2016-05-26 - ANGLER EK SENDS UPDATED VERSION OF CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-26-Angler-EK-sends-CryptXXX-ransomware-2-pcaps.zip 2.0 MB (2,027,744 bytes)
- 2016-05-26-Afraidgate-Angler-EK-sends-CryptXXX-ransomware.pcap (1,101,070 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-sends-CryptXXX-ransomware.pcap (1,115,419 bytes)
- 2016-05-26-Angler-EK-and-CryptXXX-ransomware-files.zip 466.3 kB (466,252 bytes)
- 2016-05-26-Afraidgate-Angler-EK-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-26-Afraidgate-Angler-EK-CryptXXX-ransomware-decrypt-instructions.html (5,715 bytes)
- 2016-05-26-Afraidgate-Angler-EK-CryptXXX-ransomware-decrypt-instructions.txt (987 bytes)
- 2016-05-26-Afraidgate-Angler-EK-landing-page.txt (102,905 bytes)
- 2016-05-26-Afraidgate-Angler-EK-payload-CryptXXX-ransomware.dll (176,128 bytes)
- 2016-05-26-Angler-EK-flash-exploit-vs-flash-21.0.0.213.swf (67,386 bytes)
- 2016-05-26-page-from-brookslake_com-with-injected-pseudoDarkleech-script.txt (52,364 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.html (5,715 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-CryptXXX-ransomware-decrypt-instructions.txt (990 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-landing-page.txt (102,831 bytes)
- 2016-05-26-pseudoDarkleech-Angler-EK-payload-CryptXXX-ransomware.dll (176,128 bytes)
NOTES:
- Proofpoint's blog posts so far about CryptXXX ransomware can be found here and here.
- Background on the pseudoDarkleech campaign is available here.
- Background on the Afraidgate campaign is here.
- Looks like CryptXXX ransomware has been updated. There are new artifacts and decryption instructions.
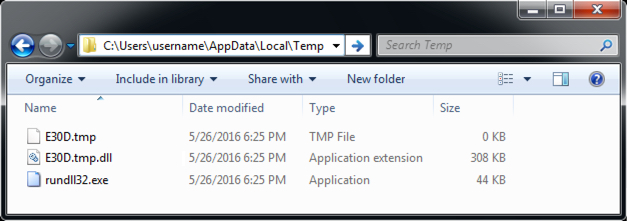
- This time, rundll32.exe is copied to the AppData\Local\Temp without being renamed as svchost.exe like it was before.
- I saw snort-based rules from Talos and EmergingThreats still triggering on callback traffic from this new version of CryptXXX ransomware.
- I'm sure someone will provide a more in-depth analysis of the malware. Meanwhile, you can view the screenshots in the images section of this blog entry.
Shown above: Example of a user's AppData\Local\Temp folder when Angler EK sends CryptXXX.
TRAFFIC
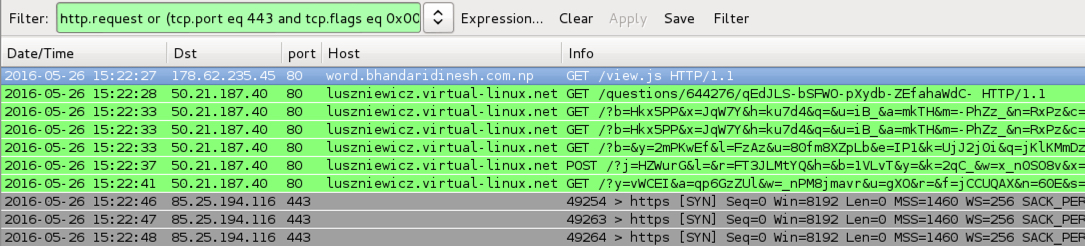
Shown above: Traffic from the Afraidgate Angler EK filtered in Wireshark using the filter: http.request or (tcp.port eq 443 and tcp.flags eq 0x0002).
