2016-06-27 - LOCKY RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-27-Locky-ransomware-data.zip 2.5 MB (2,527,088 bytes)
- 2016-06-27-Locky-ransomware-email-tracker.csv (1,889 bytes)
- 2016-06-27-Locky-ransomware-infection-traffic.pcap (2,630,328 bytes)
- attachments/alan_updated_doc_759174.zip (7,370 bytes)
- attachments/aron_updated_178841.zip (7,606 bytes)
- attachments/colin_updated_056106.zip (7,369 bytes)
- attachments/linda_updated_435835.zip (7,322 bytes)
- attachments/lyn_updated_doc_240360.zip (7,303 bytes)
- attachments/ryan_updated_doc_473239.zip (7,472 bytes)
- attachments/tim_updated_doc_551787.zip (7,666 bytes)
- attachments/update_greg_015676.zip (7,361 bytes)
- attachments/update_john_901036.zip (7,675 bytes)
- attachments/update_phil_430422.zip (7,379 bytes)
- attachments/update_simon_936862.zip (7,142 bytes)
- attachments/wendy_updated_246995.zip (7,428 bytes)
- emails/2016-06-27-Locky-ransomware-email-2126-UTC.eml (11,022 bytes)
- emails/2016-06-27-Locky-ransomware-email-2135-UTC.eml (10,955 bytes)
- emails/2016-06-27-Locky-ransomware-email-2153-UTC.eml (10,691 bytes)
- emails/2016-06-27-Locky-ransomware-email-2217-UTC.eml (10,923 bytes)
- emails/2016-06-27-Locky-ransomware-email-2227-UTC.eml (10,862 bytes)
- emails/2016-06-27-Locky-ransomware-email-2231-UTC.eml (10,951 bytes)
- emails/2016-06-27-Locky-ransomware-email-2232-UTC.eml (10,872 bytes)
- emails/2016-06-27-Locky-ransomware-email-2236-UTC.eml (10,947 bytes)
- emails/2016-06-27-Locky-ransomware-email-2240-UTC.eml (11,344 bytes)
- emails/2016-06-27-Locky-ransomware-email-2305-UTC.eml (11,089 bytes)
- emails/2016-06-27-Locky-ransomware-email-2315-UTC.eml (11,361 bytes)
- emails/2016-06-27-Locky-ransomware-email-2325-UTC.eml (11,275 bytes)
- extracted-files/swift 24a2.js (69,397 bytes)
- extracted-files/swift 352c.js (69,284 bytes)
- extracted-files/swift 4f1a.js (69,564 bytes)
- extracted-files/swift 58c8.js (69,575 bytes)
- extracted-files/swift 5cd0.js (70,926 bytes)
- extracted-files/swift 822.js (69,627 bytes)
- extracted-files/swift 881a.js (72,194 bytes)
- extracted-files/swift 899f.js (67,383 bytes)
- extracted-files/swift c9eb.js (70,097 bytes)
- extracted-files/swift cc9.js (69,573 bytes)
- extracted-files/swift ea2.js (71,614 bytes)
- extracted-files/swift eb18.js (71,333 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-06-27-Locky-ransomware-decryption-instructions.bmp (4,149,158 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-06-27-Locky-ransomware-decryption-instructions.html (8,973 bytes)
- Locky-ransomware-files-from-an-infected-host/2016-06-27-Locky-ransomware-sample.exe (165,888 bytes)
NOTES:
- These emails are from the same wave of emails reported on Dynamoo's Blog earlier today at:
- Which is the same type of email reported last week by Proofpoint after Locky ransomware came back:
EMAILS AND ATTACHMENTS
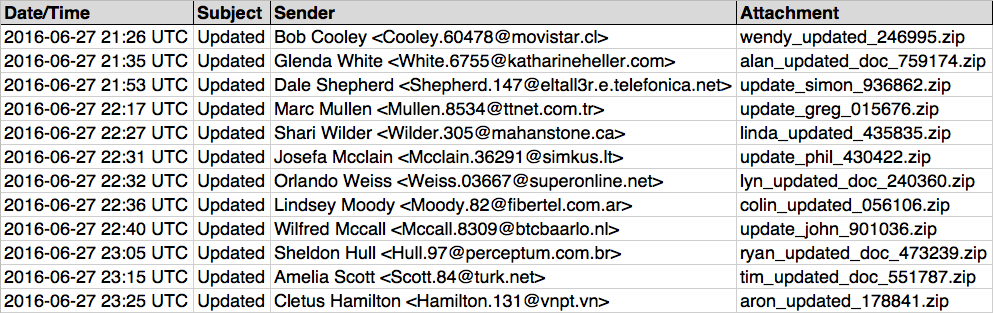
Shown above: Data from the .csv spreadsheet on 12 email samples from Monday 2016-06-27.
