2016-05-19 - LOCKY RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILE:
- 2016-05-19-Locky-ransomware-data.zip 952.6 kB (952,579 bytes)
NOTES:
- The Palo Alto Networks Unit 42 blog about Locky ransomware can be found here.
- Proofpoint's blog about Locky ransomware is available here.
EMAILS AND ATTACHMENTS
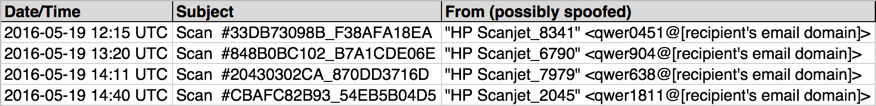
Shown above: Data from the .csv spreadsheet on 4 emails from today pushing Locky ransomware.
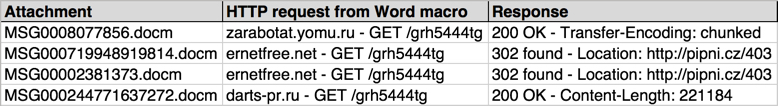
Shown above: Data from the .csv spreadsheet on 4 attachments from today's emails pushing Locky ransomware.
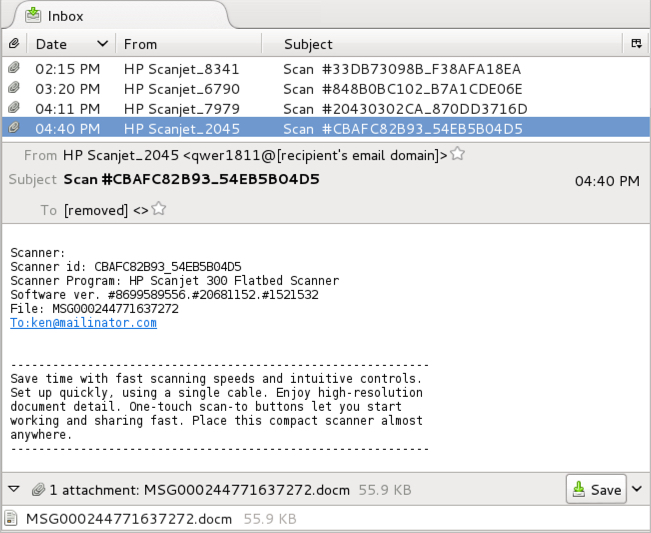
Shown above: Example from one of the emails.
TRAFFIC
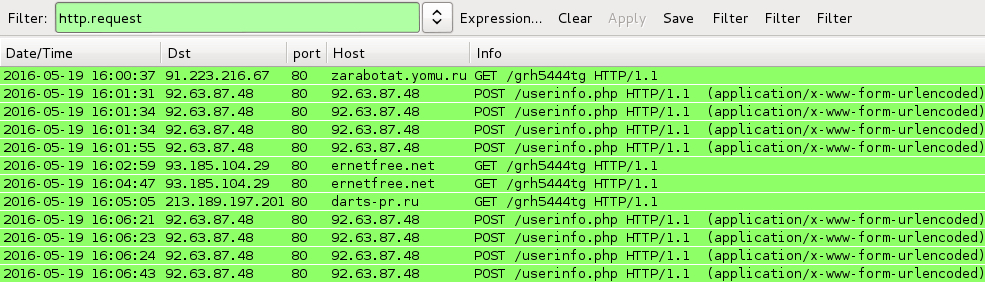
Shown above: Traffic from enabling macros on the .docm files, filtered in Wireshark.
HTTP REQUESTS FROM THE WORD MACROS:
- 91.223.216[.]67 port 80 - zarabotat.yomu[.]ru - GET /grh5444tg
- 93.185.104[.]29 port 80 - ernetfree[.]net - GET /grh5444tg
- 213.189.197[.]201 port 80 - darts-pr[.]ru - GET /grh5444tg
POST-INFECTION TRAFFIC FROM THE LOCKY RANSOMWARE SAMPLE:
- 92.63.87[.]48 port 80 - 92.63.87[.]48 - POST /userinfo.php
IMAGES
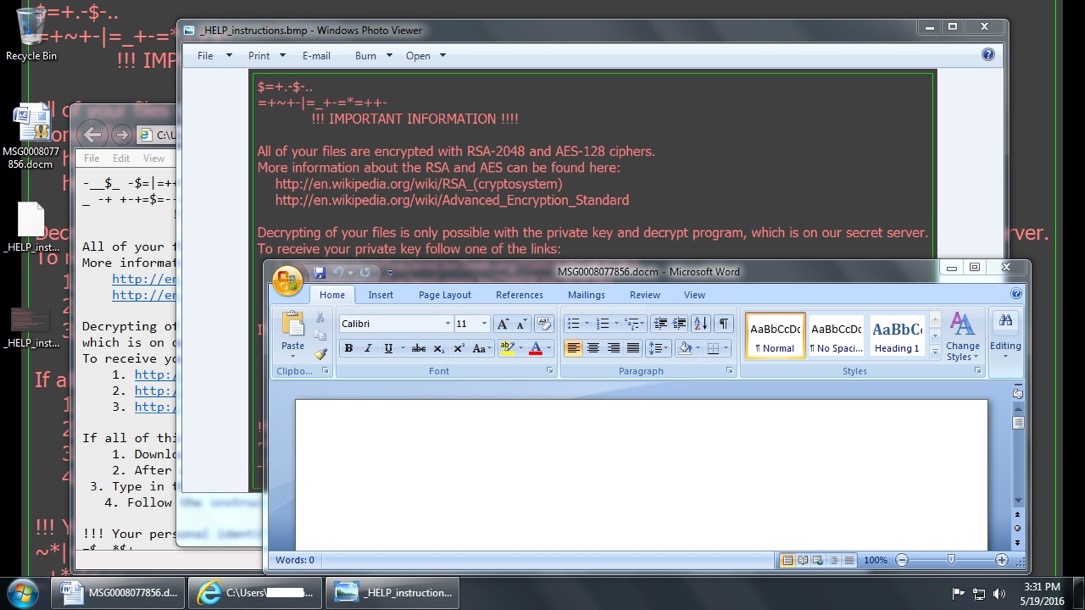
Shown above: Desktop of a Windows host after enabling macros on one of the .docm files from the emails.
ZIP ARCHIVE CONTENTS
- 2016-05-19-Locky-ransomware-email-tracker.csv (897 bytes)
- 2016-05-19-Locky-ransomware-infection-traffic.pcap (431,177 bytes)
- files-from-infected-host/2016-05-19-Locky-ransomware-sample.exe (221,184 bytes)
- files-from-infected-host/2016-05-19-Locky-ransomware_HELP_instructions.bmp (3,721,466 bytes)
- files-from-infected-host/2016-05-19-Locky-ransomware_HELP_instructions.html (9,749 bytes)
- attachments/MSG00002381373.docm (57,158 bytes)
- attachments/MSG000244771637272.docm (57,221 bytes)
- attachments/MSG000719948919814.docm (57,148 bytes)
- attachments/MSG0008077856.docm (57,243 bytes)
- emails/2016-05-19-email-pushing-Locky-ransomware-1215-UTC.eml (78,831 bytes)
- emails/2016-05-19-email-pushing-Locky-ransomware-1320-UTC.eml (78,7211 bytes)
- emails/2016-05-19-email-pushing-Locky-ransomware-1411-UTC.eml (78,719 bytes)
- emails/2016-05-19-email-pushing-Locky-ransomware-1440-UTC.eml (78,823 bytes)
Click here to return to the main page.