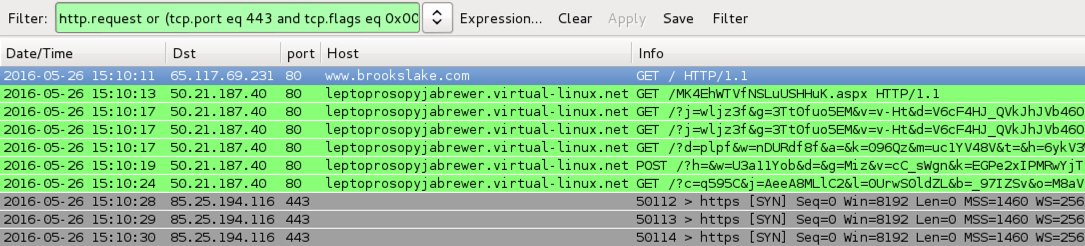
Shown above: Traffic from the pseudoDarkleech Angler EK filtered in Wireshark using the filter: http.request or (tcp.port eq 443 and tcp.flags eq 0x0002).
ASSOCIATED DOMAINS:
- 178.62.235[.]45 port 80 - word.bhandaridinesh[.]com[.]np - GET /view.js - Afraidgate campaign redirect
- 50.21.187[.]40 port 80 - luszniewicz.virtual-linux[.]net - Angler EK (Afraidgate campaign)
- 50.21.187[.]40 port 80 - leptoprosopyjabrewer.virtual-linux[.]net - Angler EK (pseudoDarkleech campaign)
- 85.25.194[.]116 port 443 - CryptXXX ransomware callback traffic (custom encoded, not SSL)
IMAGES
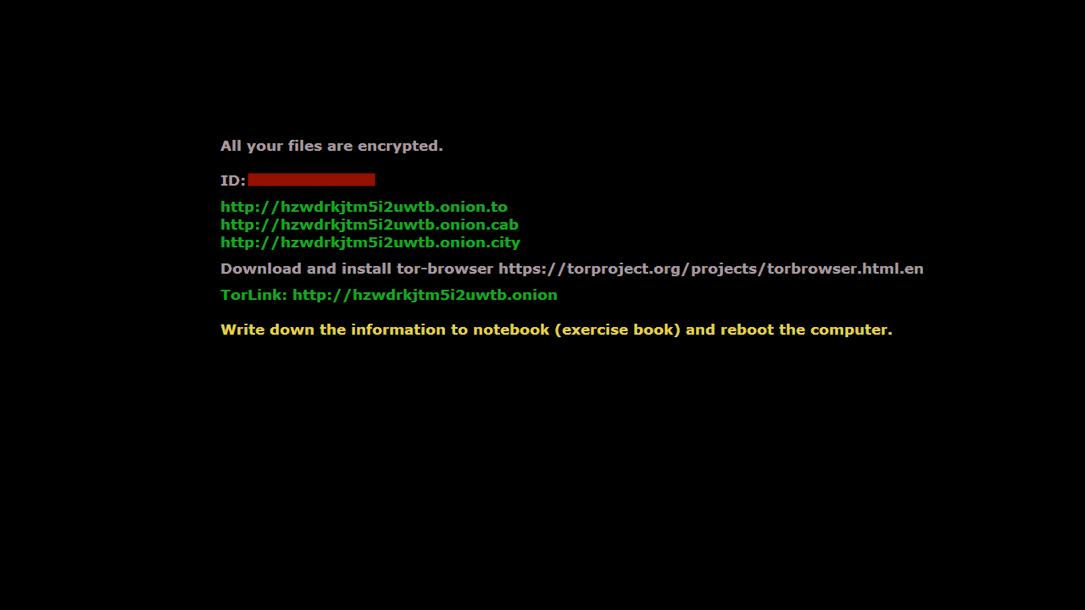
Shown above: Lock screen when the CryptXXX ransomware infection kicks in.
