2016-06-28 - EK DATA DUMP (NEUTRINO EK, RIG EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-28-EK-data-dump-5-pcaps.zip 8.0 MB (7,974,307 bytes)
- 2016-06-28-Neutrino-EK-after-mu-media_co_uk.pcap (5,521,238 bytes)
- 2016-06-28-Neutrino-EK-after-tonyattwood_com_au.pcap (413,103 bytes)
- 2016-06-28-Rig-EK-after-monavocatparis_fr.pcap (200,657 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-after-airbornehydrography_com_pcap (1,133,721 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-after-gennaroespositomilano_it.pcap (1,385,884 bytes)
- 2016-06-28-EK-data-dump-malware-and-artifacts.zip 1.0 MB (1,047,460 bytes)
- 2016-06-28-Neutrino-EK-flash-exploit-after-mu-media_co_uk.swf (87,014 bytes)
- 2016-06-28-Neutrino-EK-flash-exploit-after-tonwyattwood_com_au.swf (90,037 bytes)
- 2016-06-28-Neutrino-EK-landing-page-after-mu-media_co_uk.txt (1,156 bytes)
- 2016-06-28-Neutrino-EK-landing-page-after-tonwyattwood_com_au.txt (1,003 bytes)
- 2016-06-28-Neutrino-EK-payload-Gootkit-after-mu-media_co_uk.exe (238,592 bytes)
- 2016-06-28-Neutrino-EK-payload-Gootkit-after-tonwyattwood_com_au.exe (238,592 bytes)
- 2016-06-28-Rig-EK-flash-exploit-after-monavocatparis_fr.swf (24,413 bytes)
- 2016-06-28-Rig-EK-landing-page-after-monavocatparis_fr.txt (5,304 bytes)
- 2016-06-28-Rig-EK-payload-after-monavocatparis_fr.exe (151,552 bytes)
- 2016-06-28-page-from-airbornehydrography_com-with-injected-pseudoDarkleech-script.txt (15,473 bytes)
- 2016-06-28-page-from-gennaroespositomilano_it-with-injected-pseudoDarkleech-script.txt (32,141 bytes)
- 2016-06-28-page-from-monavocatparis_fr-with-injected-script-pointing-to-gate.txt (12,860 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-flash-exploit-after-airbornehydrography_com.swf (86,380 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-flash-exploit-after-gennaroespositomilano_it.swf (89,145 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-landing-page-after-airbornehydrography_com.txt (1,153 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-landing-page-after-gennaroespositomilano_it.txt (1,012 bytes)
- 2016-06-28-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (500,224 bytes)
- 2016-06-28-CryptXXX-ransomware-decrypt-instructions.bmp (3,686,454 bytes)
- 2016-06-28-CryptXXX-ransomware-decrypt-instructions.html (36,201 bytes)
- 2016-06-28-CryptXXX-ransomware-decrypt-instructions.txt (1,755 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
- 85.25.95[.]39 port 80 - realstatistics[.]info - gate leading to Neutrino EK
- 78.46.167[.]130 port 80 - vxovtphxu.llxfqt[.]xyz - Neutrino EK
- 78.46.167[.]130 port 80 - poyuw.kpigmq[.]xyz - Neutrino EK
- 93.115.10[.]203 port 80 - sievavower[.com - Gootkit post-infection SSL/TLS traffic over port 80
- 52.67.39[.]104 port 80 - stogtetch[.]com] - Gootkit post-infection SSL/TLS traffic over port 80
- 93.115.10[.]203 port 443 - Gootkit post-infection SSL/TLS traffic
- 74.208.147[.]184 port 80 - condir.lenderconvey[.]com - pseudoDarkleech campaign Neutrino EK
- 185.49.68[.]215 port 443 - CryptXXX ransomware callback traffic
- 93.114.65[.]96 port 80 - ac84[.]ro - gate leading to Rig EK
- 46.30.43[.]38 port 80 - ds.naviforedtech[.]com - Rig EK (probably sent Tofsee payload)
IMAGES
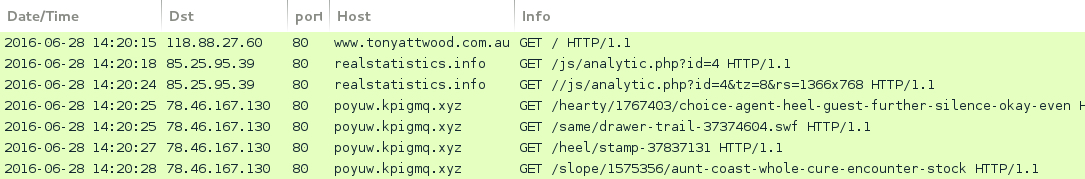
Shown above: Traffic from the first pcap filtered in Wireshark.
