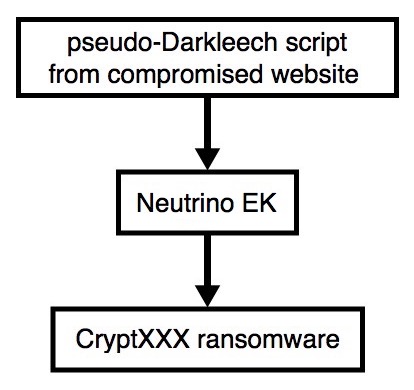
2016-06-17 - PSEUDO-DARKLEECH NEUTRINO EK FROM 45.63.25[.]106 SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-17-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-2-pcaps.zip 2.1 MB (2,123,214 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-ex.technor_com.pcap (990,812 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-nuvon_com.pcap (1,359,082 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-and-CryptXXX-ransomware-files.zip 460.7 kB (460,692 bytes)
- 2016-06-17-CryptXXX-ransomware-decrypt-instructions.bmp (3686454 bytes)
- 2016-06-17-CryptXXX-ransomware-decrypt-instructions.html (36201 bytes)
- 2016-06-17-CryptXXX-ransomware-decrypt-instructions.txt (1755 bytes)
- 2016-06-17-page-from-ex.technor_com-with-injected-pseudoDarkleech-script (33092 bytes)
- 2016-06-17-page-from-nuvon_com-with-injected-pseudoDarkleech-script.txt (40157 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-flash-exploit-after-ex.technor_com.swf (79872 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-flash-exploit-after-nuvon_com.swf (79871 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-landing-page-after-ex.technor_com.txt (841 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-landing-page-after-nuvon_com.txt (805 bytes)
- 2016-06-17-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (526336 bytes)
BACKGROUND INFO:
- A PaloAlto Network blog post with background on the pseudoDarkleech campaign: link.
- An ISC diary I wrote about pseudo-Darkleech causing Angler EK/Bedep/CryptXXX infections: link.
- The latest Proofpoint post about CryptXXX ransomware: link.
Shown above: Flowchart for today's infection traffic.
TRAFFIC
ASSOCIATED DOMAINS:
- 45.63.25[.]106 port 80 - clyburnjtrennten.japaneseknotweedremovals[.]com - Neutrino EK
- 188.0.236[.]7 port 443 - CryptXXX ransomware callback (attempted TCP connections, no response)
- 85.25.194[.]116 port 443 - CryptXXX ransomware callback traffic
IMAGES
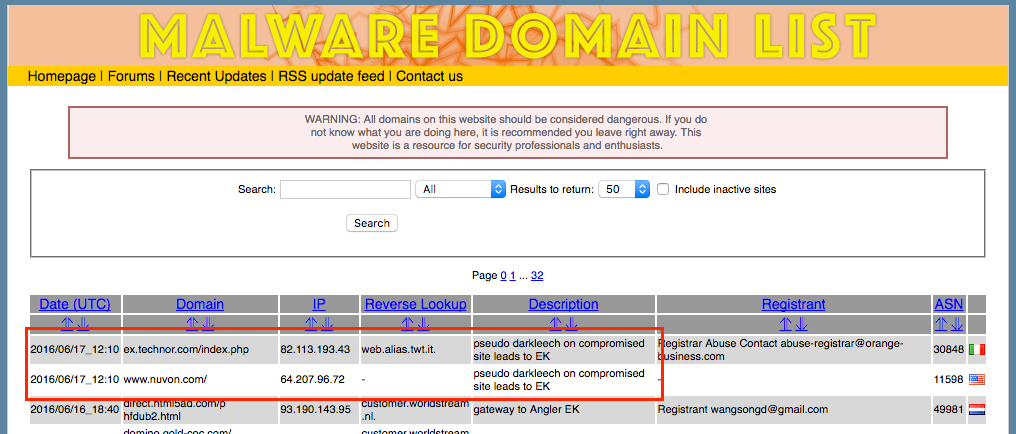
Shown above: What I found on Malware Domain List earlier today [2025 note: Site is no longer online].
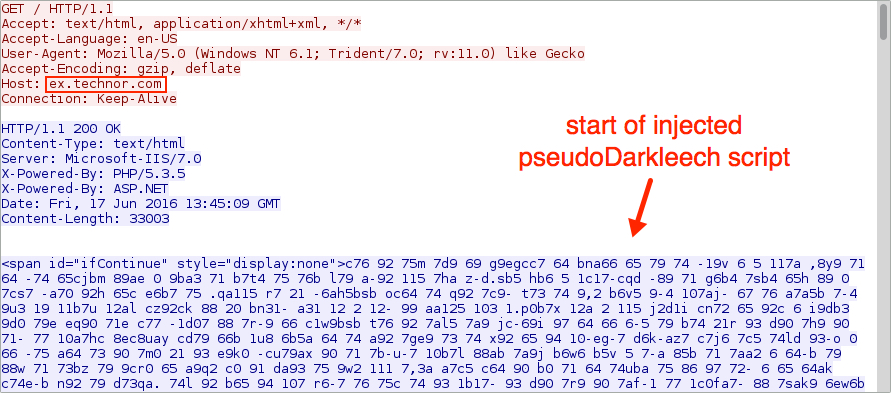
Shown above: HTTP GET request to the first website returns pseudoDarkleech script.