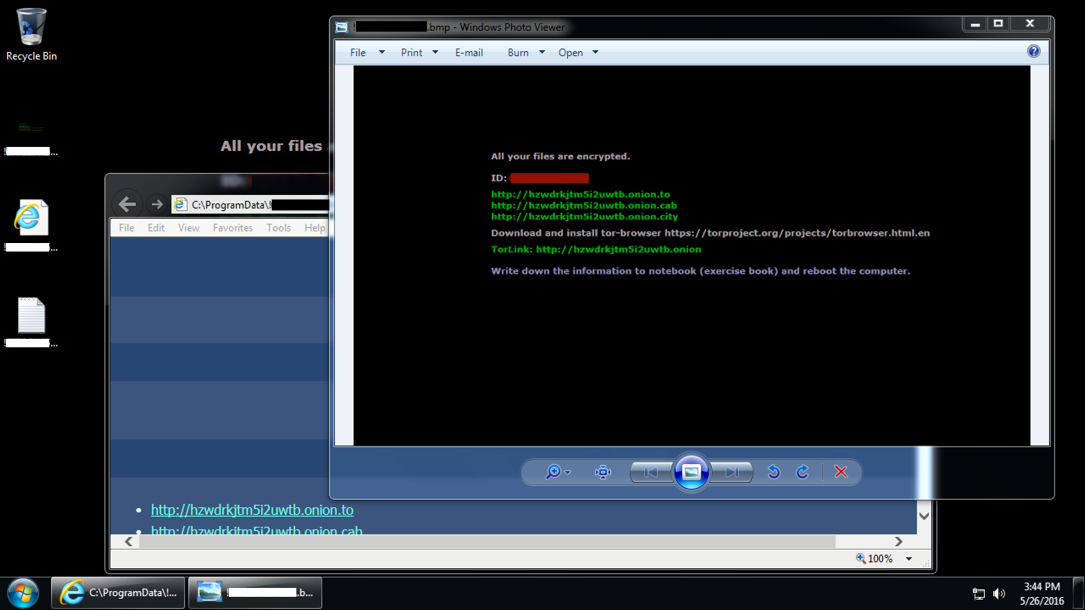
Shown above: HTML file to get to the decryption instructions.
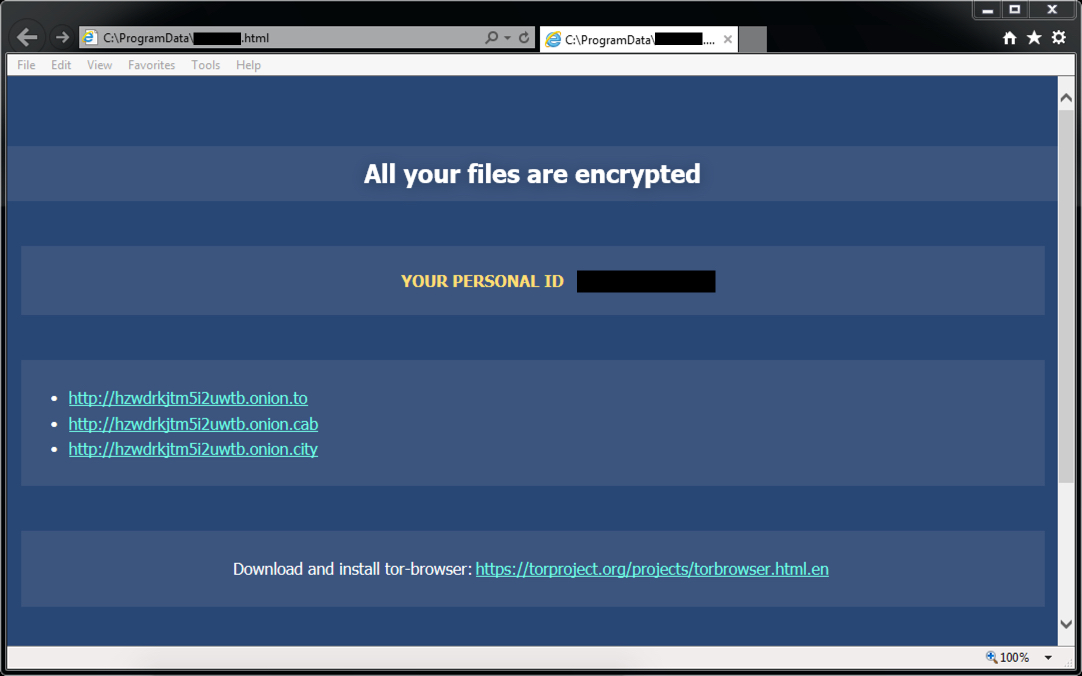
Shown above: Windows desktop when it was rebooted.
