2016-05-31 - MORE LOCKY RANSOMWARE (ALWAYS MORE LOCKY)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-31-Locky-ransomawre-infection-traffic-4-pcaps.zip 537.4 kB (537,394 bytes)
- 2016-05-31-Locky-ransomawre-infection-after-details_V9yGF.js.pcap (157,924 bytes)
- 2016-05-31-Locky-ransomawre-infection-after-details_gyo4a.js.pcap (193,258 bytes)
- 2016-05-31-Locky-ransomawre-infection-after-doc_scan_GKnaA.js.pcap (219,064 bytes)
- 2016-05-31-Locky-ransomawre-infection-after-scan_k9w7fm.js.pcap (219,207 bytes)
- 2016-05-31-files-from-Locky-ransomware-activity.zip 246.4 kB (246,379 bytes)
- 2016-05-31-Locky-ransomware-email-tracker.csv (659 bytes)
- files-from-an-infected-host/2016-05-31-Locky-ransomware-example.exe (181,760 bytes)
- files-from-an-infected-host/2016-05-31-Locky-ransomware_HELP_instructions.bmp (3,293,774 bytes)
- files-from-an-infected-host/2016-05-31-Locky-ransomware_HELP_instructions.html (9,355 bytes)
- email-attachments/caution_trevor_54614652.zip (5,879 bytes)
- email-attachments/copy_alan_14149553.zip (5,897 bytes)
- email-attachments/report_56098446.zip (5,864 bytes)
- email-attachments/security_69514117.zip (5,772 bytes)
- email-examples/2016-05-31-email-for-Locky-ransomware-0926-UTC.eml (9,914 bytes)
- email-examples/2016-05-31-email-for-Locky-ransomware-0956-UTC.eml (9,928 bytes)
- email-examples/2016-05-31-email-for-Locky-ransomware-1134-UTC.eml (9,657 bytes)
- email-examples/2016-05-31-email-for-Locky-ransomware-1158-UTC.eml (9,515 bytes)
- files-extracted-from-email-attachments/details_V9yGF.js (13,028 bytes)
- files-extracted-from-email-attachments/details_gyo4a.js (12,965 bytes)
- files-extracted-from-email-attachments/doc_scan_GKnaA.js (12,812 bytes)
- files-extracted-from-email-attachments/scan_k9w7fm.js (11,918 bytes)
EMAILS AND ATTACHMENTS

Shown above: Data from the .csv spreadsheet on 4 email samples from Tuesday 2016-05-31.
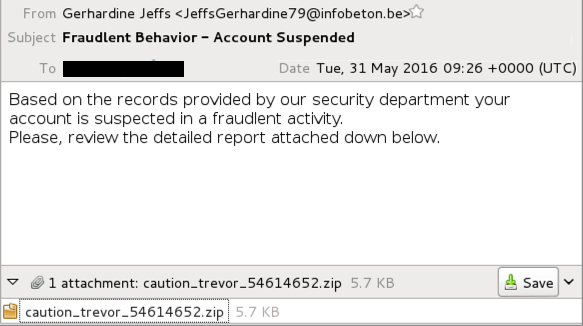
Shown above: Example of Fraudlent Behavior - Account Suspended email from
Tuesday 2016-05-31.
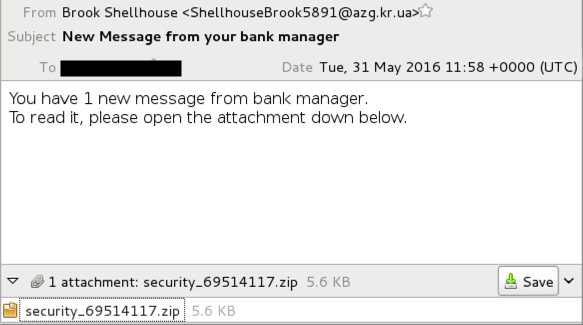
Shown above: Example of New Message from your bank manager email from
Tuesday 2016-05-31.
TRAFFIC
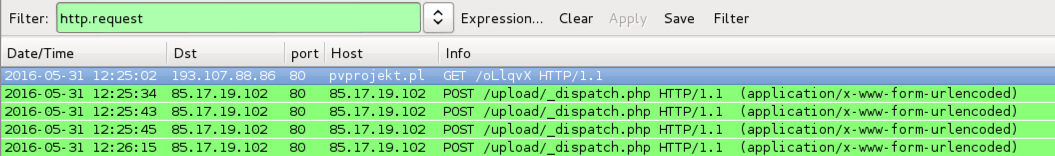
Shown above: Locky ransomware infection traffic generated from the first email attachment filtered in Wireshark.
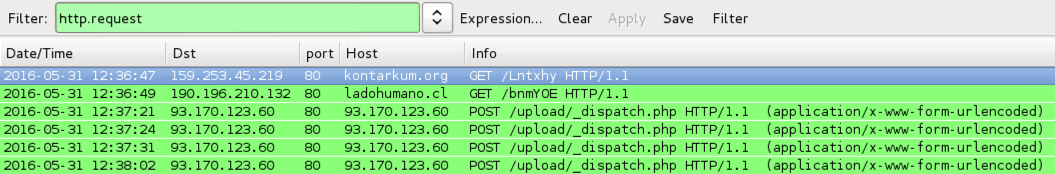
Shown above: Locky ransomware infection traffic generated from the second email attachment filtered in Wireshark.