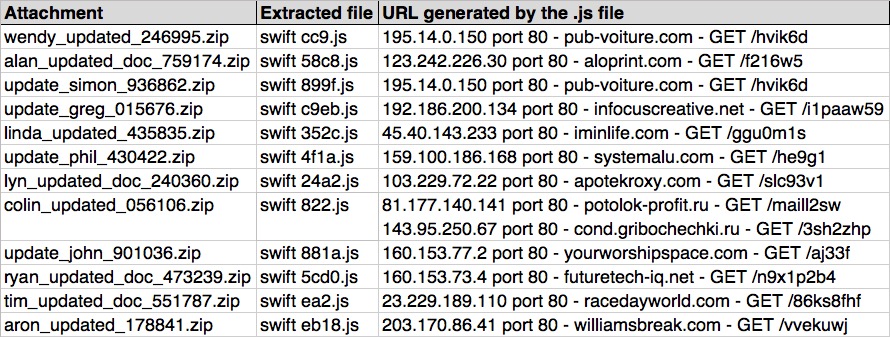
Shown above: Data from the .csv spreadsheet on the 12 email attachments from Monday 2016-06-27.
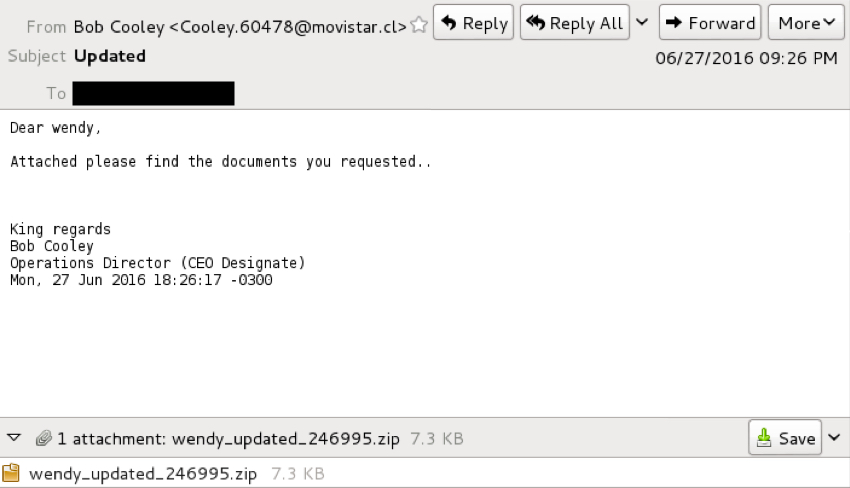
Shown above: An example of the text from one of the emails.