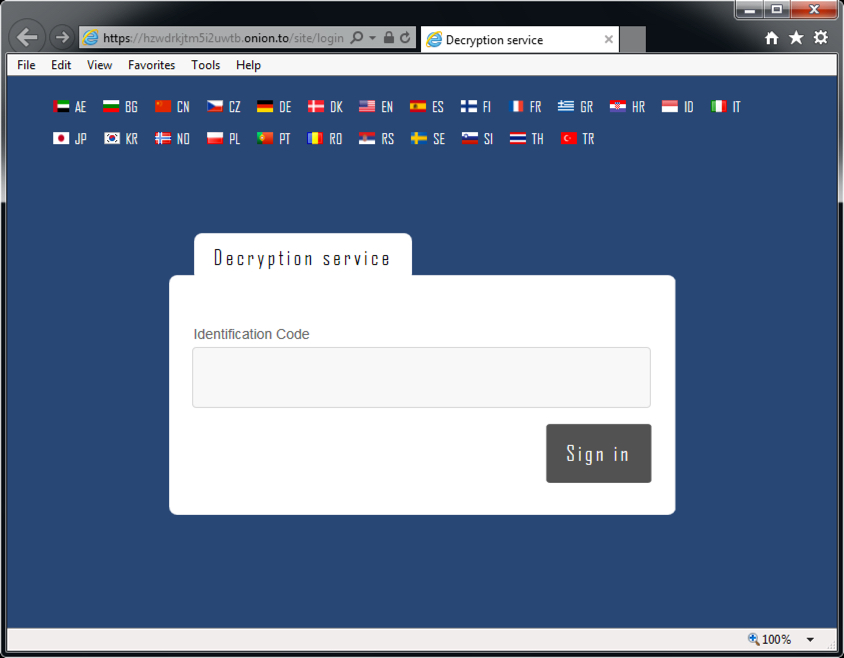
Shown above: Going to the site to pay the ransom, you'll have to enter your code.
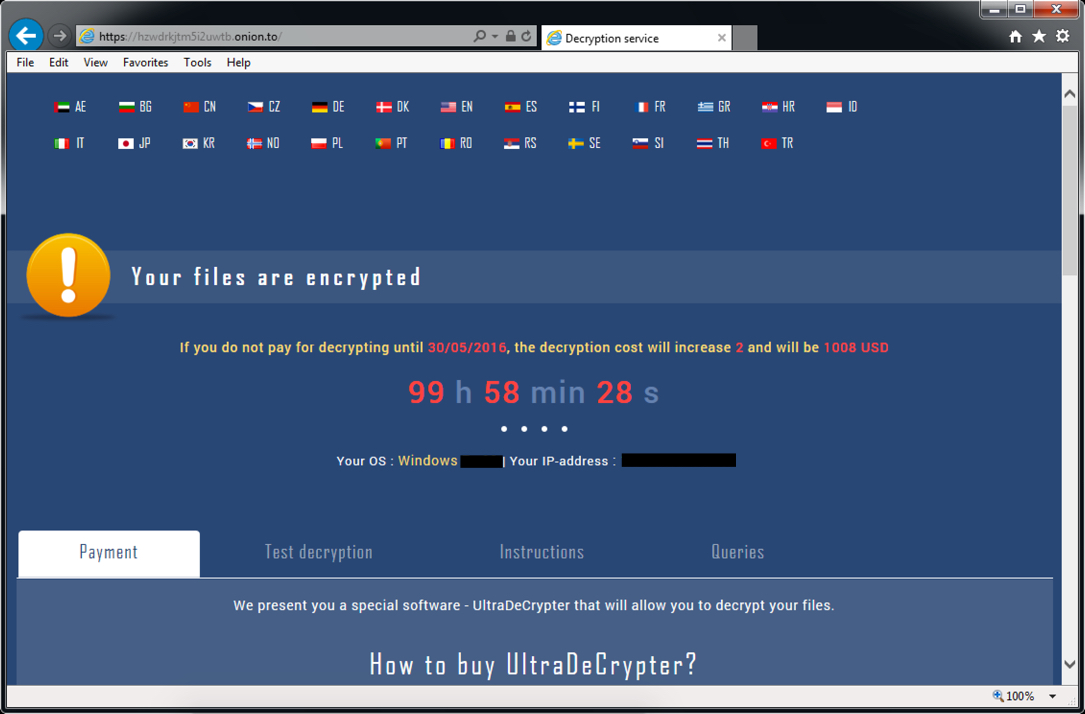