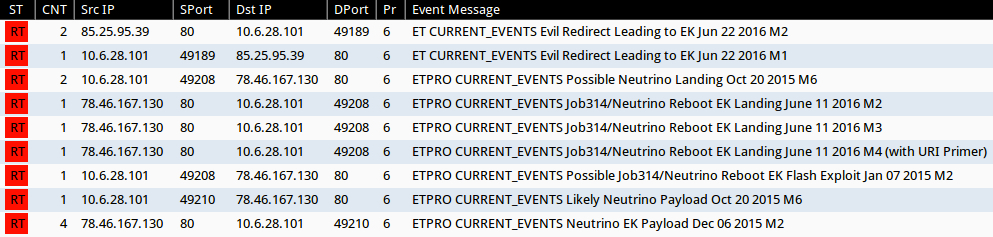
Shown above: Alerts in Sguil after using tcpreplay on the first pcap in Security Onion with Suricata and the EmergingThreats Pro ruleset.
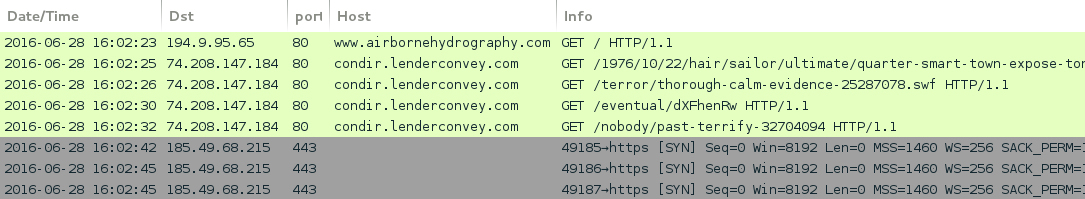
Shown above: Traffic from the second pcap filtered in Wireshark.
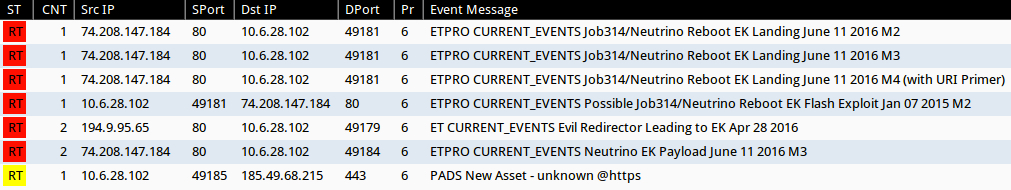
Shown above: Alerts in Sguil after using tcpreplay on the second pcap in Security Onion with Suricata and the EmergingThreats Pro ruleset.
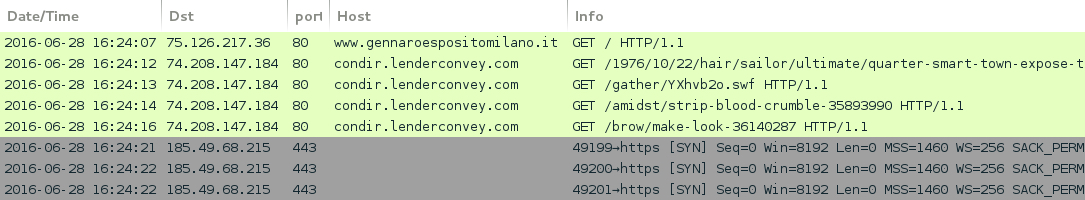
Shown above: Traffic from the third pcap filtered in Wireshark.
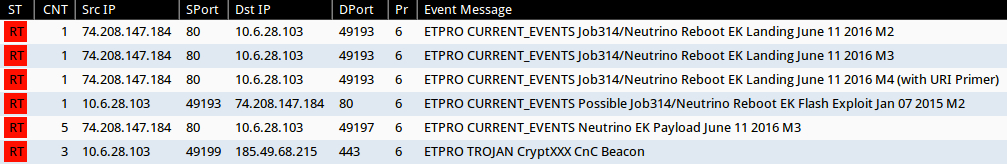
Shown above: Alerts in Sguil after using tcpreplay on the third pcap in Security Onion with Suricata and the EmergingThreats Pro ruleset.
