2016-04-28 - THURSDAY MALWARE HUNT (MOSTLY LOCKY RANSOMWARE)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-04-28-email-traffic-and-malware-samples.zip 2.4 MB (2,445,002 bytes)
NOTES:
- Bit off more than I could chew today. Ran across several different campaigns, and the data dump is below.
- Only got Locky ransomware when I tested the file attachments. However, not all of them worked.
- The six extracted "details.rse" files will execute using the Windows Script Engine, just like any .js file. Might have to change the file extension (to .js) if you want to run those in a test environment.
IMAGES
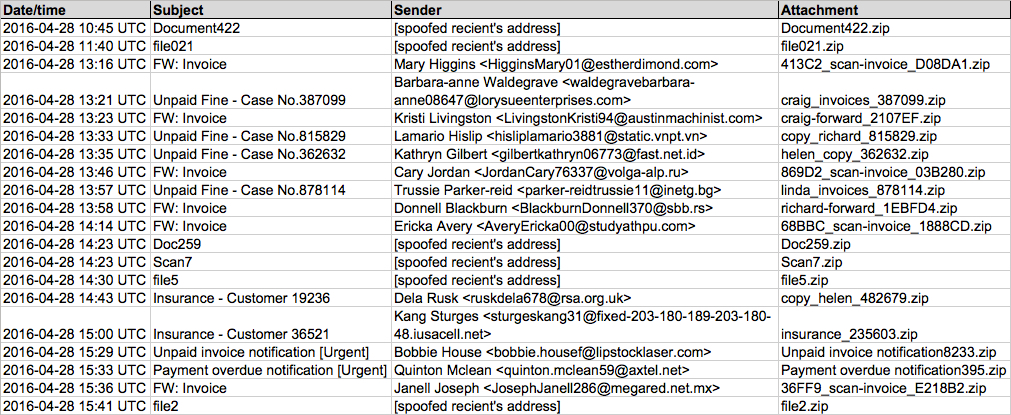
Shown above: Data from the .csv spreadsheet on 20 emails from today's malware hunt.
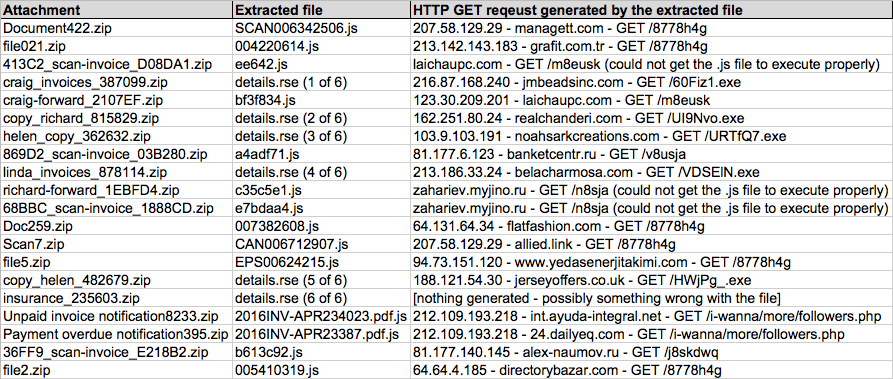
Shown above: Data from the .csv spreadsheet on 20 attachments from today's emails.