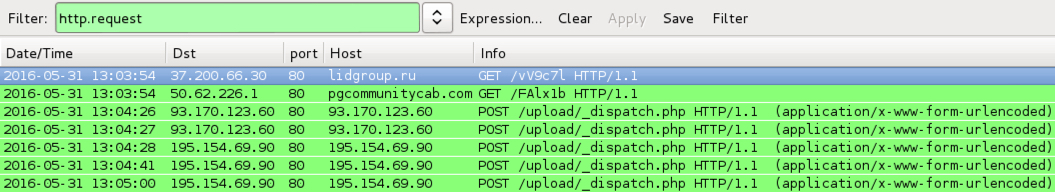
Shown above: Locky ransomware infection traffic generated from the third email attackment filtered in Wireshark.
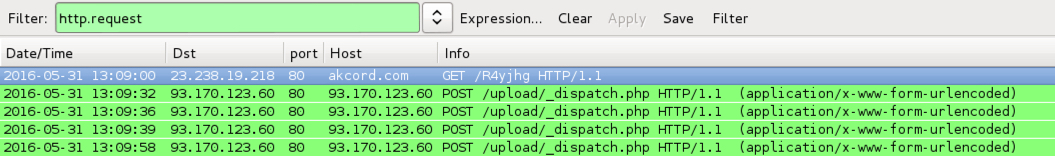
Shown above: Locky ransomware infection traffic generated from the fourth email attachment filtered in Wireshark.
HTTP REQUESTS FORM .JS FILES TO DOWNLOAD THE LOCKY RANSOMWARE EXE:
- 23.238.19[.]218 port 80 - akcord[.]com - GET /R4yjhg
- 37.200.66[.]30 port 80 - lidgroup[.]ru - GET /vV9c7l
- 50.62.226[.]1 port 80 - pgcommunitycab[.]com - GET /FAlx1b
- 159.253.45[.]219 port 80 - kontarkum[.]org - GET /Lntxhy
- 190.196.210[.]132 port 80 - ladohumano[.]cl - GET /bnmYOE
- 193.107.88[.]86 port 80 - pvprojekt[.]pl - GET /oLlqvX
POST-INFECTION TRAFFIC FROM THE LOCKY RANSOMWARE EXE:
- 85.17.19[.]102 port 80 - 85.17.19[.]102 - POST /upload/_dispatch.php
- 93.170.123[.]60 port 80 - 93.170.123[.]60 - POST /upload/_dispatch.php
- 195.154.69[.]90 port 80 - 195.154.69[.]90 - POST /upload/_dispatch.php
IMAGES
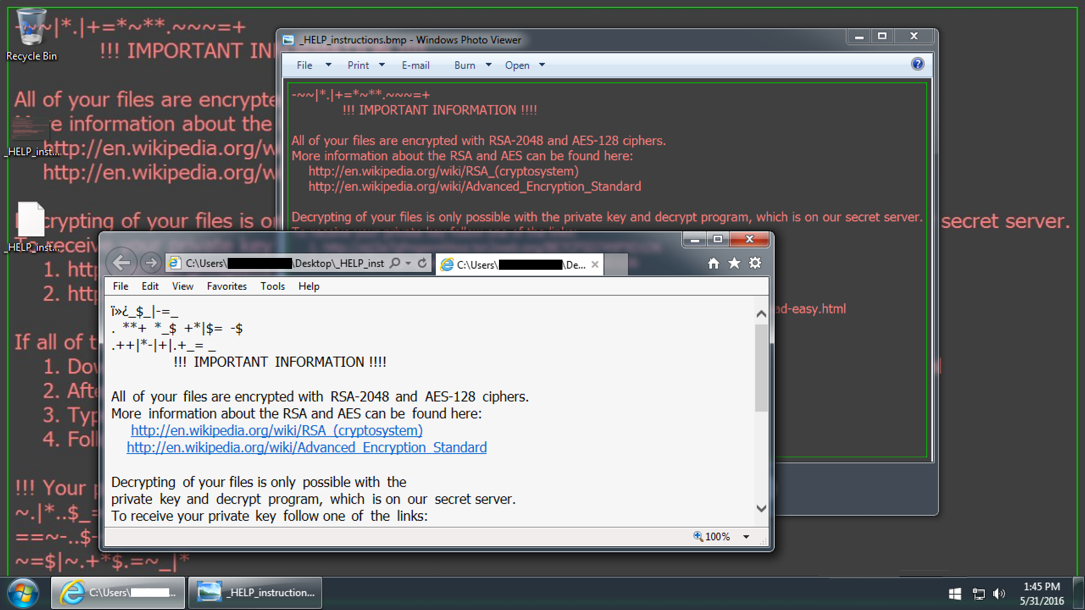
Shown above: Windows computer's desktop after one of today's Locky ransomware infections.
Click here to return to the main page.