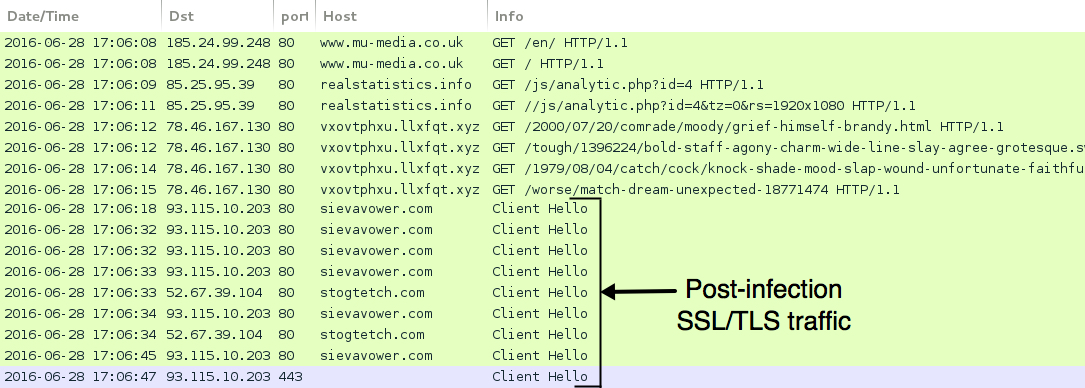
Shown above: Traffic from the fourth pcap filtered in Wireshark.
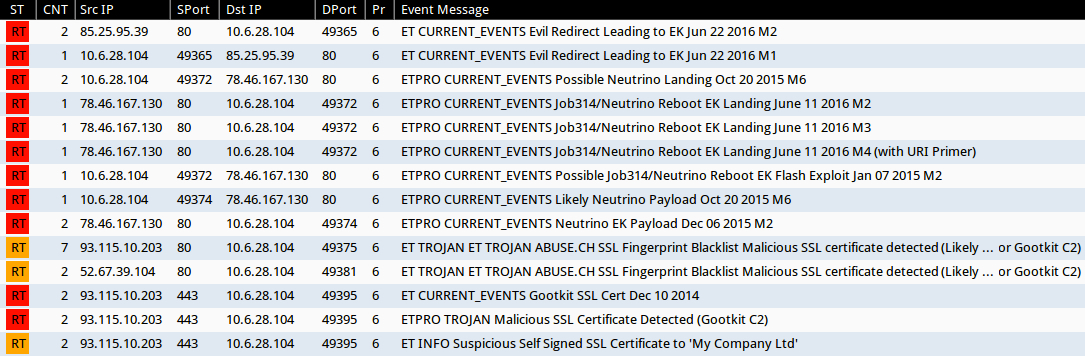
Shown above: Alerts in Sguil after using tcpreplay on the fourth pcap in Security Onion with Suricata and the EmergingThreats Pro ruleset.
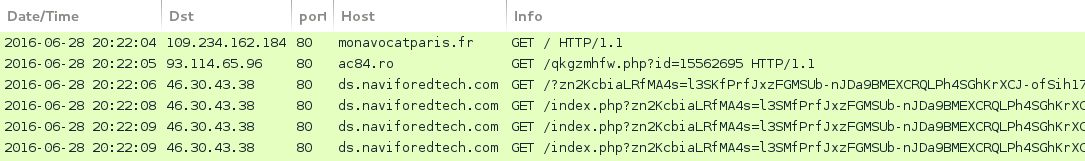
Shown above: Traffic from the fifth pcap filtered in Wireshark.
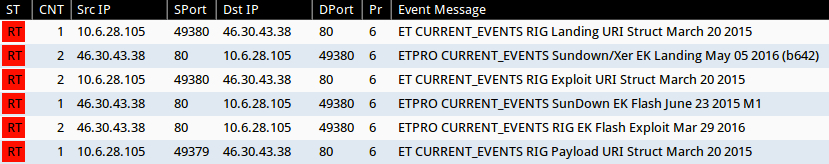
Shown above: Alerts in Sguil after using tcpreplay on the fifth pcap in Security Onion with Suricata and the EmergingThreats Pro ruleset.
Click here to return to the main page.