Shown above: Decryption instructions (part 1 of 3).
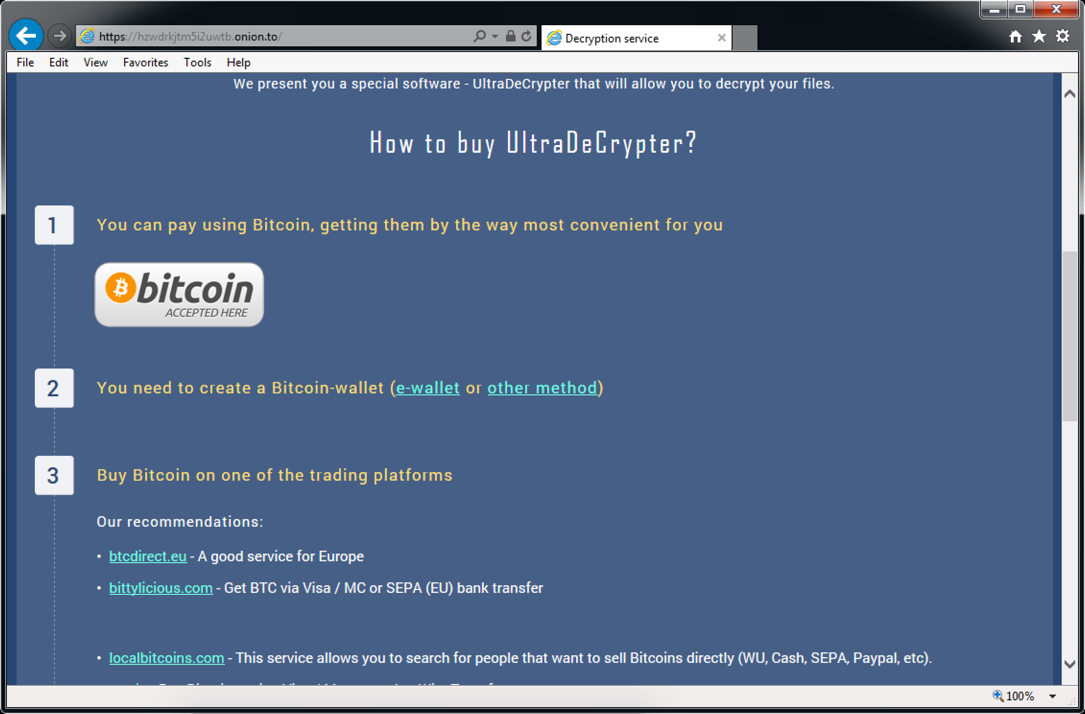
Shown above: Decryption instructions (part 2 of 3).