TRAFFIC
HTTP REQUESTS FROM THE .JS FILES TO DOWNLOAD LOCKY RANSOMWARE:
- 23.229.189[.]110 port 80 - racedayworld[.]com - GET /86ks8fhf
- 45.40.143[.]233 port 80 - iminlife[.]com - GET /ggu0m1s
- 81.177.140[.]141 port 80 - potolok-profit[.]ru - GET /maill2sw
- 103.229.72[.]22 port 80 - apotekroxy[.]com - GET /slc93v1
- 123.242.226[.]30 port 80 - aloprint[.]com - GET /f216w5
- 143.95.250[.]67 port 80 - cond.gribochechki[.]ru - GET /3sh2zhp
- 159.100.186[.]168 port 80 - systemalu[.]com - GET /he9g1
- 160.153.73[.]4 port 80 - futuretech-iq[.]net - GET /n9x1p2b4
- 160.153.77[.]2 port 80 - yourworshipspace[.]com - GET /aj33f
- 192.186.200[.]134 port 80 - infocuscreative[.]net - GET /i1paaw59
- 195.14.0[.]150 port 80 - pub-voiture[.]com - GET /hvik6d
- 203.170.86[.]41 port 80 - williamsbreak[.]com - GET /vvekuwj
POST-INFECTION CALLBACK FROM TODAY'S LOCKY RANSOMWARE SAMPLE:
- 109.234.35[.]71 port 80 - 109.234.35[.]71 - POST /upload/_dispatch.php
- 185.146.169[.]16 port 80 - 185.146.169[.]16 - POST /upload/_dispatch.php
- 195.123.209[.]227 port 80 - 195.123.209[.]227 - POST /upload/_dispatch.php
- 217.12.223[.]89 port 80 - 217.12.223[.]89 - POST /upload/_dispatch.php
IMAGES
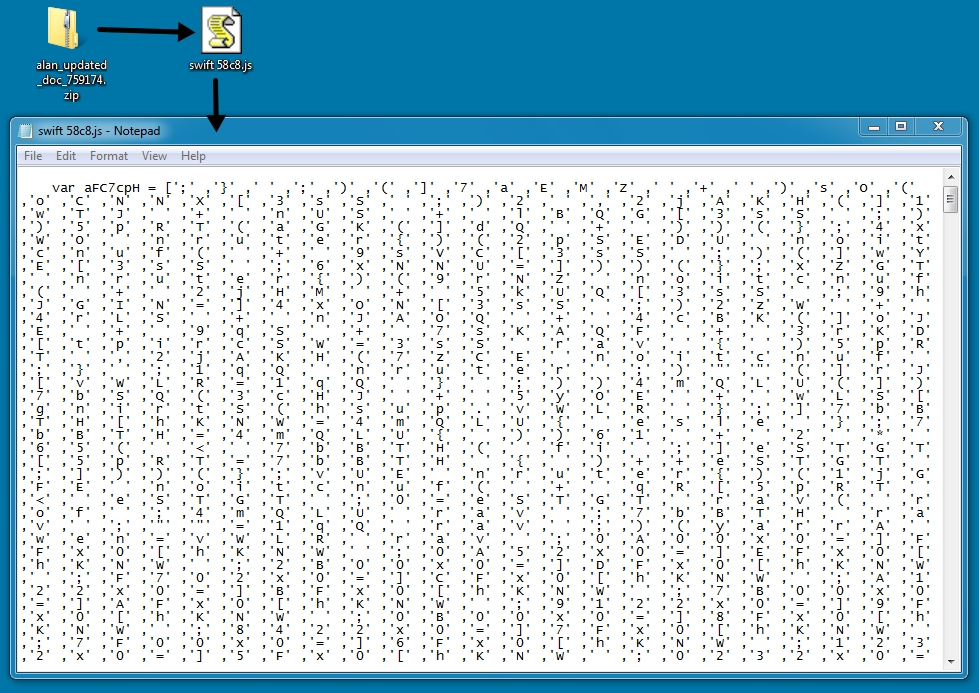
Shown above: From zip archive to looking at the text of the extracted .js file.
