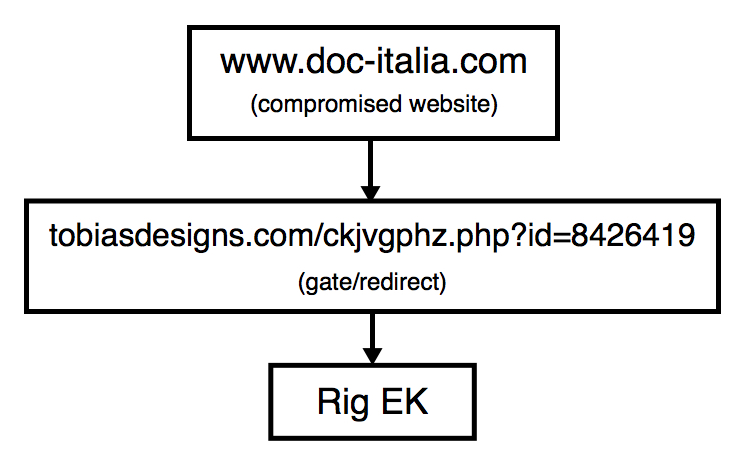
Shown above: A flow chart depicting this infection's chain of events.
NOTES:
- Post-infection traffic matches what I've seen before with Tofsee.
- The filter I used in the pcap image below was: http.request or (frame.number > 64 and (dns or tcp.flags eq 0x0002))
- Something like the above Wireshark filter is a quick way to check for post-infection TCP connections after the EK traffic.
TRAFFIC

Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 68.171.129[.]152 port 80 - tobiasdesigns[.]com - Gate/redirect
- 5.200.35[.]189 port 80 - fe.skiresortco[.]com - Rig EK
- 111.121.193[.]242 port 443 - encrypted Post-infection traffic caused by Tofsee malware
- 171.6.91[.]73 port 7249 - encrypted Post-infection traffic caused by Tofsee malware
- 104.40.211[.]35 port 80 - Post-infection traffic caused by Tofsee malware (no content)
- Attempted SMTP to various mail server IP addresses over TCP port 25 - Post-infection traffic caused by Tofsee
IMAGES
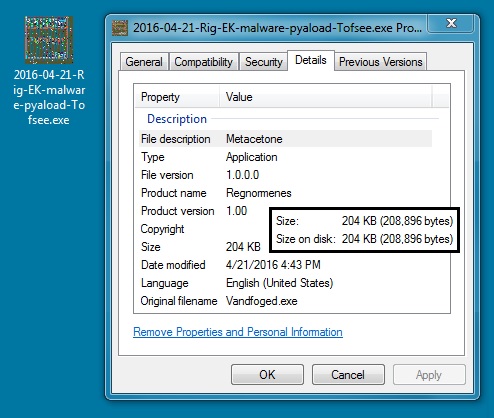
Shown above: The Rig EK payload (Tofsee).
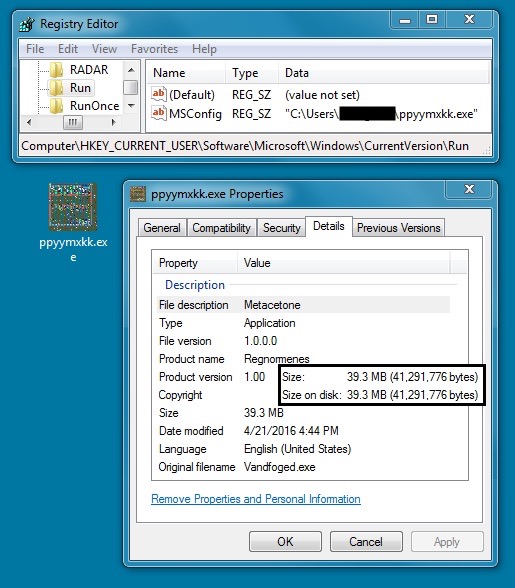
Shown above: The 41+ MB file dropped by Tofsee (the malware copied itself and
added a lot of padding) with one of the registry entries for persistence.
Click here to return to the main page.