ZIP ARCHIVE CONTENTS
- 2016-04-28-email-tracker.csv (3,877 bytes)
- 2016-04-28-traffic-after-running-the-extracted-files.pcap (2,157,182 bytes)
- attachments/36FF9_scan-invoice_E218B2.zip (2,049 bytes)
- attachments/413C2_scan-invoice_D08DA1.zip (2,046 bytes)
- attachments/68BBC_scan-invoice_1888CD.zip (2,045 bytes)
- attachments/869D2_scan-invoice_03B280.zip (2,042 bytes)
- attachments/Doc259.zip (3,009 bytes)
- attachments/Document422.zip (3,016 bytes)
- attachments/Payment overdue notification395.zip (5,322 bytes)
- attachments/Scan7.zip (3,023 bytes)
- attachments/Unpaid invoice notification8233.zip (5,493 bytes)
- attachments/copy_helen_482679.zip (6,926 bytes)
- attachments/copy_richard_815829.zip (6,134 bytes)
- attachments/craig-forward_2107EF.zip (2,045 bytes)
- attachments/craig_invoices_387099.zip (5,424 bytes)
- attachments/file021.zip (3,019 bytes)
- attachments/file2.zip (3,039 bytes)
- attachments/file5.zip (3,034 bytes)
- attachments/helen_copy_362632.zip (5,733 bytes)
- attachments/insurance_235603.zip (6,575 bytes)
- attachments/linda_invoices_878114.zip (6,939 bytes)
- attachments/richard-forward_1EBFD4.zip (2,045 bytes)
- extracted-files/004220614.js (5,949 bytes)
- extracted-files/005410319.js (6,025 bytes)
- extracted-files/007382608.js (5,984 bytes)
- extracted-files/2016INV-APR23387.pdf.js (14,755 bytes)
- extracted-files/2016INV-APR234023.pdf.js (16,980 bytes)
- extracted-files/CAN006712907.js (5,989 bytes)
- extracted-files/EPS00624215.js (6,047 bytes)
- extracted-files/SCAN006342506.js (5,963 bytes)
- extracted-files/a4adf71.js (4,976 bytes)
- extracted-files/b613c92.js (4,983 bytes)
- extracted-files/bf3f834.js (4,978 bytes)
- extracted-files/c35c5e1.js (4,981 bytes)
- extracted-files/details-1-of-6.rse (17,339 bytes)
- extracted-files/details-2-of-6.rse (16,541 bytes)
- extracted-files/details-3-of-6.rse (20,042 bytes)
- extracted-files/details-4-of-6.rse (20,842 bytes)
- extracted-files/details-5-of-6.rse (23,436 bytes)
- extracted-files/details-6-of-6.rse (24,763 bytes)
- extracted-files/e7bdaa4.js (4,983 bytes)
- extracted-files/ee642.js (4,983 bytes)
- emails/2016-04-28-1045-UTC.eml (6,958 bytes)
- emails/2016-04-28-1140-UTC.eml (6,940 bytes)
- emails/2016-04-28-1316-UTC.eml (4,388 bytes)
- emails/2016-04-28-1321-UTC.eml (9,300 bytes)
- emails/2016-04-28-1323-UTC.eml (4,413 bytes)
- emails/2016-04-28-1333-UTC.eml (10,194 bytes)
- emails/2016-04-28-1335-UTC.eml (9,663 bytes)
- emails/2016-04-28-1346-UTC.eml (4,374 bytes)
- emails/2016-04-28-1357-UTC.eml (11,302 bytes)
- emails/2016-04-28-1358-UTC.eml (4,418 bytes)
- emails/2016-04-28-1414-UTC.eml (4,379 bytes)
- emails/2016-04-28-1423a-UTC.eml (6,909 bytes)
- emails/2016-04-28-1423b-UTC.eml (6,902 bytes)
- emails/2016-04-28-1430-UTC.eml (6,959 bytes)
- emails/2016-04-28-1443-UTC.eml (11,099 bytes)
- emails/2016-04-28-1500-UTC.eml (10,681 bytes)
- emails/2016-04-28-1529-UTC.eml (14,467 bytes)
- emails/2016-04-28-1533-UTC.eml (14,257 bytes)
- emails/2016-04-28-1536-UTC.eml (4,408 bytes)
- emails/2016-04-28-1541-UTC.eml (6,954 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware-sample-1-of-4.exe (237,568 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware-sample-2-of-4.exe (180,224 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware-sample-3-of-4.exe (179,712 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware-sample-4-of-4.exe (179,712 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware_HELP_instructions.bmp (3,578,902 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-04-28-Locky-ransomware_HELP_instructions.html (2,943 bytes)
Click here to return to the main page.