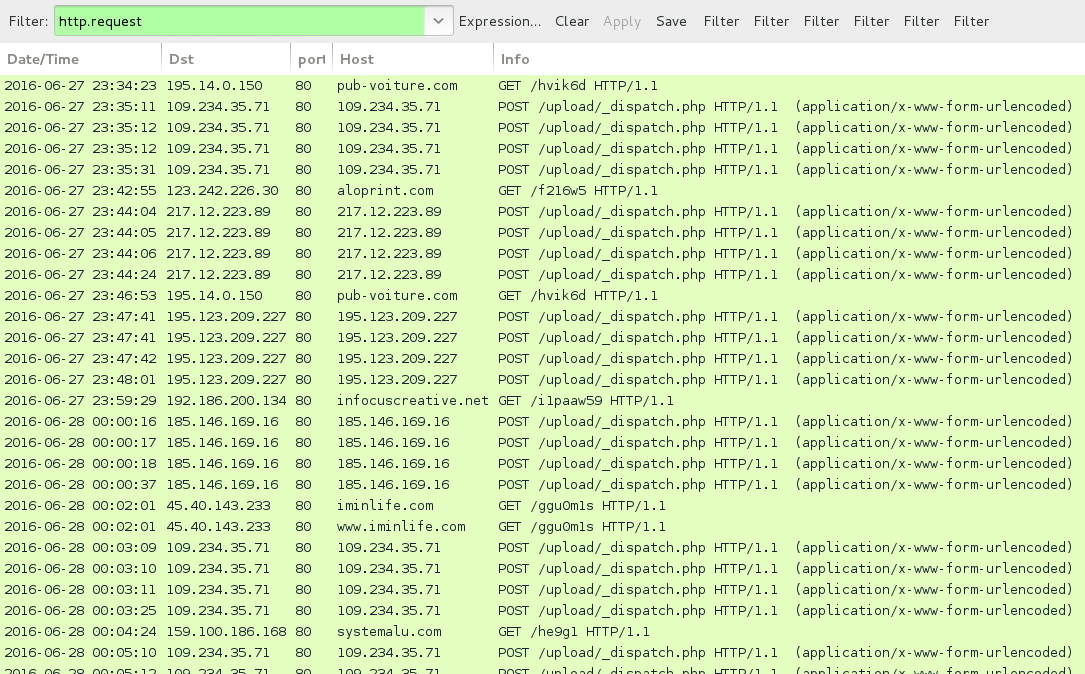
Shown above: Traffic from some of today's Locky ransomware infections filtered in Wireshark.
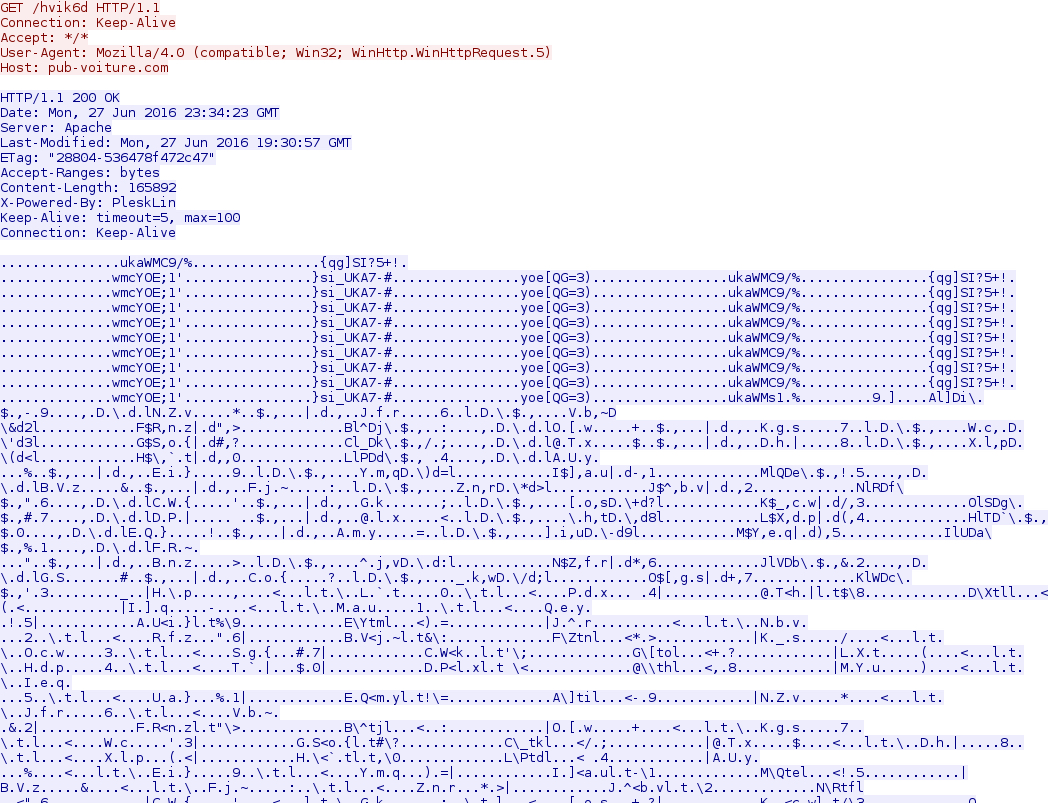
Shown above: Locky ransomware being downloaded by one of the .js files (Note: Locky is obfuscated here).
