2016-06-24 - PSEUDO-DARKLEECH NEUTRINO EK SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-24-pseudoDarkleech-Neutrino-EK-2-pcaps.zip 2.4 MB (2,412,513 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-after-fiocchidiriso_com.pcap (1,170,037 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-after-sunlait_com.pcap (1,390,485 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-malware-and-artifacts.zip 885.2 kB (885,225 bytes)
- 2016-06-24-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-24-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-24-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
- 2016-06-24-page-from-fiocchidiriso_com-with-injected-pseudoDarkleech-script.txt (16,008 bytes)
- 2016-06-24-page-from-sunlait_com-with-injected-pseudoDarkleech-script.txt (79,532 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-flash-exploit-after-fiocchidiriso_com.swf (81,798 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-flash-exploit-after-sunlait_com.swf (81,798 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-landing-page-after-fiocchidiriso_com.txt (1,034 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-landing-page-after-sunlait_com.txt (1,112 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-after-fiocchidiriso_com.dll (362,496 bytes)
- 2016-06-24-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware-after-sunlait_com.dll (5329,92 bytes)
NOTES:
- Shout out to MalwareDomainList and @BroadAnalysis for information on the compromised websites for today's infections.
BACKGROUND INFO:
- A PaloAlto Networks Unit 42 blog post I wrote on exploit kit (EK) fundamentals: link.
- A PaloAlto Networks Unit 42 blog post I wrote with background on the pseudoDarkleech campaign: link.
- One of many posts about Angler EK disappearing and Neutrino EK filling in as of June 2016 (this one from the MalwareBytes Blog): link.
- A recent Proofpoint post about CryptXXX ransomware: link.
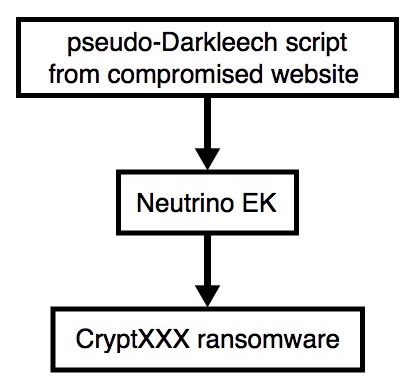
Shown above: Flowchart for today's infection traffic.
TRAFFIC
ASSOCIATED DOMAINS:
- 136.243.126[.]122 port 80 - pozwalajacehevosvoimien.drauk[.]co[.]uk - Neutrino EK from first pcap at 14:40 UTC
- 184.154.146[.]157 port 80 - natuurgenot.drauk[.]com - Neutrino EK from second pcap at 20:55 UTC
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic
IMAGES
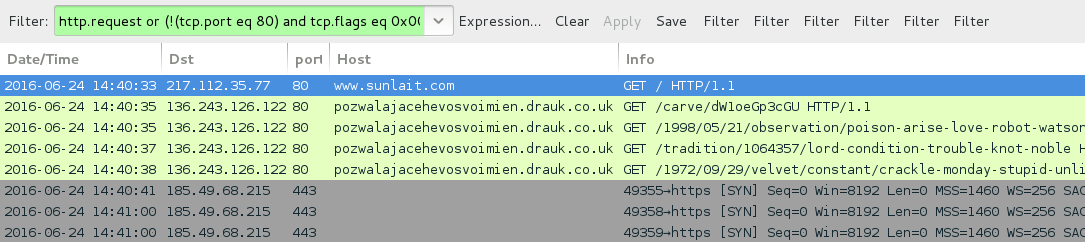
Shown above: Traffic from the first pcap filtered in Wireshark. Filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
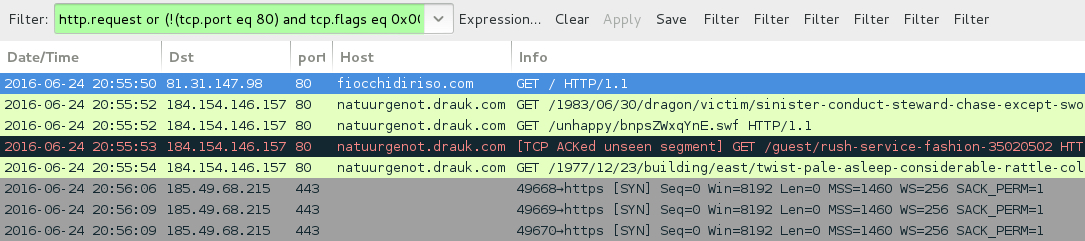
Shown above: Traffic from the second pcap filtered in Wireshark.
Click here to return to the main page.