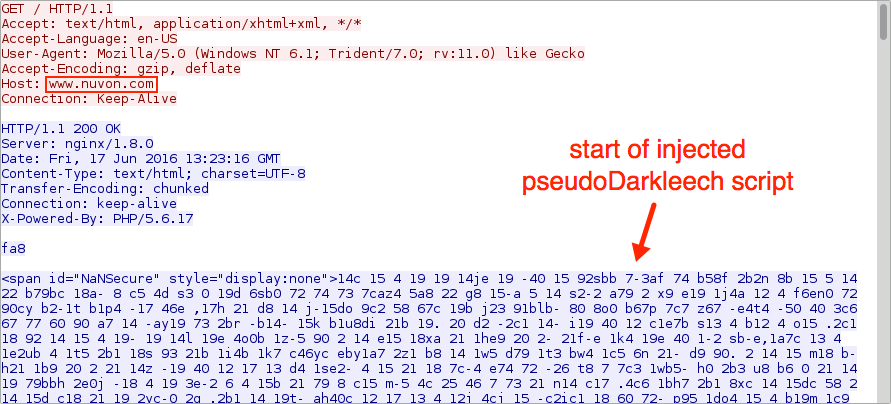
Shown above: HTTP GET request to the second website returns pseudoDarkleech script.
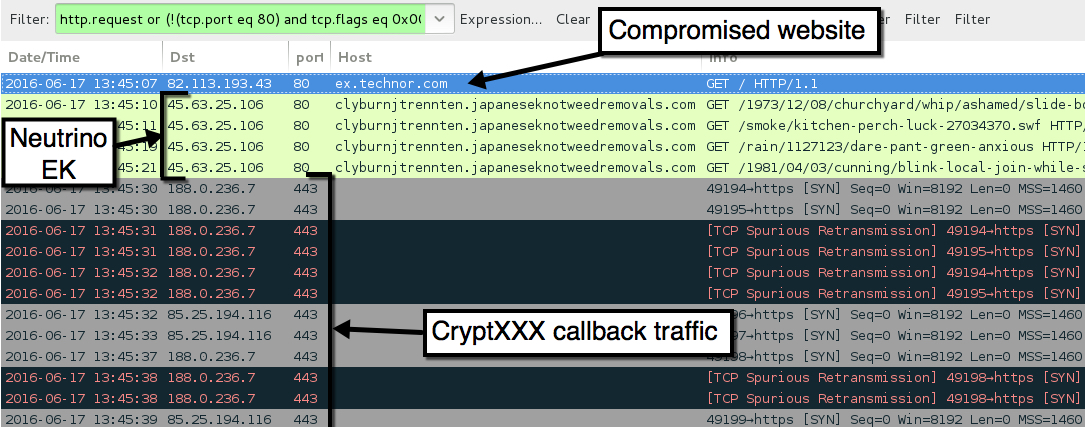
Shown above: First pcap of the traffic filtered in Wireshark.
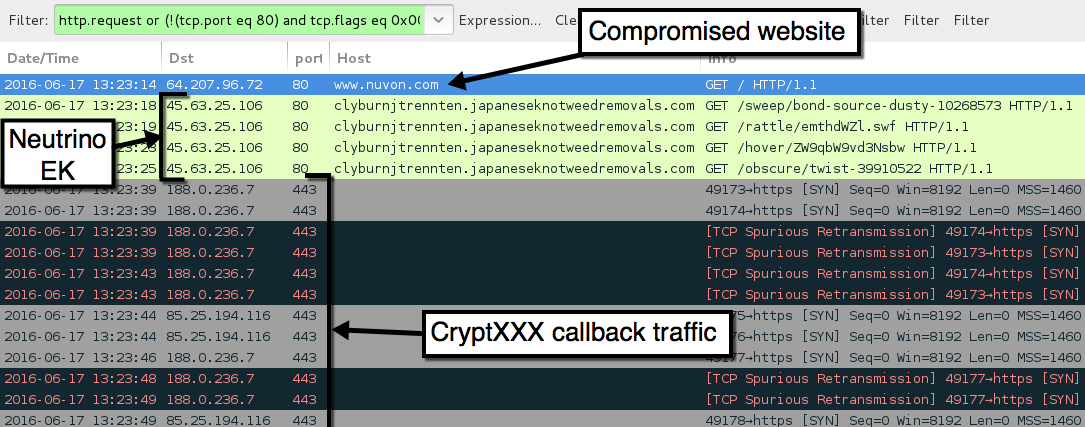
Shown above: Second pcap of the traffic filtered in Wireshark.
Click here to return to the main page.