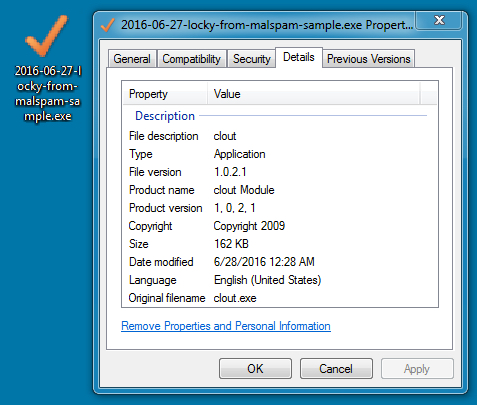
Shown above: An example of Locky ransomware after it was decoded on a local host.
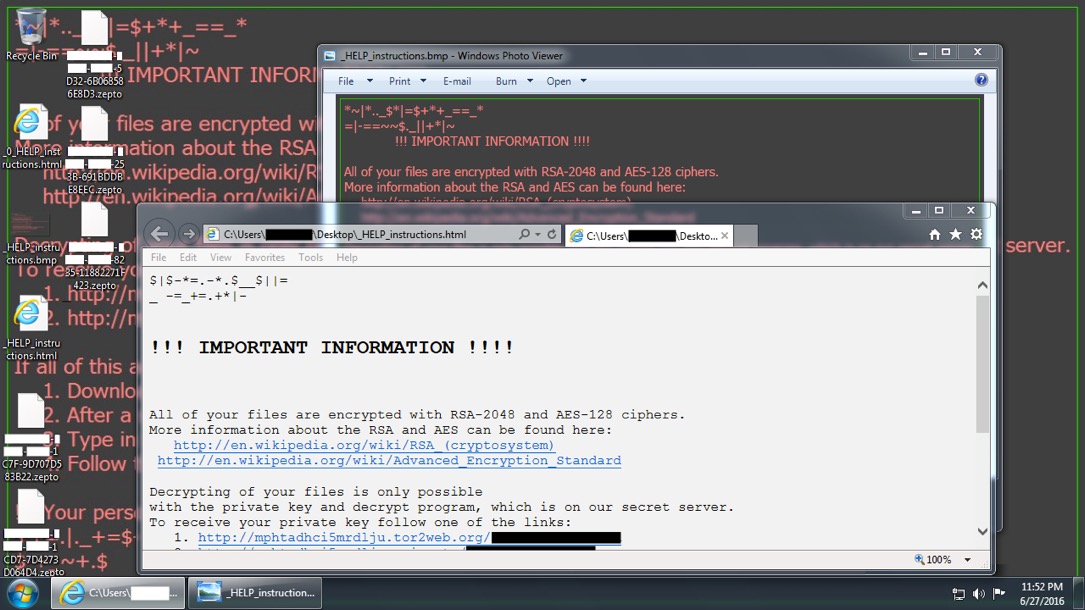
Shown above: A Windows computer's desktop after one of today's Locky ransomware infections.
Click here to return to the main page.