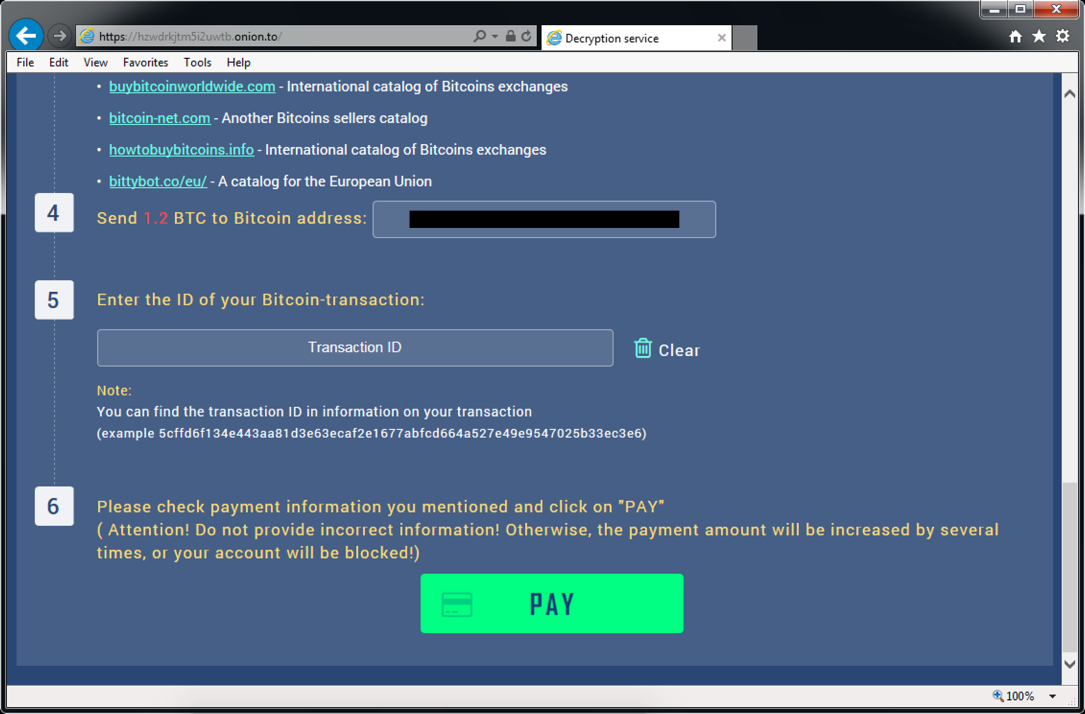
Shown above: Decryption instructions (part 3 of 3).
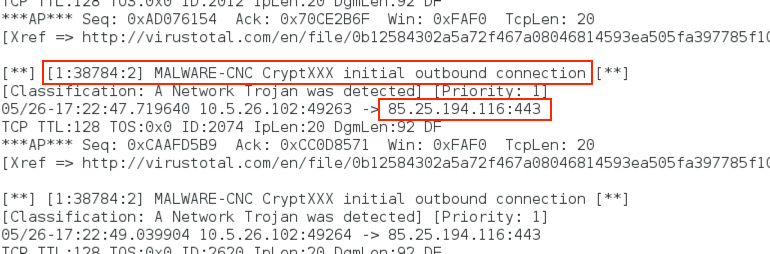
Shown above: Talos subscriber set signatures still cover callback traffic from the new CryptXXX ransomware.
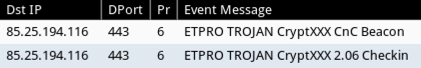
Shown above: ET PRO signatures also still cover callback traffic.
NOTE: I removed the identification code from the post-infection traffic in my pcaps. Because of that, I haven't been able to get any of the pcaps to trigger the above ETPRO alerts when using tcpreplay on Security Onion (with Suricata and the ETPRO ruleset). The above image shows CryptXXX ransomware alerts from post-infection traffic before I sanitized the pcap.
Click here to return to the main page.